الغوص العميق: كيف يفتح التشفير المتماثل بالكامل الباب أمام حالات استخدام جديدة للذكاء الاصطناعي
Original author: 0x Todd, co-founder of Ebunker (X: @0x_Todd)
The market has been bad recently, and I finally have some time to continue sharing some new technical routes. Although the encryption market in 2024 is not as turbulent as in the past, there are still some new technologies trying to mature, such as the topic we are going to talk about today: FHE / Fully Homomorphic Encryption.
V God also published an article specifically about FHE in May this year, and recommends it to friends who are interested.
So what exactly is FHE?
To understand the difficult term FHE fully homomorphic encryption, you must first understand what encryption, what homomorphic is, and why full is needed.
1. What is encryption?
Ordinary encryption is the most familiar to everyone. For example, Alice wants to send a message to Bob, such as 1314 520.
If we want a third party C to send the message and keep the information confidential, it is very simple – just encrypt each number by x2, for example, to 2628 1040.
When Bob received it, he divided each digit by 2 and decrypted it to find out that Alice was saying 1314 520.
See? The two people completed the information transmission through symmetric encryption, without asking C to help but without C knowing the information. Generally, in spy movies, the communication between two liaisons will not exceed this scope.
2. So what is homomorphic encryption?
Now Alices requirements have been upgraded:
-For example, Alice is only 7 years old;
-Alice can only do simple arithmetic such as x 2 and ÷ 2, and she doesnt understand any other operations.
OK, now lets assume that Alice has to pay the electricity bill. Alices monthly electricity bill is 400 yuan, and it has been in arrears for 12 months.
However, 400*12=how much? This problem is beyond the calculation range of Alice, who is only 7 years old. She cannot do such complicated calculations.
However, she does not want others to know how much her electricity bill is/how many months because it is sensitive information.
Therefore, Alice asks C to help with the calculation without trusting C.
Because she only knows x 2 ÷ 2, she uses x 2 multiplication to simply encrypt her number. Then, she tells C to calculate what 80 0x 24 = is, that is: (40 0x 2) times (12 x 2).
C is an adult with a strong computing brain. He quickly calculated 800*24 = 19200 and told Alice the number. Then, Alice used the result, which is 19200 ÷ 2 ÷ 2, and soon realized that she had to pay 4,800 yuan for water.
Did you see it? This is the simplest multiplication homomorphic encryption. 800*24 is just a mapping of 400*12. The shape before and after the transformation is actually the same, so it is called homomorphic.
This encryption method makes it possible for someone to entrust an untrusted entity to calculate the results while ensuring that their sensitive numbers are not leaked.
3. Then why does “homomorphic encryption” need to be “complete”?
However, the problems just now only exist in an ideal world. Problems in the real world are not that simple. Not everyone is 7 years old, or as honest as C.
Lets assume a very bad situation, for example, C may try to reverse the process, and C can also decipher that Alice wants to calculate 400 and 12 through brute force method.
At this time, fully homomorphic encryption is needed to solve the problem.
Alice multiplies each number by 2, and this 2 can be regarded as noise. If the noise is too small, it is easy for C to crack it.
Therefore, Alice can introduce an addition based on multiplication.
Of course, it would be best if the noise was like a main road intersection at 9 a.m., in which case cracking C would be harder than climbing to the sky.
Therefore, Alice can multiply 4 times and add 8 times, which greatly reduces the probability of C being cracked.
However, Alice is still only partially homomorphically encrypted, that is:
(1) Her encrypted content can only address certain issues;
(2) She can only use a specific set of operation rules because the number of additions and multiplications cannot be too many (generally no more than 15).
Full means that Alice should be allowed to perform addition encryption and multiplication encryption any number of times for a polynomial, so that she can entrust a third party to perform complete calculations and still get the correct result after decryption.
A super long polynomial can express almost all mathematical problems in the world, not just problems that 7-year-olds can solve, such as calculating electricity bills.
Coupled with any number of encryptions, it is almost impossible for C to snoop on private data, truly achieving both.
Therefore, the technology of fully homomorphic encryption has always been a jewel in the holy grail of cryptography.
In fact, homomorphic encryption technology only supported partial homomorphic encryption until 2009.
The new idea proposed by Gentry and other scholars in 2009 opened the door to the possibility of fully homomorphic encryption. Interested readers can also refer to this paper.
Many friends still have doubts about the application scenarios of this technology. In what scenarios will the fully homomorphic encryption (FHE) technology be needed?
For example – AI.
As we all know, a powerful AI needs enough data to be fed, but the privacy value of a lot of data is too high. So can FHE achieve both?
The answer is yes.
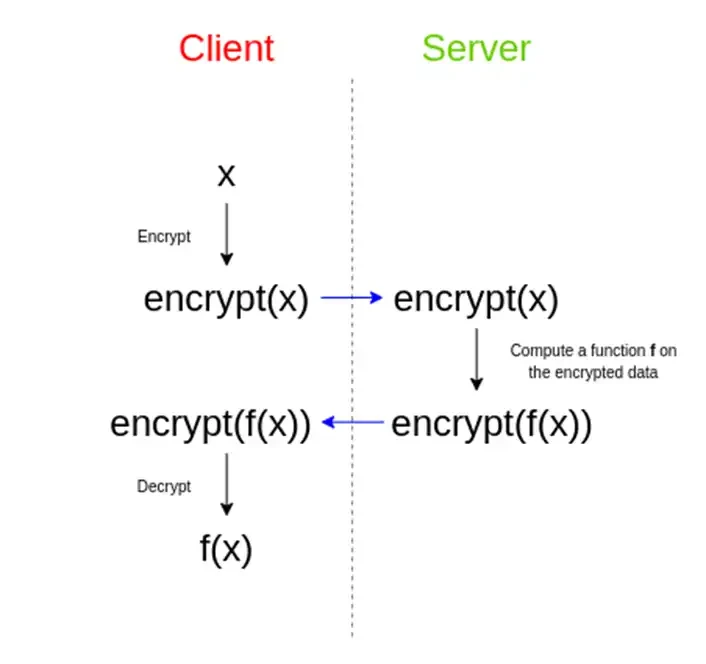
you can:
(1) Encrypt your sensitive data using FHE;
(2) Use the encrypted data to perform AI calculations;
(3) Then the AI spits out a bunch of gibberish that no one can understand.
Unsupervised AI can achieve this because the data is essentially vectors. AI, especially generative AI such as GPT, does not understand the words we input to it at all. It just predicts the most appropriate answer through the vector.
However, since this mess of code follows some mathematical rules, and you are the one who encrypted it, then:
(4) You can disconnect from the network and decrypt the garbled code locally, just like Alice did;
(5) Furthermore, you have achieved the following: AI uses its massive computing power to help you complete the calculation without having to touch your sensitive data at all.
But current AI cannot do this, and must give up privacy. Think about everything you input to GPT in plain text! To achieve this, FHE is indispensable.
This is the root of the natural fit between AI and FHE, and thousands of words can be summed up in one word: both.
Since FHE is linked to AI and spans the two major fields of encryption and AI, it naturally receives extra favor. There are many FHE projects, such as Zama, Privasea, Mind Network, Fhenix, Sunscreen, etc., and the application directions of FHE are also creative.
Today, I will analyze one of the projects, @Privasea_ai, which is a FHE project led by Binance. Its white paper describes a very relevant scenario, such as face recognition.
Both: the machine computing power must be able to determine whether this person is a real person;
Another requirement: The machine does not handle any sensitive facial information.
The introduction of FHE can effectively solve this problem.
However, if you really want to do FHE calculations in the real world, you need a huge amount of computing power. After all, Alice needs to do arbitrary addition and multiplication encryption. Whether it is calculation, encryption, or decryption, it is a process that consumes a lot of computing power.
Therefore, Privasea needs to build a powerful computing network and supporting facilities. Therefore, Privasea has proposed a PoW+PoS network architecture to solve the problem of computing network.
Recently, Privasea just announced its own PoW hardware, called WorkHeart USB, which can be understood as one of the supporting facilities of Privaseas computing network. Of course, you can simply understand it as a mining machine.
The initial price is 0.2 ETH, which can mine 6.66% of the total tokens of the network.
There is also a PoS-like asset called StarFuel NFT, which can be understood as a work certificate, with a total of 5,000.
The initial price is also 0.2 ETH, and you can get 0.75% of the total tokens of the network (through airdrop).
This NFT is also interesting. It is similar to PoS, but not true PoS. It tries to avoid the question of Is PoS a security in the United States?
This NFT supports users to pledge Privasea tokens into it, but it does not directly generate PoS income. Instead, it doubles the mining efficiency of your bound USB device, so it is a disguised PoS.
Back to the topic, if AI can really popularize FHE technology on a large scale, it will be a blessing for AI itself. You know, many countries now focus on data security and data privacy when regulating AI.
Even, to give an inappropriate example, in the Russia-Ukraine war, some Russian military personnel tried to use AI, but considering the American background of many AI companies, the intelligence agencies would probably be riddled with holes.
But if we don’t use AI, we will naturally fall behind. Even if the gap is not big now, in another 10 years, we may not be able to imagine a world without AI.
Therefore, data privacy is everywhere in our lives, from major issues such as war and conflict between two countries to minor issues such as facial unlocking on mobile phones.
In the era of AI, if FHE technology can truly mature, it will undoubtedly be the last line of defense for mankind.
This article is sourced from the internet: Deep Dive: How Fully Homomorphic Encryption Unlocks New Use Cases for AI
Related: Early-stage potential projects that must be participated in this week: Movement, WORLD3
Original | Odaily Planet Daily ( @OdailyChina ) Author | Asher ( @Asher_0210 ) Since the ZKsync and LayerZero airdrops, many people have said that the era of scalping is over. Coupled with the sluggish market in the past two weeks, the communitys enthusiasm for scalping has dropped to a low point. It is true that the era of achieving financial freedom by mindlessly signing up for airdrops is gone forever, but as the definition of high-quality accounts becomes more and more stringent, retail investors have become an entry point to understand high-finance or popular projects by scaling in a short period of time. Odaily Planet Daily has compiled two projects worth participating in this week based on financing status, project popularity and other aspects. Movement: Building the first L2…