原作者:弗蘭克,PANews
The world has suffered from MEV for a long time.
Despite complaints, the MEV robot has not been restricted and is still accumulating wealth through the sandwich attack.
On June 16, a researcher named Ben exposed on social media that a sandwich attack robot with an address starting with arsc (hereinafter referred to as arsc) made more than 30 million US dollars in 2 months. PANews conducted an in-depth analysis of the behavior and operation of this MEV robot to understand how this MEV robot achieved tens of millions of wealth.
A pile of sand makes a tower, indiscriminate attack
A sandwich attack is a market manipulation strategy in which an attacker inserts his own transactions one after the other in a blockchain transaction with the aim of profiting from price movements caused by the victims transactions.
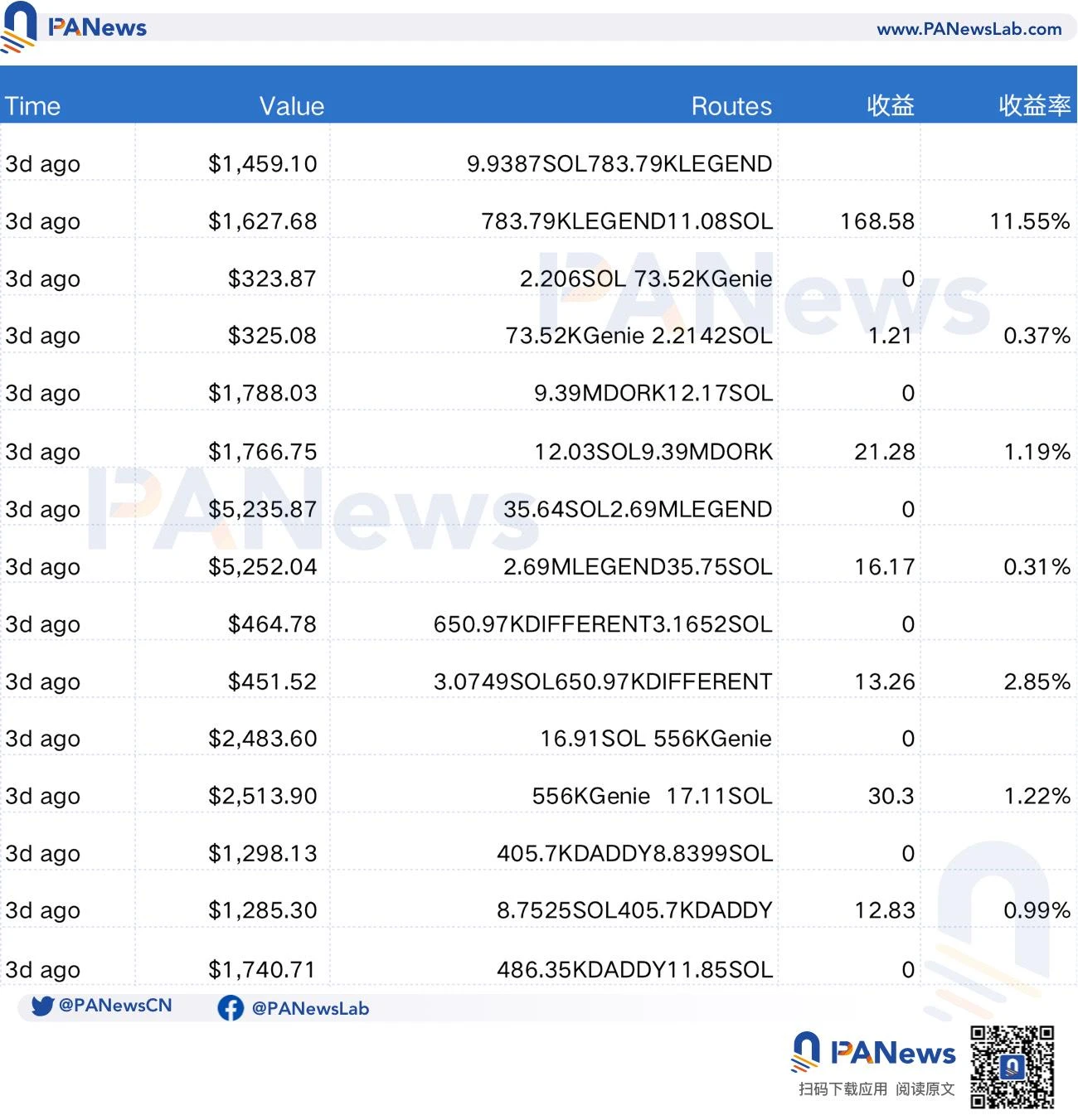
Since the Solana browser can only view the last 1,000 transactions of the day, we can only capture arscs transactions from 15:38 to 16:00 on April 21, which was nearly 20 minutes. During this period, the robot made 494 transactions, with an initial SOL balance of 449, and after 20 minutes, the balance increased to 465. In other words, in just 20 minutes, the arsc address completed the income of 16 SOL through the sandwich attack. At this rate, its daily income is about 1,152 SOL. Calculated based on the SOL price of about US$150 at the time, the daily income can reach US$172,800.
PANews counted the last 100 transactions of arsc and found that the average investment of arsc was about $6,990, the average profit of a single transaction was about $38, and the average return rate of a single transaction was about 3.44%. Orders as small as $43 and as large as $160,000 can become targets of its attacks. The higher the value of the order, the higher the single income. An order targeting $160,000 brought a profit of $1,200. It can be said to be an indiscriminate attack.
(Figure: Some transaction records and earnings of arsc)
As arscs principal increases, its profit rate is also steadily increasing. On April 22, the profit amount reached 63 SOL in 492 attacks within half an hour that day, and the daily profit amount level increased to about 3,000 SOL, about twice the previous day. In fact, in the two months of record, arsc has made a total profit of 209,500 SOL, an average daily profit of 3,800 SOL, and an average daily income of about 570,000 US dollars. This income capacity even exceeds the recently popular MEME coin issuance platform Pump.fun (on June 19, Pump.funs 24-hour income was about 557,000 US dollars).
The attacker is a large staker of the super validator
After making profits from the sandwich attack, the address transferred a total of 209,500 SOLs to the address 9973 hWbcumZNeKd 4 UxW 1 wT 892 rcdHQNwjfnz 8 KwzyWp 6 (hereinafter referred to as 9973), which is worth about 31.425 million US dollars (based on the price of 150 US dollars). Subsequently, the 9973 address transferred 124,400 SOLs to the address Ai 4 zqY 7 gjyAPhtUsGnCfabM 5 oHcZLt 3 htjpSoUKvxkkt (hereinafter referred to as Ai4z ), 和 Ai4z sold these SOL tokens into USDC through a decentralized exchange.
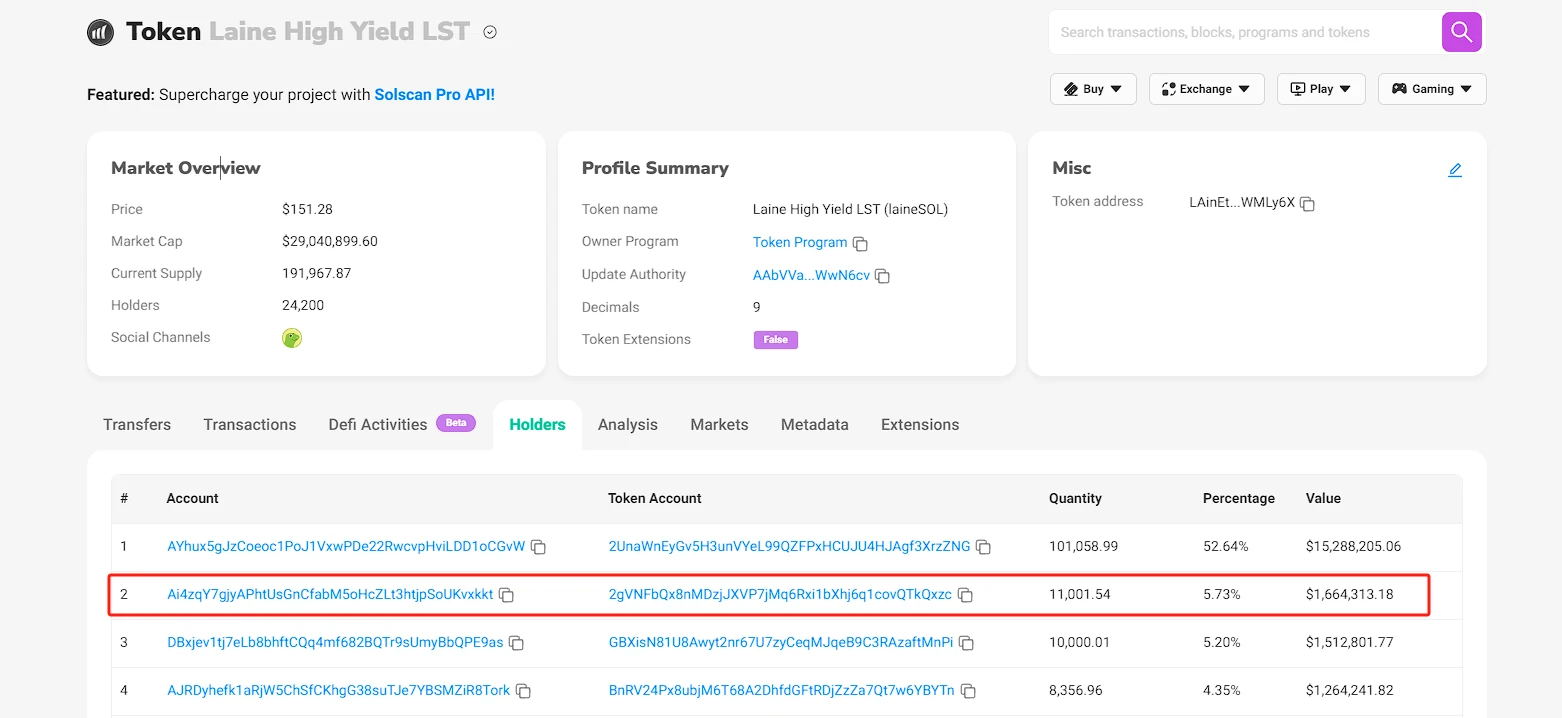
In addition, the Ai4z address also pledged its SOL to several Solana validators, including 11,001 SOL to Laine, 8,579 to Jito, 4,908 to Pumpkins, 2,467 to Jupiter, and about 800 each to Marinade and Blazestake.
Among them, the total number of staked tokens on laineSOL is 190,000, and the Ai4z address is the largest individual staker of Laine, accounting for 5.73%, second only to the largest holding address of a certain exchange. laineSOL is a staking interest issued by a validator. Users can stake and vote by holding this token while also obtaining DeFi benefits. However, there is currently no evidence to show whether this staking behavior indicates that Laine has any other additional relationship with the attacker, but to some extent there is a certain binding of interests between the two. Laine is one of the main validators on the Solana chain and was previously the main supporter of pushing Solana to issue 100% of the priority fees to validators. (Related reading: Behind Solanas vote to reward validators with 100% priority fees, community disputes continue to highlight governance issues )
Why Sandwich Attacks on Solana Keep Coming
From the root, MEV on Solana is a new business. Before the release of the MEV reward protocol Jito, the MEV data on Solana was almost negligible. After Jito launched the MEV reward plan, more than 66% of validators are now running the Jito-Solana client. The feature of this client is that it allows users to pay additional consumption (Tip) to validators to allow validators to run bundled transaction packages first. In addition, Jito also runs a mempool, which can be used by sandwich attackers to monitor the content of transactions initiated by users. In March, Jito announced the temporary closure of the mempool to reduce sandwich attacks, but the MEV robot can still monitor transactions by running an RPC node.
In essence, MEV is not a completely useless design. By prioritizing fees and other methods, a large number of spam attacks can be avoided, which plays a certain role in maintaining the health of the blockchain network. However, the current mode on Solana that can still monitor user transactions and the mode that tip payers can package transactions still leaves loopholes for sandwich attacks.
The Solana Foundation previously announced on June 10 that it had deleted more than 30 validators who participated in the sandwich attack. However, in terms of effectiveness, this governance plan did not play a big role. PANews investigated the transaction process of arsc and found that many of the validators it selected for the sandwich attack were large validators such as Laine, Jito, and Jupiter. The attack behavior of this address did not stop until June 14, and it did not seem to be affected by the Solana Foundations punishment governance. (Related reading: Solana Foundation took action against MEV validators, but the community did not buy it and complained about the centralization of governance )
Sandwich attacks can also be subject to legal sanctions
Is a sandwich attack really a risk-free arbitrage? The answer is no. There are cases that show that such grabbing behavior may have legal risks.
In May, the U.S. Department of Justice announced that brothers Anton and James Pepaire-Bueno had been arrested for allegedly stealing $25 million in cryptocurrency through a sophisticated arbitrage bot vulnerability on Ethereum.
Perhaps considering the legal risks, the arsc address seems to have suspended the sandwich attack and tried to hide the evidence of the previous attack by refreshing the Solana browser records with thousands of small transactions. However, the assets related to the address are still on the chain and have not been transferred to any centralized exchange.
At present, the clamping behavior of arsc has aroused public outrage, and there are hundreds of tweets on Twitter offering rewards for tracking down the people behind the address. Perhaps, in the near future, the moment when this mysterious attacker shows his prototype will also be the time when he faces severe judicial punishment.
This article is sourced from the internet: In-depth analysis: How did MEV Robotics make $30 million in 2 months?
相關:鏈上衍生性商品浪潮來襲,解讀變革新力量 SOFA.org
引言隨著低成本L2甚至專有鏈的發展,從CEX到鏈上衍生品的趨勢已經勢不可擋。儘管一系列鏈上衍生品取得了驕人的成績,但與CEX相比,其市佔率仍然較小。追根溯源,鍊和衍生性商品之間存在資金和模型的差距,進而導致用戶使用量和轉換率不足。衍生性商品賽道迫切需要改變的力量。針對此,一系列生態系統和領先專案推出了衍生性商品基礎設施組織 SOFA.org ,其成員包括投資管理公司 Galaxy Asia Trading Ltd.、Layer 2 Arbitrum、Linea、基礎設施 Chainlink、OKX Wallet、SignalPlus、VC OKX Ventures、HashKey Capital 等。