يدق جرس الإنذار مرة أخرى بشأن أمن الأصول المتداولة. كيف تبني Gate.io بوابة حماية قوية؟
الأصل|Odaily Planet Daily
المؤلف: فينسر

As a hard-hit area for hacker attacks, the cryptocurrency industry has frequent security incidents. According to CertiK Alert يراقب , the total loss of the cryptocurrency industry in the first half of June alone was as high as 85 million US dollars, of which the UwU Lend protocol suffered a total loss of more than 22 million US dollars. From the beginning of the year to the beginning of June, the cryptocurrency industry has lost about 821 million US dollars . Previously, several leading exchanges and users in the industry have also suffered security attacks and asset losses to varying degrees, and cryptocurrency exchanges are a high-incidence area for digital asset security incidents. In this regard, the cryptocurrency exchange Gate.io, which was established in 2013, has always been in the first echelon of the industry. Its unique security strategies such as binding IP and internal and external dual security measures have built a digital asset security protection gate for many users. Today, let us walk into Gate.ios multi-security protection system together.
Security issues have become a chronic problem in the industry, and positioning issues are the key
As we enter 2024, the cryptocurrency industry is still facing the chronic disease of security risks.
In February 2024, a Hong Kong cryptocurrency exchange BF lost approximately US$56.5 million in assets; in April, a Middle Eastern cryptocurrency exchange lost US$14.8 million in an attack; in May, a leading Japanese cryptocurrency exchange تم اختراقه , 4,502.9 bitcoins were stolen, and the loss amounted to US$305 million; in June, a British cryptocurrency exchange stopped trading after losing US$22 million due to a security incident , and then closed two days after the hacker attack; a Turkish cryptocurrency exchange issued a notice stating that the platform was attacked by a cyber attack on June 22, affecting the hot wallet assets of 10 cryptocurrencies.
Looking back at the past, the link where positioning problems arise may be more critical. Specifically, the main problems in the industry currently include the following three aspects:
First, on the exchange side: some exchanges have loopholes in risk control management mechanisms, lack of encryption insurance mechanisms for user data management, lack of disaster recovery backup or problems with access permission management. In addition, the single asset storage method is also an important reason for the frequent occurrence of digital asset security incidents in exchanges;
Secondly, on the user side: the natural anonymity mechanism of the blockchain network and the complex and high-risk network environment provide convenience for hackers or attackers, and the lack of awareness of asset security management is also the main reason for the damage of cryptocurrency assets. Not only that, some users with huge wealth are also facing various risks in offline physical space, and their personal and property safety are threatened, and thousands of people with thousands of faces social engineering attacks are also waiting in the dark, eyeing their digital assets;
Finally, on the security company side: Although the cryptocurrency industry has a history of more than 10 years, it has not yet established a relatively complete white hat hacker mechanism. The lack of a security vulnerability feedback mechanism with unclear responsibilities makes it difficult for many problems to be handled and solved in a timely manner. Some time ago, the cryptocurrency exchange Kraken and the security company Certik had a big fight over security vulnerabilities and feedback mechanisms. For details, please refer to the article CertiK vs. Kraken: What is the appropriate scale for white hat hackers? issued by Odaily Planet Daily.
Exchange hacking incidents are frequent. How does Gate.io solve the problem?
It can be seen that as an important flow node of digital assets, exchanges are subject to the most direct and fierce security attack test. As a veteran exchange founded in 2013, Gate.io has also gained the trust and support of many loyal users with its continuous technical product updates, risk prevention and control management, and fast and convenient trading system. It is مفهومة that Gate.io currently has more than 16 million users worldwide and supports more than 2,200 cryptocurrencies. As one of the mainstream exchanges in the market, it provides many users with a variety of cryptocurrency trading options.
To deal with hacker attacks, financial strength and 100% reserve funds that are both transparent and secure are the most basic parts of the user asset security system.
In view of this, as an exchange that always adheres to making full preparations for the security of users digital assets, Gate.io has long been committed to compliance and transparency as early as 2020, before FTX, the second largest exchange in the cryptocurrency industry, went bankrupt in 2022 due to a liquidity crisis. It has become one of the first exchanges in the industry to promise that users can verify the proof of reserves, making it convenient for each user to independently verify whether all types of digital assets under it are held in a 1:1 ratio. For details, please refer to the reserve audit proof interface of the Gate.io official website . Gate.io also regularly issues 100% reserve reports to ensure that user assets will not be maliciously misappropriated or other security issues will occur.
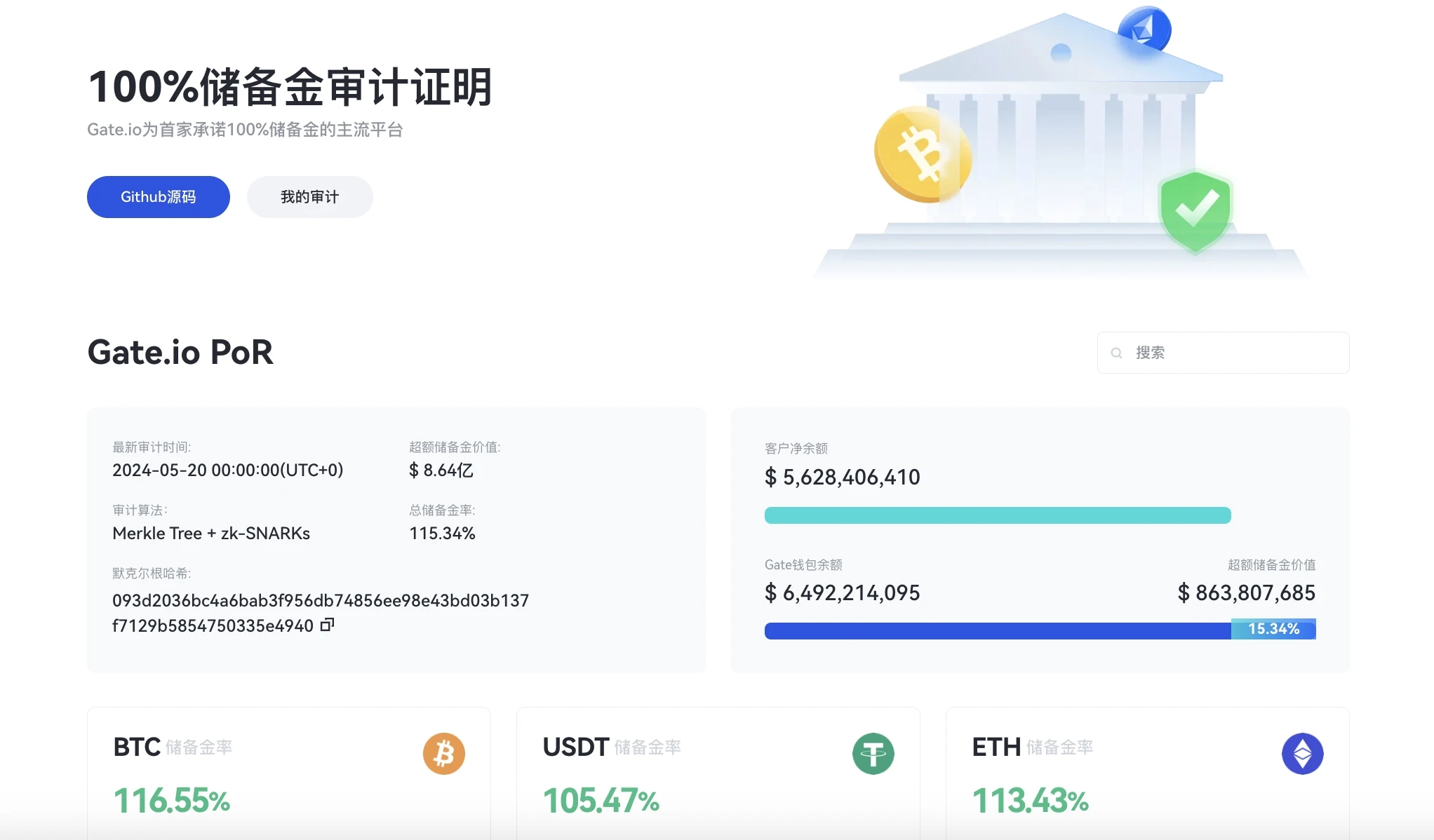
Gate Reserve Audit Interface
In terms of specific asset security management, Gate.ios efforts are obvious to all.
Gate.ios multiple protection strategies build a solid security gate for digital assets
It is worth mentioning that due to the frequency and complexity of security incidents in the industry, Gate.io did not focus on just one or several links, but worked hard to build a digital asset security protection system based on multiple protection strategies.
For the exchange side
In the past, the security issues of crypto exchanges mainly arose in the asset storage link. In response to this, Gate.io protects user assets through a dual storage solution that combines online and offline solutions, leveraging the physical protection advantages of cold wallets and the encryption protection features of hot wallets to achieve high confidentiality of asset storage.
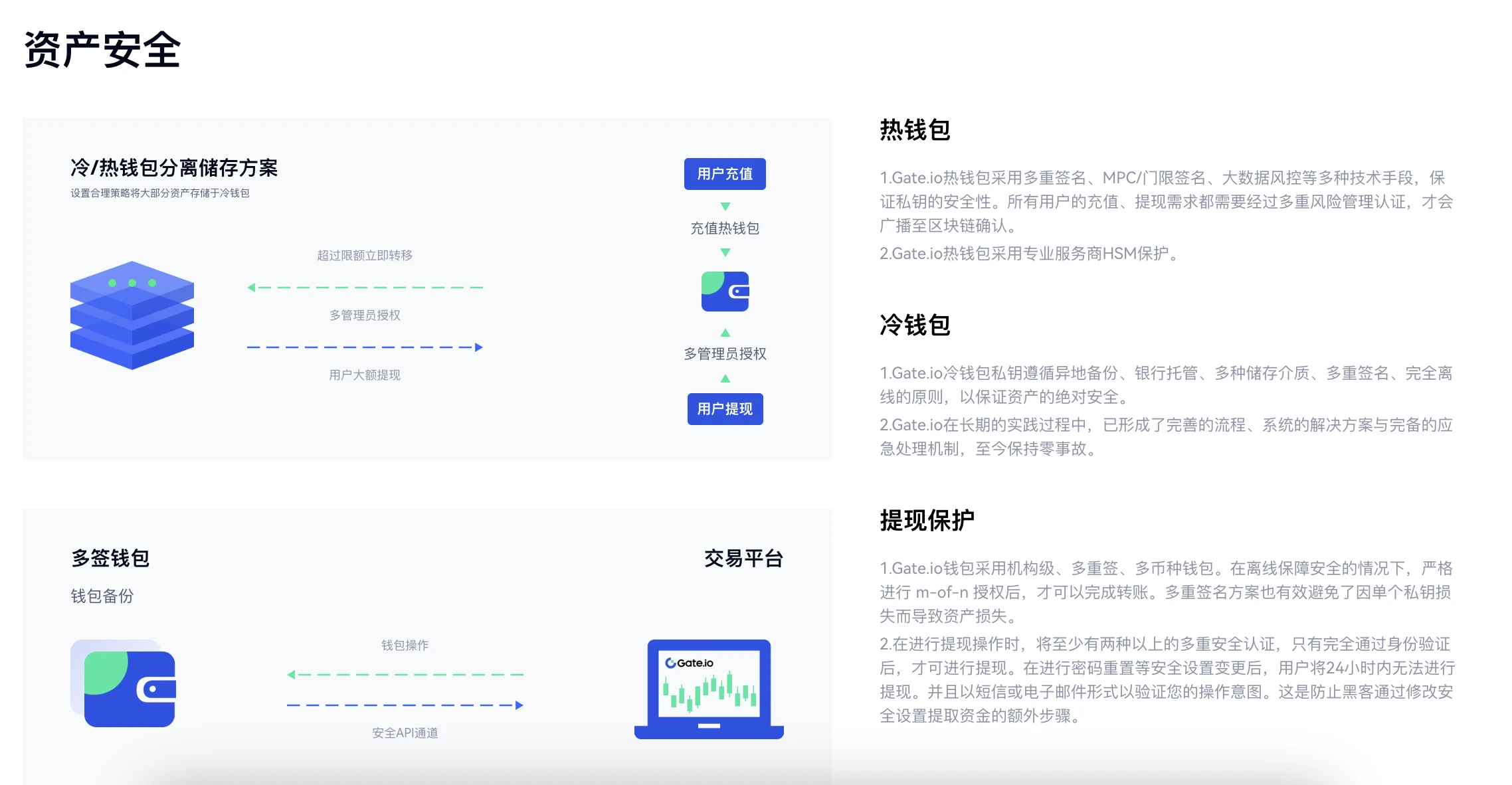
Gate.io Asset Security Instructions
In addition, the effective combination of advanced encryption technology, cloud security protection, anti-DDoS measures, solid DNS security and Web application firewall also provides sufficient protection against external threats.

Gate.io Platform Security Introduction
For the user side
For users who have occasional and asynchronous security issues, Gate.io has prepared a series of comprehensive security infrastructures to protect the account assets of platform users through multi-level security mechanisms. Every operation step on the platform involving digital interfaces or physical levels runs smoothly under the protection of corresponding security facilities. Specifically, it mainly involves the following links:
1. Gate.io’s original “Bind IP” feature: It is recommended that users select “Bind to IP address” when logging into an exchange account. This feature protects the user’s current login session from being hijacked by unauthorized networks, and the account is only available on Gate.io.
2. Setting of fund operation isolation password: Users can set an independent fund password to verify transactions and withdraw assets. Note: This password should be distinguished from the login password to avoid being the same as the login password, so as to prevent unauthorized transactions.
3. Enable 2FA two-factor authentication: Users can use other two-factor authentication (2FA) tools such as Google Authenticator or YubiKey to set up login security, and add additional security protection to the account login process through multiple authentication forms (such as plain text password + authenticator).
4. Enable anti-phishing passwords for emails: Users should enable settings such as anti-phishing passwords to effectively address fraudulent emails, strengthen phishing email detection, and send anti-counterfeiting emails through the Gate.io official email account to help users receive real emails and identify fraudulent emails, thereby solving the risk of clicking on scam links from the source.

Gate.io Account Security Instructions
All of the above security features have been recognized and supported by senior security professionals in the industry, and their protection effects have been verified many times in many practical application scenarios. It is particularly worth mentioning that IP binding, as a security strategy pioneered by Gate.io, effectively prevents unauthorized IP addresses from accessing user accounts, further improving the security of user assets. For more detailed introductions to the Gate.io solution, please refer to its الموقع الرسمي .
In addition, Gate.io has also specifically built a top internal security expert team in the industry to safeguard user rights and interests based on risk management strategies and ensure that users digital assets receive the highest level of protection.
For security companies
In order to identify and fill gaps in the internal security protection system, and to complete the early detection of security risks and the elimination of potential threats as soon as possible, Gate.io has also formed a diversified professional team composed of senior security experts and external auditors to conduct rigorous testing and inspections on the various components of the platform from time to time to complete the last piece of the puzzle in the security protection system.
In addition, Gate.io has also reached a long-term cooperation with the well-known blockchain security company Hacken. The cooperation includes annual security assessments, penetration testing, and bug bounty programs, providing white hat hackers and anonymous security personnel with a complete security vulnerability feedback mechanism and sufficient incentive bounties, truly achieving the coordination of internal and external security protection. At the beginning of this year, Gate.ios reserve plan also passed Hackens security review, which highly praised the good balance between functionality and complexity achieved by Gate.ios reserve plan.
Asset security is a pain point for users and the bottom line of the industry
After experiencing the early development pains of the industry in 2014 and 2015, Gate.io has been active in many mainstream crypto exchanges with a new look. It has been following up and supporting many early high-quality assets, innovative trading protocols, and investment targets with high market popularity. Therefore, it is affectionately called Open Sesame by many users, implying that Gate.io is like the magic door that appears after chanting a spell, and has the magical power to influence the market on some level. According to official data, Gate.ios annual transaction volume in 2023 reached 1.72 trillion US dollars, with more than 360 new currencies added throughout the year, more than 7 million people have participated in the subscription of new Startup projects, the scale of Sesame Finance users has reached one million, and the total amount of funds has exceeded 768 million USDT.
Now, after the historic 11th anniversary, Gate.io has achieved long-term stable development in maintaining the security of user assets and ensuring the stable operation of platform asset transactions with a consistent responsible attitude and patience. With the slogan of Opening the era of all-round trading, Gate Group has established local sites in Malta, Hong Kong, Lithuania, Turkey and other regions, which also highlights the next development focus of globalization.
During this process, asset security, as a user pain point and industry bottom line issue, still has a long way to go. After all, the formation of a secure, open, and decentralized blockchain world requires efforts and support from multiple parties. I believe that Gate.io is happy to play a more proactive role as a builder in this process.
As the old saying goes, “The road may be long, but if you keep walking you will reach your destination; the task may be difficult, but if you keep doing it you will succeed.”
Gate.io is on the road to build a solid security protection gate.
This article is sourced from the internet: The alarm bell for exchange asset security rings again. How does Gate.io build a solid protective gate?
Original author: Alex Liu, Foresight News The Aptos public chain was created by some members of Facebooks former blockchain team Diem after independence, raising a total of up to $350 million in funds. After a large airdrop on the test network, the Aptos main network has been online for more than a year and a half, and the ecological projects are becoming increasingly mature, but most of them have not yet issued coins. How can we layout to kill two birds with one stone and maximize the benefits of the interactive Aptos ecosystem? This article takes stock of the main potential projects of the ecosystem and gives a detailed interaction path. Among the top 5 protocols in the Aptos ecosystem by TVL on DefiLlama, only Thala has issued tokens Potential…







