Final chapter of the security special issue | OKX Web3: Safeguarding user assets
Introduction: OKX Web3 has specially planned the Security Special Issue column to answer different types of on-chain security issues. Through the most real cases happening around users, in collaboration with experts or institutions in the security field, dual sharing and answers from different perspectives are conducted, so as to sort out and summarize the rules of safe transactions from the shallow to the deep, aiming to strengthen user security education while helping users learn to protect their private keys and wallet assets from themselves.
Thank you for your company all the way~
Finally! The Security Special Issue series initiated by the OKX Web3 Wallet Security Team has come to an end~
Don’t put it in your favorites and let it gather dust! Don’t wait a while to learn it either!
The safety of your wallet and assets is no small matter, you must keep it in mind~
1. Content Review
First of all, I would like to express my sincere gratitude to guests in the security field such as SlowMist, CertiK, WTF Academy, OneKey, BlockSec and GoPlus for their joint support for this series of content. We started with the most real cases happening around users and sorted out the risk types, advanced tools, safety rules, protection suggestions, etc. in different scenarios.
Looking back at the entire series, it has covered 6 popular scenarios in the field of cryptographic security, including private key security, MEME transaction security, money laundering security, device security, and DeFi security. While aiming to strengthen user security education, it also hopes to help users learn to protect their private keys and wallet asset security from themselves. Users can read on demand:
Security Special Issue 01 | OKX Web3 SlowMist: Sharing Experience of “Hundreds of Scams”
Security Special Issue 02 | OKX Web3 CertiK: MEME Big Adventure and Security Truth
Security Special Issue 04 | OKX Web3 OneKey: Add some buff to device security
Security Special Issue 06 | OKX Web3 GoPlus: On-chain security monitoring and post-event rescue
In general, current security incidents are characterized by diversity, concealment, and complexity, but most of them are caused by users having their private keys or mnemonics stolen or induced to enter, such as fake airdrops, fake websites, fake customer service, etc. Therefore, you must always be vigilant, do not easily click on unfamiliar links, leak information to strangers, enter unfamiliar websites, etc., and do not easily leak your private keys and mnemonics.
Please remember: in the encrypted world, safety comes first.
2. Latest security updates of OKX Wallet
Secondly, as a self-hosted wallet, the private keys and assets of the OKX Web3 wallet are completely controlled by the user. The OKX Web3 wallet will protect the security and privacy of users 24/7. So we will share some OKX Web3 wallet security updates with you in the final chapter.
Currently, OKX Web3 wallet has officially launched the Security Center, which users can access by clicking the relevant banner on the Web3 wallet webpage, or by clicking: https://www.okx.com/zh-hans/web3/security? source=gtm. The center covers five major aspects, including code open source, multi-party audit, and bug bounty program, and supports public verification by users, aiming to create a safer Web3 ecosystem.
First, in terms of multi-party auditing, the security standards of OKX Web3 Wallet have been tested and verified by third-party security auditing companies. The audit reports of SlowMist and Certik are now public and users can view them at any time. In the future, OKX Web3 Wallet will continue to be regularly audited by reputable security auditing companies to ensure asset security.
Second, in terms of open source code, the OKX Web3 wallet has completed the open source of its core code, including mnemonics, private keys, MPC and other core algorithms, which have been widely verified by the technical community. The implementation details are open to users for free viewing and auditing on GitHub, making it more open and transparent.
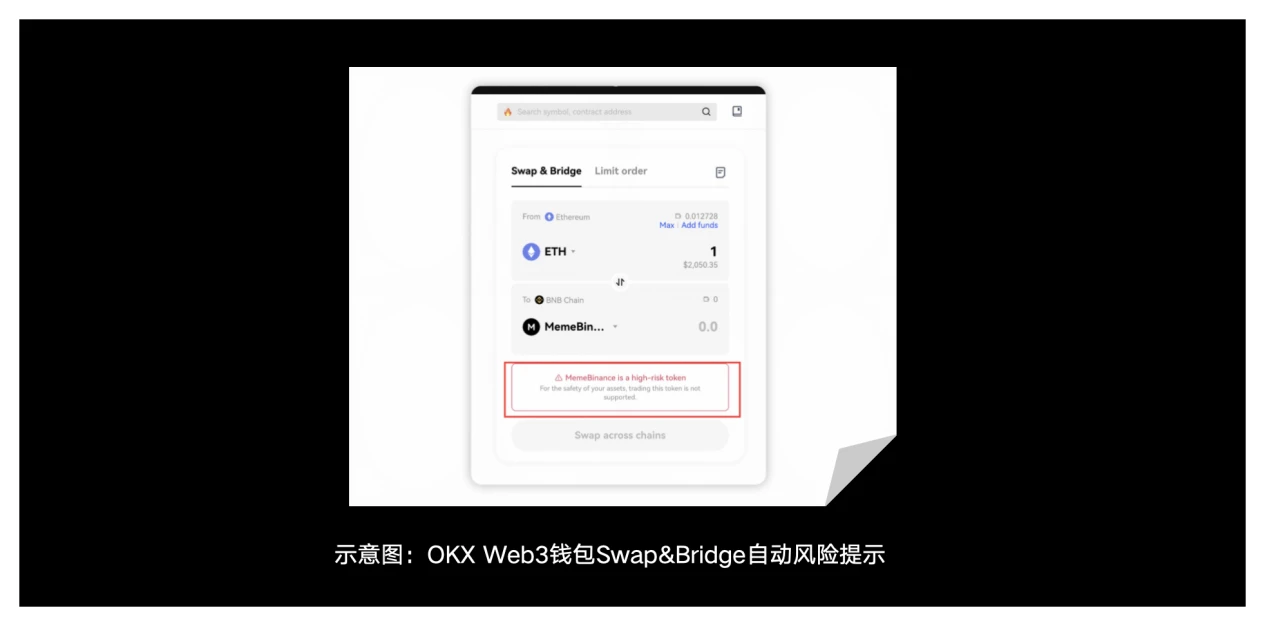
Third, in terms of intercepting third-party risks, the OKX Web3 wallet can help users filter high-risk tokens and domain names and protect their assets from threats by providing powerful security monitoring. So far, it has intercepted 153K+ malicious domain names, 1.5M+ similar domain names, 1.28M+ high-risk tokens, and 153K+ high-risk transactions for users.
Fourth, the OKX Web3 wallet has also launched a bug bounty program to encourage users and developers to submit service errors and security vulnerabilities, and has prepared generous bug bounties to work with users to build wallet security.
While redefining the wallet experience, the OKX Web3 wallet protects the security of users assets and strives to protect users so that they can embark on their on-chain exploration journey more safely.
3. 7 x 24 hours security escort
As the industrys leading one-stop Web3 portal, OKX Web3 Wallet provides 24/7 security protection for user assets, such as:
1. In terms of private key security
To ensure the security of the users wallet private key, the entire underlying system of the OKX Web3 wallet is not connected to the Internet. The users mnemonic and private key related information are all encrypted and stored locally on the users device. The relevant SDK is also open source and has been widely verified by the technical community, making it more open and transparent. In addition, the OKX Web3 wallet has also conducted strict security audits through cooperation with well-known security organizations such as SlowMist.
In addition, in order to better protect our users, the OKX Web3 security team has provided strong security protection for private key management and is continuously iterating and upgrading. Here is a brief sharing:
1) Two-factor encryption. Currently, most wallets usually use a password to encrypt the mnemonic and save the encrypted content locally. However, if the user is infected with a Trojan virus, the Trojan will scan the encrypted content and monitor the password entered by the user. If the scammer monitors it, the encrypted content can be decrypted to obtain the users mnemonic. In the future, the OKX Web3 wallet will use a two-factor method to encrypt the mnemonic. Even if the scammer obtains the users password through the Trojan, he will not be able to decrypt the encrypted content.
2) Private key copying security. Most Trojans will steal information from the users clipboard when the user copies the private key, resulting in the leakage of the users private key. We plan to help users reduce the risk of private key information theft by increasing the security of the users private key copying process, such as copying part of the private key and clearing the clipboard information in time.
2. At the level of APP data security
OKX Web3 Wallet uses a variety of methods to reinforce the App, including but not limited to algorithm obfuscation, logic obfuscation, code integrity detection, system library integrity detection, application tamper-proofing, and environmental security detection. These methods minimize the probability of users being attacked by hackers when using the App. At the same time, they can also prevent the black industry from repackaging our App to the greatest extent, reducing the probability of downloading fake Apps.
In addition, in terms of Web3 wallet data security, we use the most advanced hardware security technology and chip-level encryption to encrypt sensitive data in the wallet. The encrypted data is bound to the device chip. If the encrypted data is stolen, no one can decrypt it.
3. At the level of third-party testing
We provide many security mechanisms to protect user funds:
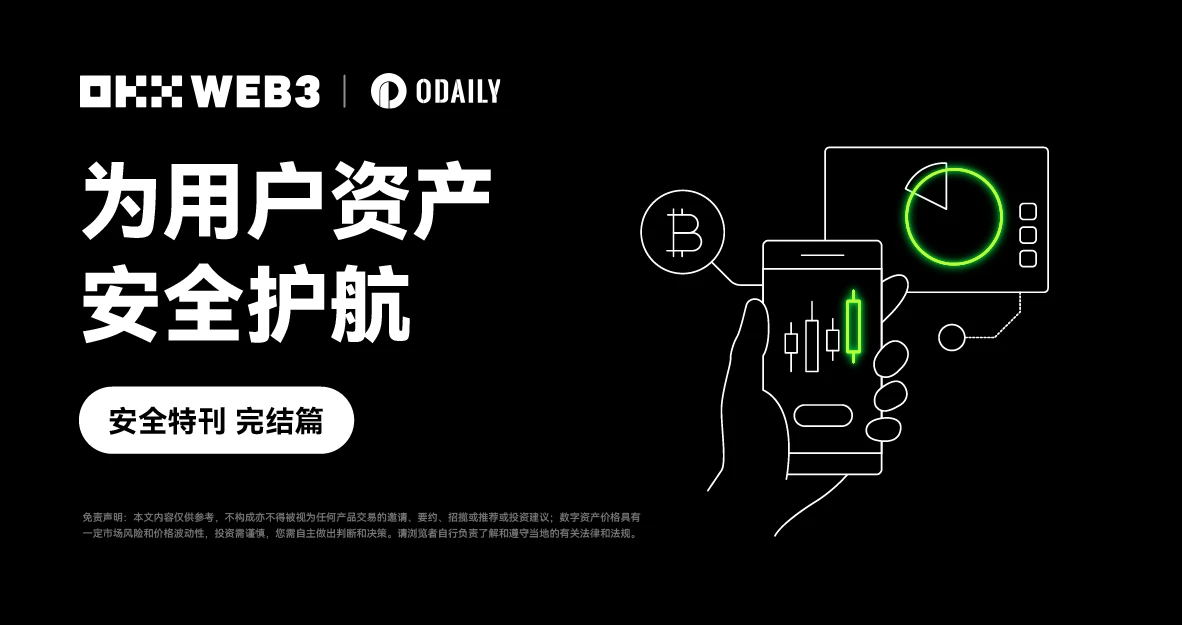
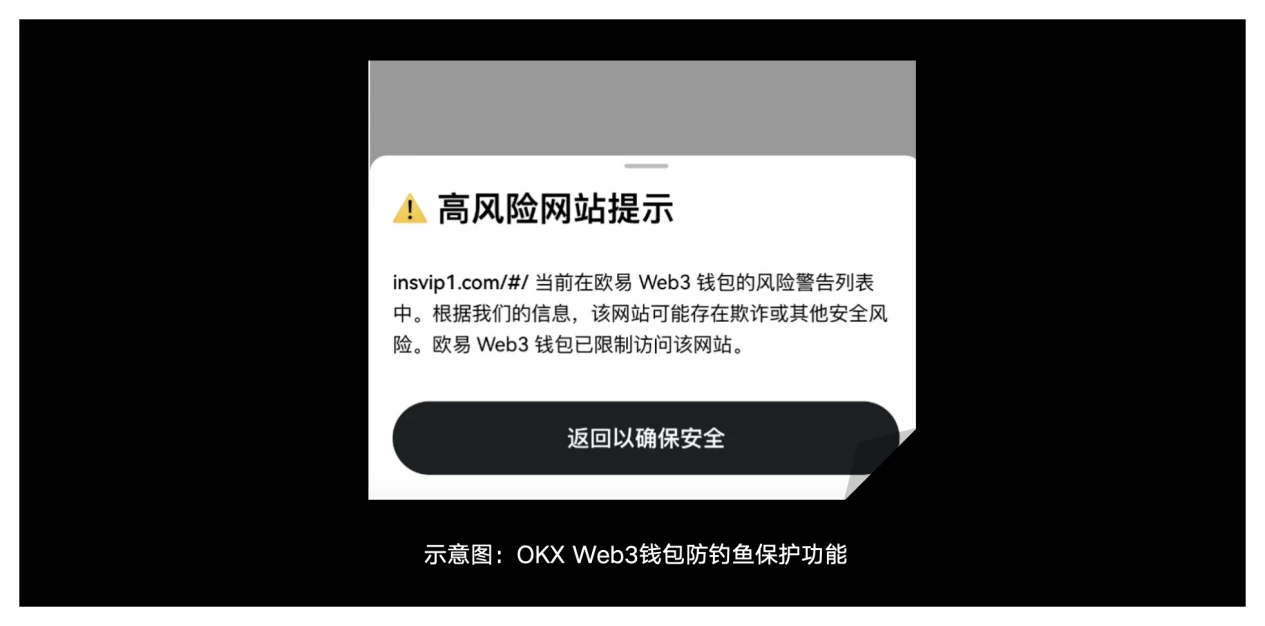
1) Risky domain name detection: When a user accesses a DAPP, the OKX Web3 wallet will perform detection and analysis at the domain name level. If the user accesses a malicious DAPP, it will be intercepted or reminded to prevent the user from being deceived.
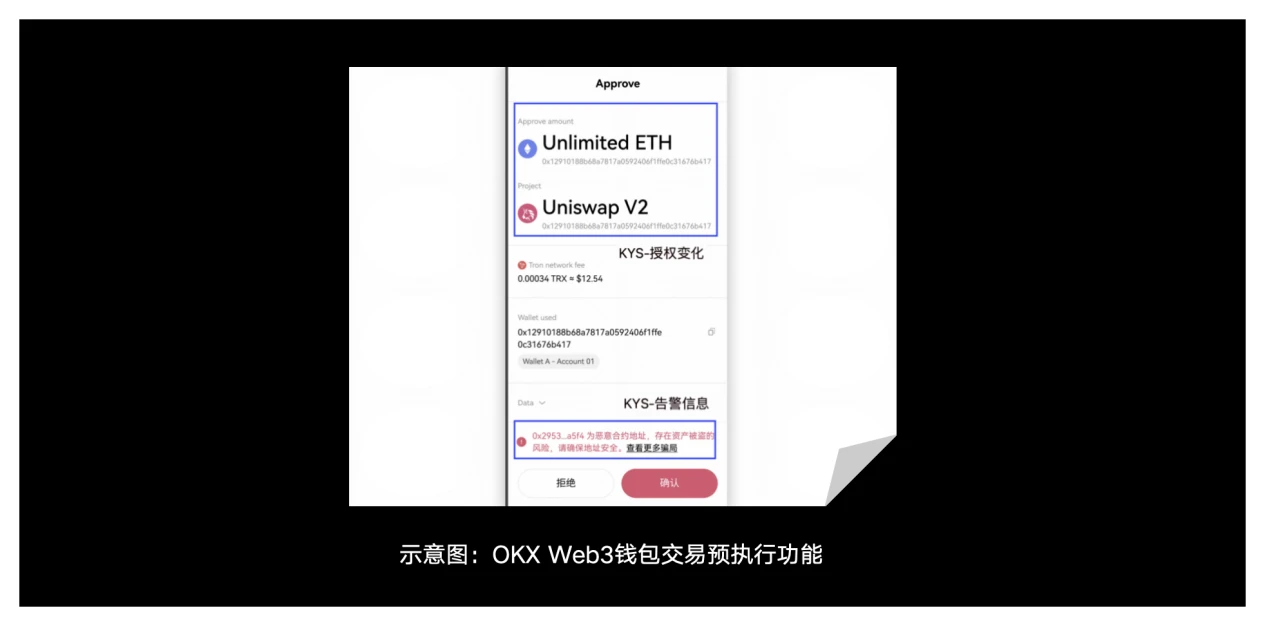
2) Pixiupan token detection: OKX Web3 wallet supports comprehensive Pixiupan token detection capabilities, actively blocking Pixiupan tokens in the wallet to prevent users from trying to interact with Pixiupan tokens.
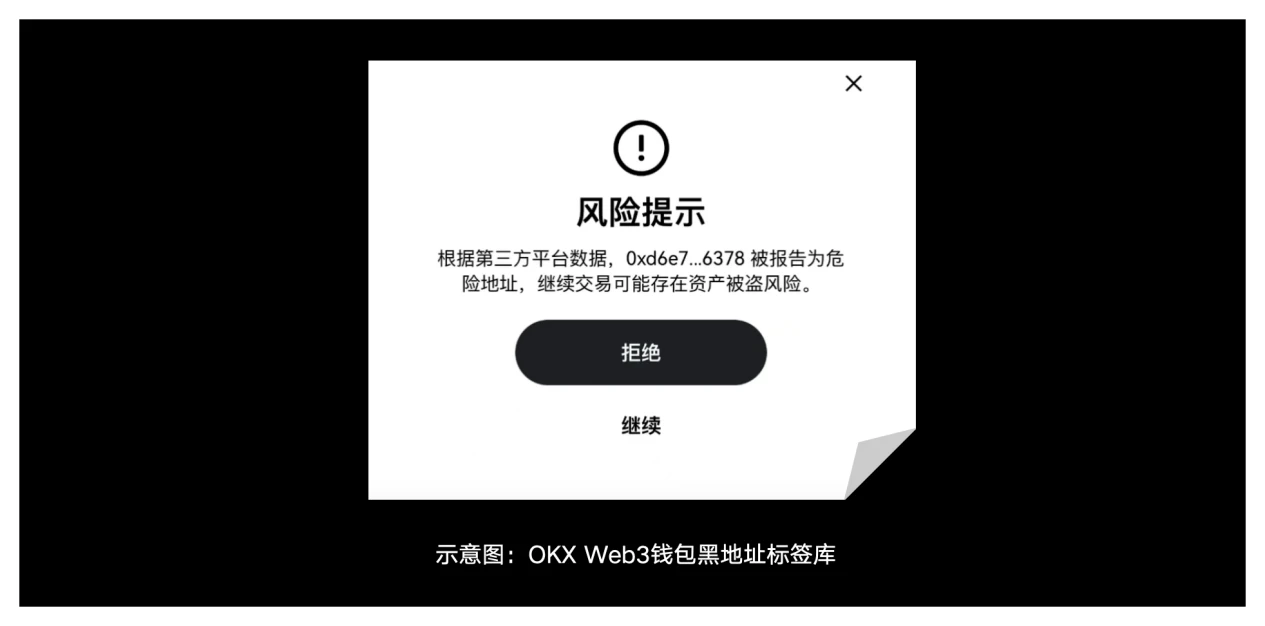
3) Address tag library: OKX Web3 wallet provides a rich and complete address tag library. When users interact with suspicious addresses, OKX Web3 wallet will give timely warnings.
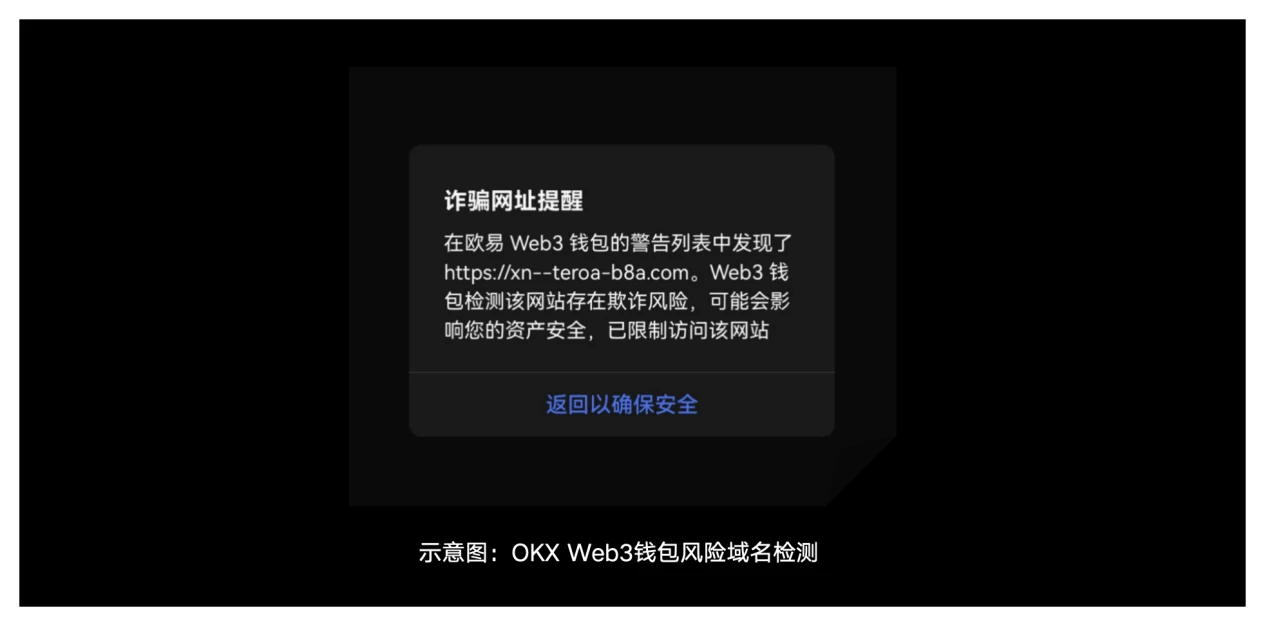
4) Transaction pre-execution: Before a user submits any transaction, the OKX Web3 wallet will simulate the transaction and display the asset and authorization change results for the user’s reference. The user can judge whether the result meets expectations based on the result, so as to decide whether to continue submitting the transaction.
5) Integrated DeFi applications: OKX Web3 wallet has integrated services of various mainstream DeFi projects. Users can safely interact with integrated DeFi projects through OKX Web3 wallet. In addition, OKX Web3 wallet will also recommend paths for DeFi services such as DEX and cross-chain bridges to provide users with the best DeFi services and the best Gas solutions.
6) Black address tag library: OKX Web3 wallet has established a rich black address tag library to prevent users from interacting with known malicious addresses. The tag library is continuously updated to respond to changing security threats and ensure the security of user assets.
7) More security services: OKX Web3 wallet is gradually adding more security features and building more advanced security protection services, which will better and more efficiently protect the assets of OKX Web3 wallet users.
4. Other aspects
1) Security plug-in: OKX Web3 wallet provides built-in anti-phishing protection to help users identify and block potential malicious links and transaction requests, enhancing the security of user accounts.
2) 24-hour online support: OKX Web3 Wallet provides customers with 24-hour online support, promptly following up on incidents of customer asset theft and fraud, and ensuring that users can quickly get help and guidance.
3) User Education: OKX Web3 Wallet regularly publishes security tips and educational materials to help users improve their security awareness and understand how to prevent common security risks and protect their assets.
OKX Web3 Wallet attaches great importance to the security of user assets and continues to invest in protecting user assets, providing multiple security mechanisms to ensure the security of users digital assets.
4. Security is an eternal topic in the encryption industry
In the digital age, the crypto industry, as an emerging and rapidly developing field, is increasingly attracting global attention. However, with the widespread application of cryptocurrency and blockchain technology, various security issues cannot be ignored. Although blockchain technology provides high security for cryptocurrency, the security of the wallet itself is affected by many factors, such as private key security, phishing, or user errors leading to private key leakage.
The decentralized nature of Web3 wallets enables users to fully control their digital assets without relying on any central agency or third-party services. However, this also means that users need to bear the responsibility for the security of their assets. Users should fully realize the importance of wallet and asset security and take effective measures to ensure it.
A secure and reliable Web3 wallet can enhance users trust in the crypto industry. With the continuous development of cryptocurrency and blockchain technology, users have an increasingly strong demand for asset security. As a platform or wallet, we should continue to make efforts in technological innovation, security education and other aspects to provide users with a safe and convenient asset management platform, and provide solid security guarantees for the healthy development of the crypto industry.
Safety is no small matter, it concerns you and me.
Disclaimer:
This article is for reference only and is not intended to provide (i) investment advice or investment recommendations; (ii) an offer or solicitation to buy, sell or hold digital assets; or (iii) financial, accounting, legal or tax advice. Holding digital assets (including stablecoins and NFTs) involves high risks and may fluctuate significantly or even become worthless. You should carefully consider whether trading or holding digital assets is suitable for you based on your financial situation. Please be responsible for understanding and complying with local applicable laws and regulations.
This article is sourced from the internet: Final chapter of the security special issue | OKX Web3: Safeguarding user assets
Related: Hashed: Why did we invest in Taiko?
Original author: Ryan Kim , Edward Tan , Dan Park Original translation: TechFlow Imagine a world where Ethereum scalability is endless, transactions are lightning fast, and user privacy is sacrosanct. It not a distant dream, but a rapidly approaching reality, all thanks to Taiko. As a lead investor , we are excited to support Taiko journey to revolutionize the Ethereum ecosystem, and their Type-1 ZK-VM technology is leading this change. Today, as they launch their mainnet, we are at the cusp of an unprecedented leap in technological innovation. Despite the challenges of integrating ZK with the EVM, Taiko鈥檚 Type-1 ZK-VM technology (launched by CEO Daniel Wang in 2023) is a breakthrough. With CTO Brecht Devos and CFO Terence Lam also involved, the experienced team has successfully launched multiple public testnets…