Một con đường mới cho thông tin chuỗi chéo: LayerZero và EigenLayer ra mắt khuôn khổ CryptoEconomic DVN
Tác giả gốc: YBB Capital Researcher Ac-Core
Tóm lại
-
The CryptoEconomic DVN Framework combines LayerZero’s cross-chain messaging with EigenLayer’s economic security and incentives.
-
The DVN framework operates through a structured process with three main phases: verification, veto, and punishment;
-
LayerZero chose to work with EigenLayer to further deepen the decentralization of its DVN, accepting ETH, ZRO, and EIGEN as collateral assets while also bringing new growth flywheels to both tokens;
-
The CryptoEconomic DVN Framework may help improve the security of the entire chain in the future.
1. Understanding the narrative background: Iterative upgrades of EigenLayer and LayerZero
Image source: LayerZero Official
According to a news release on October 2, 2024, LayerZero Labs and Eigen Labs have jointly launched a crypto-economic decentralized verification network (DVN) framework, which aims to provide crypto-economic security for full-chain messaging. Under this framework, developers can not only deploy their own DVN on EigenLayer, but also enhance the security and reliability of cross-chain messaging by introducing incentive mechanisms.
To quickly summarize in one sentence, the CoyptoEconomicDVN framework combines the cross-chain security mechanism of LayerZero with the dual protection of EigenLayers re-staking encryption. Its core purpose is to use EigenLayers crypto-economic model to provide higher security and incentives for the decentralized verification network (DVN).
1.1 Step 1: CryptoEconomic DVN’s cross-chain mechanism paves the way for LayerZero V2
LayerZero is not only an asset cross-chain but also a trustless cross-chain communication protocol. It separates the ultimate trust link through repeaters and oracles, that is, it realizes cross-chain messages through a super light node mechanism.
The core design of the LayerZero V2 architecture can be divided into three categories: protocols, standards, and infrastructure.
1. Protocol
The protocol portion of LayerZero is consistent across all supported blockchains and is immutable and permissionless, ensuring censorship resistance and long-term stability. This portion consists of two main components:
-
Endpoints: These are immutable, non-upgradeable smart contracts on each blockchain and are at the heart of the LayerZero protocol. Endpoints provide a standardized interface for applications to manage security configurations and send/receive messages across chains. Due to the immutability of endpoints, once they are deployed, no entity can modify them;
-
MessageLibs: Message libraries are connected to endpoints and are responsible for handling cross-chain message verification and communication. Each message library update is additive and does not replace the old version, so that even if the protocol needs to be upgraded, developers can still choose to use the old message library to ensure backward compatibility. This is similar to different versions of smart contracts on the blockchain, and users can choose different versions to use as needed.
Image source: LayerZero endpoint description
2. Standards
The standards provided by LayerZero allow developers to build applications and tokens that run consistently across multiple blockchains, achieving cross-chain “unified semantics”, meaning that applications or tokens behave the same across different blockchains. These standards help simplify the development process and ensure consistency and scalability of cross-chain applications.
-
Contract Standards: LayerZero provides standards such as OApp (Omnichain Application) and OFT (Omnichain Mã thông báo), which extend existing smart contract standards (for example, OFT is an extension of the ERC-20 standard), allowing developers to quickly create applications and tokens that can run on all LayerZero-supported blockchains;
-
Message Packets: used to transfer data and commands between blockchains. Message packets contain elements to prevent replay attacks and incorrect routing (such as Nonce, source/target chain ID, unique identifier), and contain the actual command or data payload to be executed on the target chain. This message format can adapt to various blockchain environments (including EVM and non-EVM chains, public chains and private chains), ensuring the accuracy and security of cross-chain information transmission;
-
Design Patterns: LayerZero provides a series of design patterns (such as AB, ABA, and combined AB) that provide developers with the basic building blocks for cross-chain applications and simplify the process of developing complex cross-chain interactions. These patterns can help developers create a more concise and efficient user experience, such as completing cross-chain bridging and exchange of tokens in one transaction.
Image source: Combinatorial ABA design pattern
3. Infrastructure
LayerZeros infrastructure layer is fully open and modular, and any entity can join the LayerZero network to verify and execute transactions. This design enables applications to choose different verification and execution methods according to their needs to achieve the optimal balance in terms of security, cost, speed, etc.
-
Decentralized Verification Networks (DVNs): These networks verify cross-chain messages, and any entity that can verify cross-chain data packets can join LayerZero as a DVN. This decentralized design allows applications to choose the right combination of validators to avoid being locked into a single validator network. Currently, there are 15+ DVNs participating in LayerZero, including the zkLight client provided by Google Cloud and Polyhedra;
-
Executors: Any entity can run an executor, which is responsible for ensuring the smooth execution of cross-chain messages on the target chain. Executors simplify the user experience, allowing users to only pay gas fees on the source chain without having to perform additional operations on the target chain. Applications can choose one or more executors based on their needs, and can even build their own executors or choose to manually execute cross-chain messages;
-
Security Stack: Each application can configure a unique security stack based on its needs, including the selection of DVNs, executors, and other security preferences. The security stack allows applications to choose how to verify cross-chain messages and make adjustments when necessary, providing a highly customized security solution and avoiding being locked into a single security model.
To better understand the CryptoEconomic DVN Framework, here is some additional information about LayerZero V2 DVN:
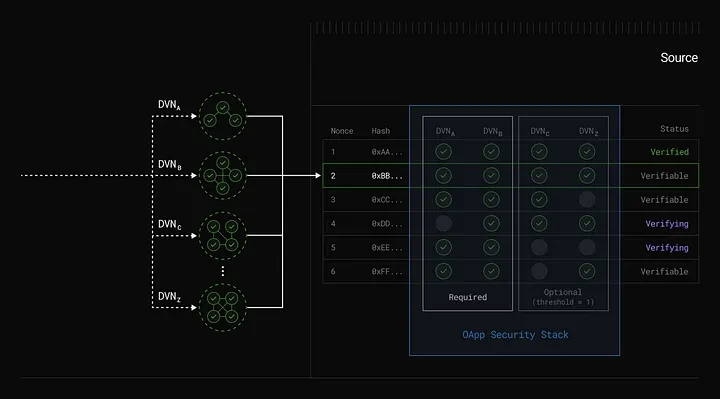
Decentralized verification networks (DVNs) are used to verify messages transmitted between different blockchain networks. Each application built on LayerZero can customize its security stack by choosing DVNs. The key points are: 1. DVNs: These entities are responsible for verifying cross-chain messages and ensuring their security and integrity. Developers can configure which DVNs to use as needed and set optional verification thresholds. 2. Openness: Anyone can create or develop a DVN, which provides a variety of verification options. DVNs can include validators, signers, or adopt advanced technologies such as zero-knowledge proofs (ZKP) and intermediate chains. 3. Customizable security: Applications can choose different DVNs based on their security needs. Unlike the one-size-fits-all model of other protocols, this flexibility enables applications to adjust security settings as needed, reducing costs and risks. 4. DVN combination: Through the X of Y of N configuration, applications can choose multiple DVNs to verify messages. For example, a “1 of 3 of 5” configuration would require one specific DVN and two other validators chosen from among the five DVNs.
Image source: DVNs position in the V2 architecture
1.2 Part 2: CryptoEconomic DVN’s Cryptoeconomic Security EigenLayer
EigenLayer consists of a series of smart contracts that allow users to choose to re-stake their ETH or Liquidity Staking Tokens (LST) to hướng dẫn new Proof of Stake (PoS) networks and services in the Ethereum ecosystem, obtain additional staking income/rewards, and provide security and decentralization attributes for other modular components and blockchain networks. Simply put, its essence is to sell the security of Ethereum. EigenLayer has created five categories: native re-staking, LRT, AVS, super-large-scale Rollups, and committed applications.
1. Native re-staking
Ability to input multiple commitments for verification at the same time, measure the cryptoeconomic bandwidth consumed by each commitment, and ensure that all commitments are solvent. The essence is Ethereums Elastic Extension of Security (ES 2). If the conditions of each AVS are met, they can all be secure;
2. Liquidity Re-Pledge
LRT is a mechanism where Liquidity Restaking Tokens (LRTs) are similar to Liquidity Staking Tokens (LSD) on Ethereum, which are tokenized representations of assets stored on EigenLayer, thereby unlocking the liquidity that was originally locked;
3. AVS Economy
The core of EienLayer is the collection of decentralized systems that can be built, and the ability to pair the technology with a certain degree of decentralized trust architecture. The AVS-centric roadmap ensures that permissionless decentralized services can be integrated to build any application and create different categories and customized AVS on Eigenlayer;
4. Large-Scale Rollups
Most crypto application development is still limited by block space. There is no corresponding concept of cloud space, which will expand according to demand.
EigenDA, for example, is a mechanism for infinitely scaling bandwidth and enables a variety of new use cases that were not possible before: converting the cloud to crypto;
5. Have a trustworthy application
Eigenlayer was built to maximize the number of commitments. EigenLayer + Ethereum provides Ethereum-level diversity and verifiable commitments. For example: 1. Maximizing the increase effect through EigenDA; 2. Achieving diversity through open innovation in Eigenlayer AVS; 3. Introducing off-chain verifiability into the on-chain mechanism to achieve verifiable computing.
2. Token economy empowerment, LayerZero x EigenLayer dual cooperation, ZRO and EIGEN can be used as collateral assets
Image source: Explaining the process of staking, verification, veto and punishment
Long story short, CryptoEconomic Distributed Verification Networks (DVNs) improve cross-chain security in three key ways:
-
Cryptoeconomic security: DVNs introduce a penalty mechanism (Slashing). When a DVN behaves maliciously or makes mistakes, its staked assets will be punished. This economic model ensures that DVN has sufficient economic incentives to maintain correct behavior, because improper behavior will result in significant economic losses, thereby promoting its sense of responsibility and security;
-
AVS-defined security: Each Active Verification Service (AVS) defines the types of assets that can be staked and their penalty conditions. This flexibility allows different types of DVNs (such as ZKP-based, Middlechain-based, or Proof-of-Authority DVNs) to enhance their security through additional staking guarantees, further increasing the economic deterrent against malicious behavior;
-
Permissionless security: Anyone can contribute to the security of DVN by staking assets, which makes the system more open and participatory. DVNs can choose any asset (such as ZRO, ETH, EIGEN) to support their network, broadening security options and enhancing decentralization.
The CryptoEconomic DVN framework is an open source system that aims to enhance the security of the decentralized verification network (DVN) through economic incentives tied to tokens. It relies on LayerZeros DVN verification messages and adds an additional layer of security. Specifically, four key mechanisms are used to protect LayerZeros cross-chain messaging: staking, verification, veto, and punishment.
-
Staking: Validators (stakers) lock tokens such as ZRO, EIGEN, or ETH in the DVN’s Active Validation Set (AVS) as collateral. Staking funds incentivize validators to act honestly, because if they misbehave, the staked assets may be punished (slashed);
-
Verification: A user or application can trigger a cross-chain round-trip message (Ethereum → source chain → target chain → Ethereum) to verify that the hash value recorded by the DVN matches the hash value recorded on the chain. If they match, the process ends;
-
Veto: If a mismatch is found, a veto process is initiated, allowing token holders to vote on whether to penalize (slash) DVNs stake. This step prevents false slashing due to non-malicious errors such as blockchain reorganizations, as reorganizations may cause data packets to mismatch, but DVN may actually be honest;
-
Penalty: If the veto fails and DVN is confirmed to have malicious behavior or verification errors, the DVN staked assets will be slashed.
The framework is divided into three phases:
-
Phase 1: Verification – Messages are verified on multiple chains, using independent DVNs to ensure fairness;
-
Phase 2: Veto – If a discrepancy is found, the veto contract is triggered and holders vote on whether to slash their DVN stake.
-
Phase 3: Punishment – If the veto fails, DVN’s staked assets will be slashed due to malicious behavior or incorrect verification.
3. Views on CryptoEconomic DVN Framework
Today, the Ethereum infrastructure is becoming more complete, and the multi-chain structure has become a foregone conclusion. The communication security issue between different chains is still a challenge that cannot be ignored. The main innovation of the CryptoEconomic DVN Framework is that it provides core components for DVN through AVS, defines the pledged assets and penalty mechanism. In the long run, it may help improve the security of the entire chain, but the uncertain impact it brings is also a common problem in the industry. How to find a balance between security and flexibility is a problem that needs to be solved in the future.
There is no doubt that the CryptoEconomic DVN Framework is a two-way empowerment cooperation between LayerZero Labs and Eigen Labs. From a technical perspective, it provides protection through staking, penalty mechanisms, verification and veto mechanisms; but from an economic benefit perspective, this is still a nesting doll operation of PoS staking income.
LayerZero chose to work with EigenLayer to further deepen the decentralization of its DVN, accepting ETH, ZRO and EIGEN as collateral assets while also bringing new growth flywheels to both tokens. LayerZero provides technology and EigenLayer provides funding. The cooperation between the two parties allows validators to be rewarded and encourages honest behavior in this economic system.
Bài viết tham khảo:
(1) LayerZero V2 Deep Dive
(2) LayerZero x EigenLayer: The CryptoEconomic DVN Framework
This article is sourced from the internet: A new path for cross-chain information: LayerZero and EigenLayer launch CryptoEconomic DVN framework
Theo số liệu thống kê chưa đầy đủ từ Odaily Planet Daily, có 19 sự kiện tài trợ blockchain trong và ngoài nước được công bố từ ngày 16 tháng 9 đến ngày 22 tháng 9, tăng so với dữ liệu của tuần trước (18). Tổng số tiền tài trợ được công bố là khoảng $180 triệu đô la Mỹ, tăng so với dữ liệu của tuần trước ($128 triệu đô la Mỹ). Tuần trước, dự án nhận được nhiều đầu tư nhất là chuỗi công khai mô-đun Celestia ($100 triệu đô la Mỹ); theo sát là giao thức tương tác Rollup Initia ($14 triệu đô la Mỹ). Sau đây là các sự kiện tài trợ cụ thể (Lưu ý: 1. Sắp xếp theo số tiền được công bố; 2. Không bao gồm các sự kiện gây quỹ và MA; 3. * biểu thị một công ty truyền thống có hoạt động kinh doanh liên quan đến blockchain): Celestia Foundation công bố vòng tài trợ $100 triệu đô la Mỹ do Bain Capital Crypto dẫn đầu Vào ngày 24 tháng 9, Celestia Foundation, nhóm đứng sau…