哈希( SHA1 ) of this article: 9 d 28 ef 4 e 6 e 45 c 21121 d 4 e 6 fc 0 ef 7 c 011 f 4826 3d 8
No.: PandaLY Security Knowledge No.025
As the core driving force of the digital economy, blockchain technology is driving a revolution in the global financial and data security fields. However, the characteristics of decentralization and anonymity have also attracted the attention of cybercriminals, giving rise to a series of attacks targeting crypto assets. Hackers never sleep, and those places where funds are collected are always the targets of hackers. According to data provided by various blockchain analysis and security companies, from 2020 to 2024, the losses caused by Web3-related hacker attacks have exceeded 30 billion. Our ChainSource Security team will deeply analyze several well-known blockchain hacker groups and their well-known cases, reveal their methods of committing crimes, and provide practical strategies for individuals to prevent hacker attacks.
Well-known hacker gangs’ methods and theft cases
North Korean hackers Lazarus Group
background:
According to Wikipedia, Lazarus Group was founded in 2007 and is affiliated with the 110th Research Center under the Reconnaissance General Bureau of the General Staff of the North Korean Peoples Army, specializing in cyber warfare. The organization is divided into two departments: the first department is called BlueNorOff (also known as APT 38), with about 1,700 members, mainly conducts illegal transfers by forging SWIFT orders. It focuses on exploiting network vulnerabilities to obtain economic benefits or control systems to commit financial cybercrimes, mainly targeting financial institutions and cryptocurrency exchanges. The second unit is AndAriel, which has about 1,600 members and mainly conducts attacks against South Korea.
Modus operandi:

In the early days, Lazarus mainly carried out DDoS attacks through botnets, but now their attack methods have shifted to spear phishing attacks, watering hole attacks, supply chain attacks, etc., and they carry out targeted social engineering attacks against different targets. They may use system destruction or ransomware to interfere with the analysis of the incident. In addition, they may use SMB protocol vulnerabilities or related worm tools to move horizontally and drop payloads, and even attack the banks SWIFT system to Its technical features include using multiple encryption algorithms (such as RC 4, AES, Spritz) and custom character transformation algorithms, disguising the TLS protocol to bypass IDS through white domain names in SNI records, and using IRC and HTTP protocol.
In addition, Lazarus damages the system by destroying the MBR, partition table, or writing garbage data to sectors, and uses self-deletion scripts to hide the traces of the attack. Its attack methods include spear phishing attacks by sending Trojan programs as email attachments, In watering hole attacks, Lazarus analyzes the targets online activities, attacks the websites they frequently visit and implants malicious code to steal funds on a large scale; in social engineering attacks, they pretend to be recruiting cryptocurrency workers or network security professionals. Lazarus’s arsenal includes a large number of customized tools, indicating that there is a large development team behind it. Its attack capabilities and tools include DDoS botnets, keyloggers, RATs, and wiper malware. The malicious code used is as follows: Destover, Duuzer and Hangman, among others.
Examples:
-
2017 Bangladesh Bank robbery
The Lazarus hacker group stole $81 million by attacking the SWIFT system. Although this incident mainly involves the traditional banking system, its impact also affects the blockchain field, because the funds obtained by hackers in this way are often used to buy cryptocurrencies. Currency laundering.
-
KuCoin hack in 2020
In September 2020, the KuCoin exchange suffered a massive hacker attack, resulting in losses of up to $200 million. Although direct responsibility has not been fully confirmed, analysts believe it is related to Lazarus. Hackers exploited contract loopholes and system weaknesses to steal a large amount of cryptocurrency. And attempted to transfer and launder money through multiple channels.
-
Ronin Cyber Attack in 2021
Ronin, the blockchain network for the Axie Infinity game, was hacked in March 2021, resulting in losses of more than $600 million. The hackers carried out the attack by attacking the developers nodes and system vulnerabilities. Although direct responsibility has not yet been confirmed, many analysts Link it to Lazarus or other state-sponsored hacking groups.
-
Harmony Cyber Attack in 2022
The cross-chain bridge of the Harmony blockchain was attacked in June 2022, resulting in a loss of approximately $100 million. The attack revealed the security vulnerabilities of the blockchain cross-chain bridge, and although the identity of the attacker was not clear, some experts attributed it to Considering the strategy of North Korean hacker groups, it is believed that they may have carried out this attack using similar methods.
Drainer Gang
A drainer in blockchain usually refers to a malicious smart contract or script whose purpose is to steal funds from a users crypto wallet or account through fraudulent means. This type of attack usually occurs when a user interacts with a fake or compromised decentralized When interacting with a decentralized application (dApp) or website, users may unknowingly grant control of their funds to a malicious contract. The following are some of the more well-known drainer criminal gangs:
background:
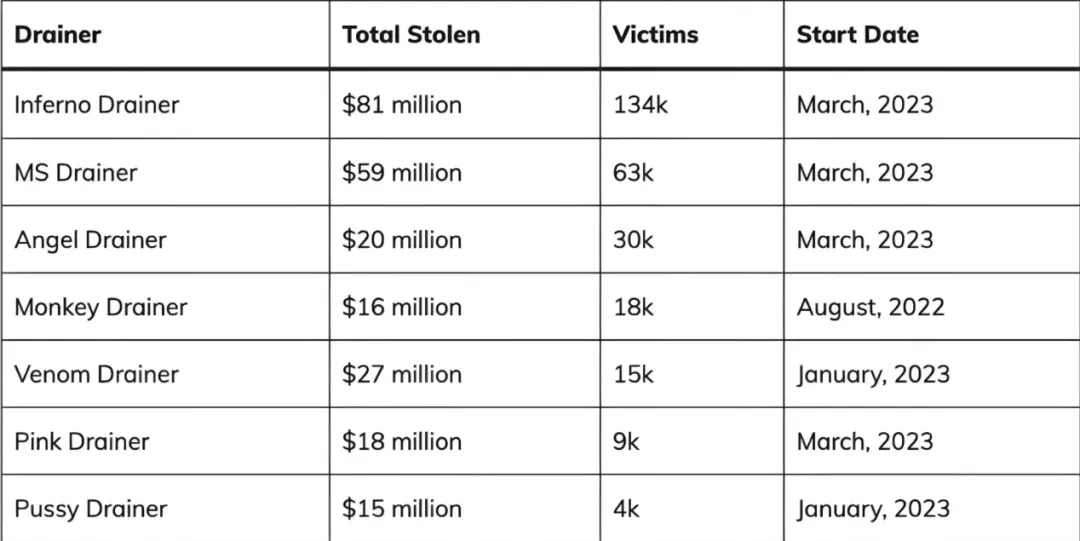
Inferno Drainer is one of the most popular crypto wallet scam tools. It is a Phishing-as-a-Service (PaaS) platform that provides scammers with ready-to-use phishing Through these platforms, attackers can easily create phishing websites disguised as legitimate decentralized applications (dApps) to steal users crypto assets. According to Web3 security company Blockaid, as of July 2024, the number of The number of DApps has increased to 40,000. The number of new malicious DApps using the tool has tripled, and usage has increased by 300%.
Modus operandi:
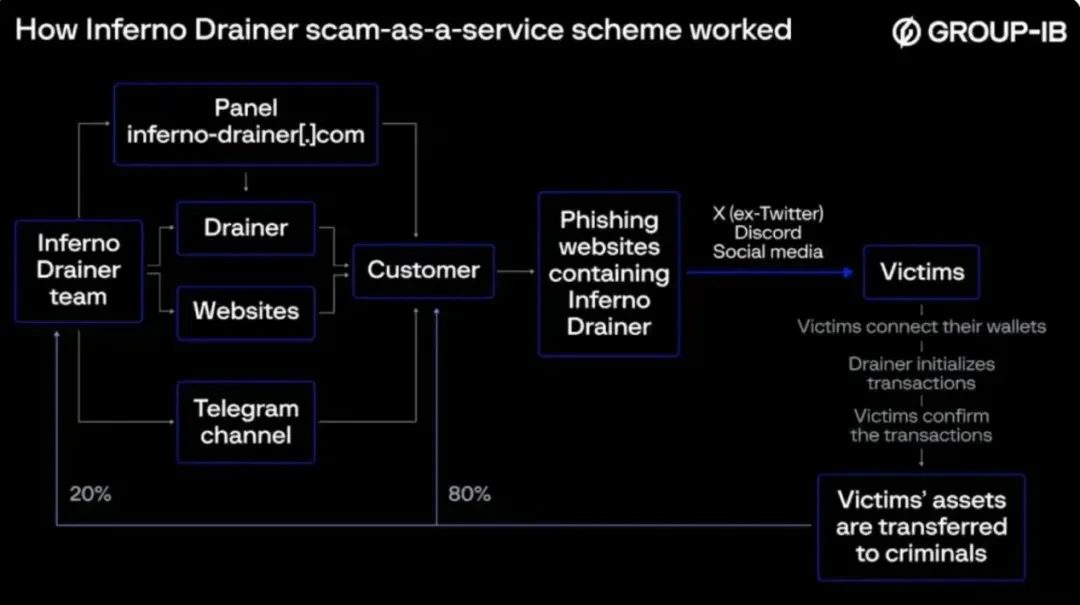
The gang promoted its services through Telegram channels and operated in a scam-as-a-service model, where developers provided phishing websites to scammers to help them carry out their fraudulent activities. When the victim scanned the QR code on the phishing website and connected to their When a victim steals a wallet, Inferno Drainer automatically checks and locates the most valuable and easily transferable assets in the wallet and initiates a malicious transaction. Once the victim confirms the transaction, the assets are transferred to the criminal’s account. % will be distributed to the developers of Inferno Drainer, and the remaining 80% will belong to the scammers.
They mainly target users and platforms related to cryptocurrencies, such as decentralized finance (DeFi) applications, NFT markets, crypto wallets, etc. They use social engineering tactics, such as fake official announcements or airdrop activities, to disguise themselves as legitimate applications. The emergence of such tools has greatly lowered the threshold for online fraud, leading to an increase in related fraud activities.
Examples:
-
OpenSea phishing attack
Hackers used the Inferno Drainer platform to carry out phishing attacks against OpenSea users. OpenSea is a popular NFT 市場 with many users crypto wallets linked to their accounts. The attacker created a phishing page disguised as the OpenSea website and sent messages to users through email and social media. Advertisements attract users to visit. When users connect their wallets on this page and authorize transactions, Inferno Drainer automatically initiates malicious transactions, transferring NFTs and cryptocurrencies in the users wallet to addresses controlled by hackers. This attack caused dozens of users to lose Their precious NFTs and large amounts of Ethereum were lost, with the total loss amounting to millions of dollars.
-
Uniswap Phishing Attack
Uniswap is one of the most popular decentralized exchanges in the decentralized finance (DeFi) space. Inferno Drainer was used in phishing attacks disguised as Uniswap. The attacker created a fake Uniswap website and used Google ads, social After the victim authorized the malicious contract on the website, Inferno Drainer would quickly scan their account and initiate a transaction to transfer tokens to steal the users assets. A large number of tokens and stablecoins were lost in the scam, with a total value ranging from hundreds of thousands to millions of dollars.
The attack methods commonly used by hacker gangs are similar
-
Phishing
Hackers pretend to be trustworthy organizations or individuals, tricking victims into clicking on malicious links or revealing private keys, thereby obtaining their crypto assets. For example, the Lazarus Group once successfully stole cryptocurrency transactions by forging the identities of government officials and launching precision phishing attacks. The huge amount of funds.
-
Malware
Hackers infect victims devices with malware to steal their cryptocurrency or gain remote control of the devices. FIN 6 often uses custom malware specifically targeting financial institutions and cryptocurrency exchanges.
-
Smart Contract Vulnerability Exploitation
Hackers can illegally transfer or steal funds by identifying and exploiting vulnerabilities in smart contracts. Since the code of smart contracts cannot be changed once they are deployed on the blockchain, the harm caused by vulnerabilities can be extremely serious.
-
51% Attack
Hackers can conduct double-spending attacks or tamper with transaction records by controlling more than 50% of the computing power in the blockchain network. Such attacks are particularly targeted at small or emerging blockchain networks, because their computing power is relatively concentrated and can be easily manipulated maliciously.
Precautions for individual customers
-
Enhance safety awareness
Always be vigilant and do not click on unfamiliar links or download software from unknown sources. Especially when it comes to operations involving cryptocurrencies, you need to be more cautious to avoid falling into traps.
-
Enable two-factor authentication
Enable two-factor authentication (2FA) on all your cryptocurrency accounts to add an extra layer of security to your accounts and prevent unauthorized logins.
-
Using a Hardware Wallet
Store most of your cryptocurrencies in hardware wallets rather than online wallets or exchanges. This offline storage method can effectively reduce the risk of remote hacking.
-
Reviewing Smart Contracts
Before interacting with a smart contract, try to understand the contract code or choose a professionally audited contract to avoid interacting with unverified smart contracts and reduce the risk of funds being stolen.
-
Update equipment and software regularly
Make sure all devices and related software used are up to date and perform regular security updates to prevent attacks due to old vulnerabilities.
結論
In the blockchain field, security is always a critical issue. Understanding and identifying well-known hacker groups, tools, and their methods of committing crimes, combined with effective personal prevention measures, can greatly reduce the risk of becoming a target of attack. With the continuous development, hacker methods are also upgrading. The Lianyuan Security Team recommends that users need to continuously improve their security awareness and stay vigilant at all times in order to remain invincible in this rapidly changing digital age.
涾源科技是一家專注於區塊鏈安全的公司。我們的核心工作包括區塊鏈安全研究、鏈上資料分析以及資產和合約漏洞救援。我們已成功為個人和機構追回許多被盜的數位資產。同時,我們致力於為產業組織提供專案安全分析報告、鏈上溯源和技術諮詢/支援服務。
感謝您的閱讀。我們將持續關注並分享區塊鏈安全內容。
This article is sourced from the internet: Hacker threats in the digital economy: A full analysis of the Lazarus and Drainer gangs
Original article by Ryan S. Gladwin , Decrypt Original translation: Felix, PANews A nutritional supplement company allegedly hired a group of trolls to impersonate celebrities, defraud investors, and sell its tokens. The scheme worked for a while, but has since been unravelled. Insane Labz, an Arkansas-based supplement company with a strong reputation in the MMA and Barstool Sports worlds and a former client of Gary Vaynerchuk’s entrepreneurial mentoring program, launched its LABZ token in May, and in its roadmap, the project promised to work with “vetted celebrities.” But the project encouraged trolls to impersonate celebrities, such as UFC president Dana White, MMA legend Nate Diaz, and social media personality Hasbulla, and tout LABZ tokens in the project’s Telegram group. The scam helped the LABZ token’s market value soar from $3…







