Chống lừa đảo: Tìm hiểu bốn chức năng chặn giao dịch rủi ro của ví OKX Web3 trong một bài viết
Scam Sniffer released the 2024 Mid-Year Phishing Report, which showed that in the first half of 2024 alone, 260,000 victims lost $314 million on the EVM chain, of which 20 people lost more than $1 million per person. Sadly, another victim lost $11 million, becoming the second largest theft victim in history.
According to the report, most ERC 20 token thefts are caused by signing phishing signatures, such as Permit, IncreaseAllowance, and Uniswap Permit 2. Most of the large thefts involve Staking, Restaking, Aave mortgage, and Pendle tokens. Most victims are directed to phishing websites through phishing comments from fake Twitter accounts.
Phishing attacks are undoubtedly still the hardest hit area of on-chain security issues.
As an entry-level product that meets the basic transaction needs of users, OKX Web3 Wallet insists on focusing on strengthening security measures and user education. At the product level, the team has recently upgraded the risk transaction interception function mainly around high-frequency phishing scenarios, and stated that it will continue to identify more risk scenarios to prompt users in the future.
This article aims to explain the applicable scenarios of the four risky transaction interception functions of the latest upgrade of the OKX Web3 wallet, and at the same time popularize the operating principles of some theft cases. I hope it will be helpful to you.
1. Malicious authorization to EOA account
On June 26, a user lost $217,000 by signing multiple phishing signatures on a fake Blast phishing website; on July 3, ZachXBT reported that the address 0x D 7 b 2 had become a victim of Fake_Phishing 187019 phishing, resulting in the loss of 6 BAYC NFTs and 40 Beans (worth approximately $1 million); on July 24, a Pendle user had PENDLEPT re-pledge tokens worth approximately $4.69 million stolen due to multiple Permit phishing signatures 1 hour ago.
In the past two months, there have been many incidents and single amounts of losses caused by various types of signature phishing, which has become an important scenario for frequent security issues. The vast majority of scenarios are to induce users to authorize hackers EOA accounts.
Malicious authorization to an EOA account generally refers to hackers inducing users to authorize through various welfare activities, and authorizing their user addresses to the signature of an EOA address.
EOA stands for Externally Owned Accounts, which is also translated as external account. It is a type of account on the Ethereum-based blockchain network. Unlike another type of account on Ethereum, the Contract Account, EOA is owned by the user and is not controlled by smart contracts. When players surf on the chain, they usually authorize the smart contract account of the project party rather than the EOA account owned by individuals.
Currently, there are three most common authorization methods: Approve is a common authorization method in the ERC-20 token standard. It authorizes a third party (such as a smart contract) to spend a certain number of tokens in the name of the token holder. Users need to authorize a certain number of tokens for a smart contract in advance, after which the contract can call the transferFrom function to transfer these tokens at any time. If the user accidentally authorizes a malicious contract, these authorized tokens may be transferred immediately. It is worth noting that the authorization traces of Approve can be seen in the victims wallet address.
Permit is an extended authorization method introduced based on the ERC-20 standard. It authorizes third parties to spend tokens through message signatures instead of directly calling smart contracts. In simple terms, users can approve others to transfer their tokens by signing. Hackers can use this method to attack. For example, they can set up a phishing website and replace the login button with Permit, so as to easily obtain the users signature.
Permit 2 is not a standard feature of ERC-20, but a feature introduced by Uniswap for user convenience. This feature allows Uniswap users to pay Gas fees only once during use. However, it should be noted that if you have used Uniswap and you have authorized an unlimited amount to the contract, you may become a target of Permit 2 phishing attacks.
Permit and Permit 2 are offline signature methods. The victims wallet address does not need to pay Gas. The phishers wallet address will provide authorization for on-chain operations. Therefore, the authorization traces of these two signatures can only be seen in the phishers wallet address. Now Permit and Permit 2 signature phishing has become a major disaster area in the field of Web3 asset security.
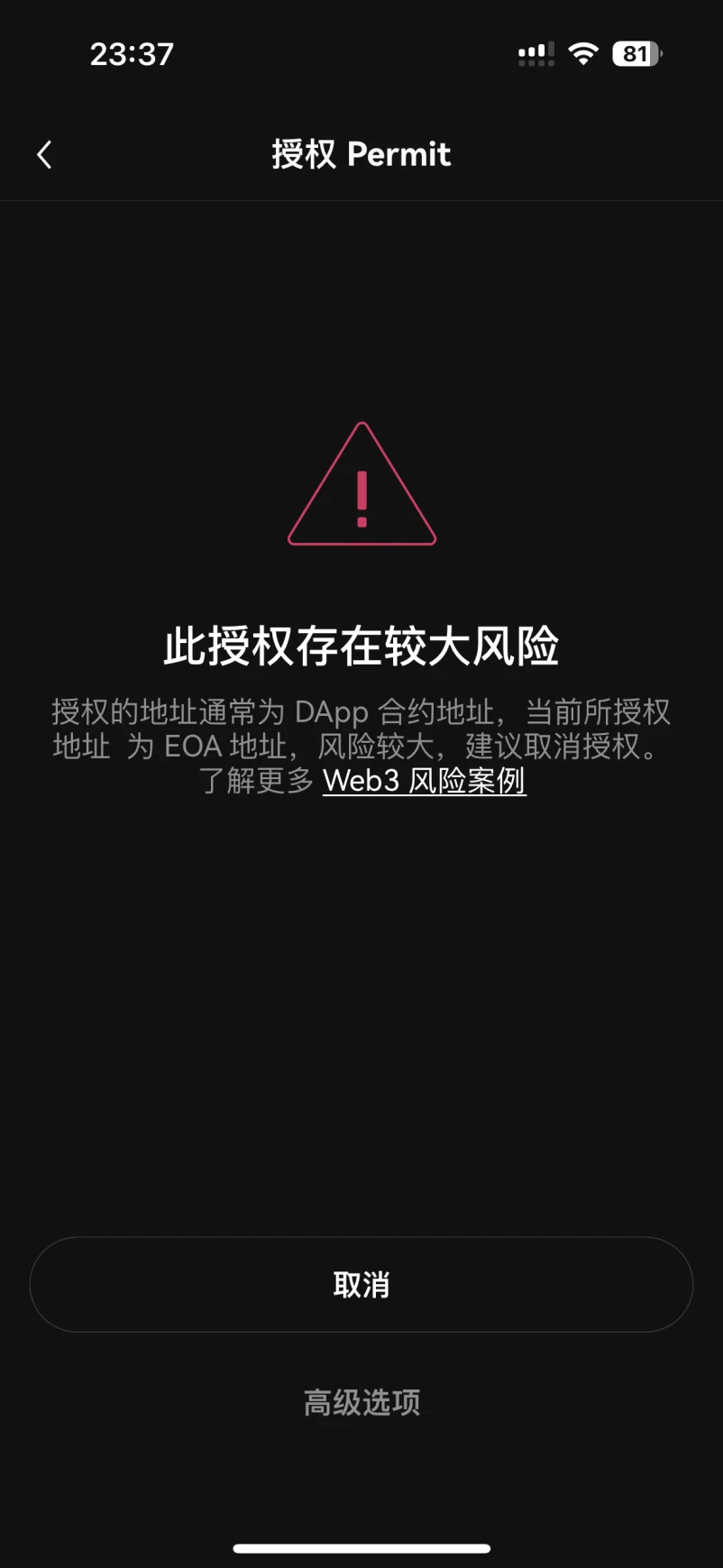
In this scenario, how does the OKX Web3 wallet interception function work?
OKX Web3 wallet will pre-parse the pending transaction. If the analysis finds that the transaction is an authorized behavior and the authorized address is an EOA address, it will alert the user to prevent the user from being phished and causing asset loss.
2. Maliciously changing the account owner
Malicious changes to account owners usually occur on public chains such as TRON and Solana, where the underlying mechanism has an account owner design. Once a user signs, they will lose control of the account.
Taking TRON wallet as an example, TRONs multi-signature permission system is designed with three different permissions: Owner, Witness, and Active. Each permission has specific functions and uses.
The Owner permission has the highest authority to execute all contracts and operations. Only with this permission can other permissions be modified, including adding or removing other signers. When a new account is created, the account itself has this permission by default.
Witness permissions are mainly related to Super Representatives. Accounts with this permission can participate in the election and voting of Super Representatives and manage operations related to Super Representatives.
Active permissions are used for daily operations, such as transferring and calling smart contracts. This permission can be set and modified by the Owner permission and is often assigned to accounts that need to perform specific tasks. It is a collection of several authorized operations (such as TRX transfers and pledged assets).
One situation is that after a hacker obtains the users private key/mnemonic phrase, if the user does not use the multi-signature mechanism (that is, the wallet account is controlled by only one user), the hacker can authorize the Owner/Active permissions to his own address or transfer the users Owner/Active permissions to himself. This operation is usually called malicious multi-signature.
If the users Owner/Active permissions are not removed, the hacker can use the multi-signature mechanism to jointly control the account ownership with the user . At this time, the user has both the private key/mnemonic phrase and the Owner/Active permissions, but cannot transfer his or her assets. When the user initiates a transfer request, both the user and the hackers address need to sign in order to execute the transaction normally.
There is also a situation where hackers take advantage of TRONs permission management design mechanism to directly transfer the users Owner/Active permissions to the hackers address, causing the user to lose the Owner/Active permissions.
The results of the above two situations are the same. Regardless of whether the user still has Owner/Active permissions, he will lose actual control over the account. The hacker address obtains the highest permissions of the account and can change account permissions, transfer assets, and other operations.
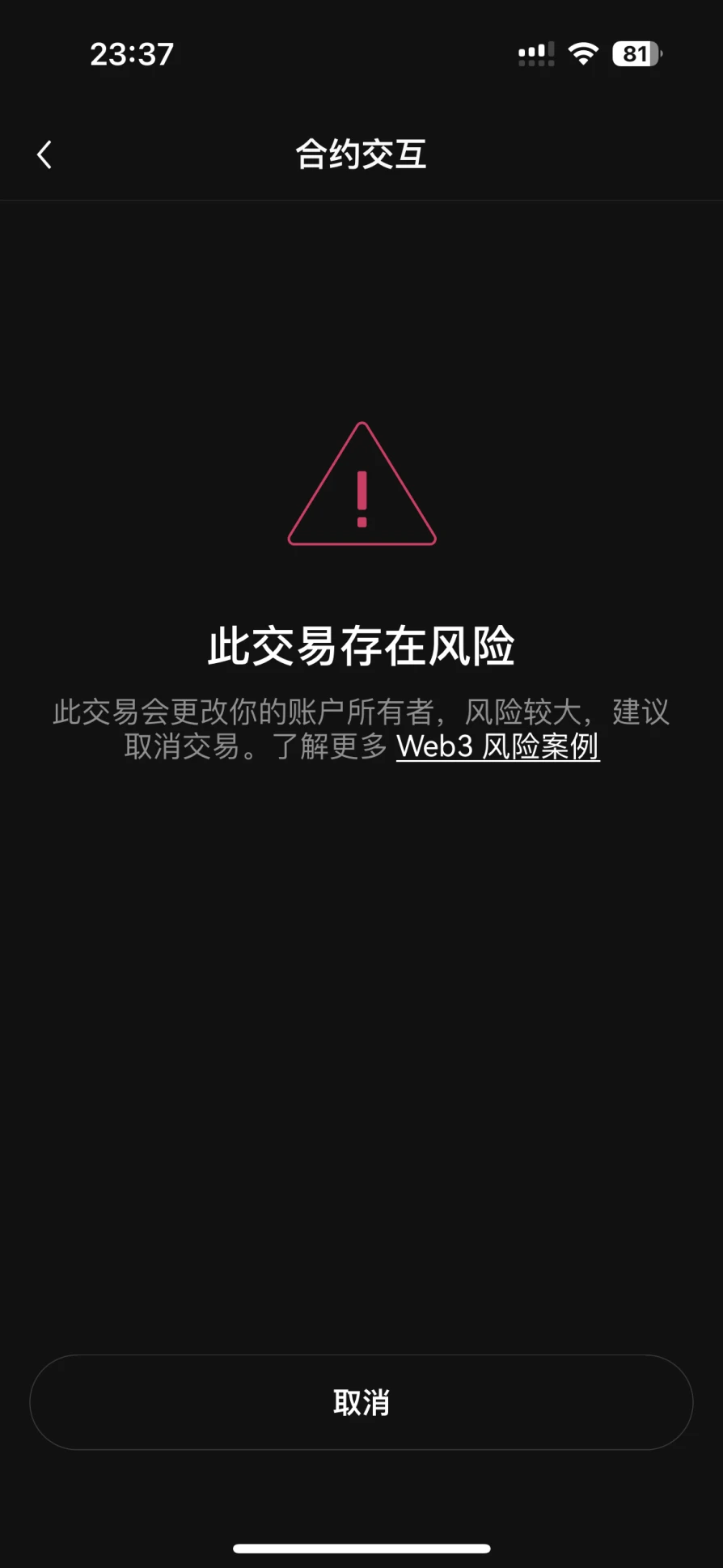
In this scenario, how does the OKX Web3 wallet interception function work?
OKX Web3 wallet performs pre-analysis on the transactions to be signed. If the analysis finds that there is any behavior of changing account permissions in the transaction, it will directly intercept the transaction for the user, preventing the user from further signing from the root, causing asset loss.
Because the risk is very high, the current OKX Web3 wallet directly intercepts it and does not allow users to conduct further transactions.
3. Malicious change of transfer address
The risky transaction scenario of maliciously changing the transfer address mainly occurs when the DApp contract design is imperfect.
On March 5, @CyversAlerts detected that the address starting with 0x ae 7 ab received 4 stETH from EigenLayer, with a contract value of 14,199.57 USD, which was suspected to be a phishing attack. At the same time, he pointed out that many victims have signed the queueWithdrawal phishing transaction on the mainnet.
Angel Drainer targeted the nature of Ethereum staking. The approval of transactions is different from the regular ERC 20 approval method. It specifically wrote an exploit for the queueWithdrawal (0x f 123991 e) function of the EigenLayer Strategy Manager contract. The core of the attack is that the user who signed the queueWithdrawal transaction actually approved the malicious withdrawer to withdraw the staking rewards of the wallet from the EigenLayer protocol to an address of the attackers choice. Simply put, once you approve the transaction on the phishing page, the rewards you staked in EigenLayer will belong to the attacker.
To make it more difficult to detect malicious attacks, the attackers used the CREATE 2 mechanism to approve these withdrawals to empty addresses. Since this is a new approval method, most security providers or internal security tools do not parse and validate this approval type, so in most cases it is marked as a benign transaction.
This is not the only case. Since this year, some mainstream public chain ecosystems have seen some imperfectly designed contract loopholes that have caused some users transfer addresses to be maliciously changed, resulting in financial losses.
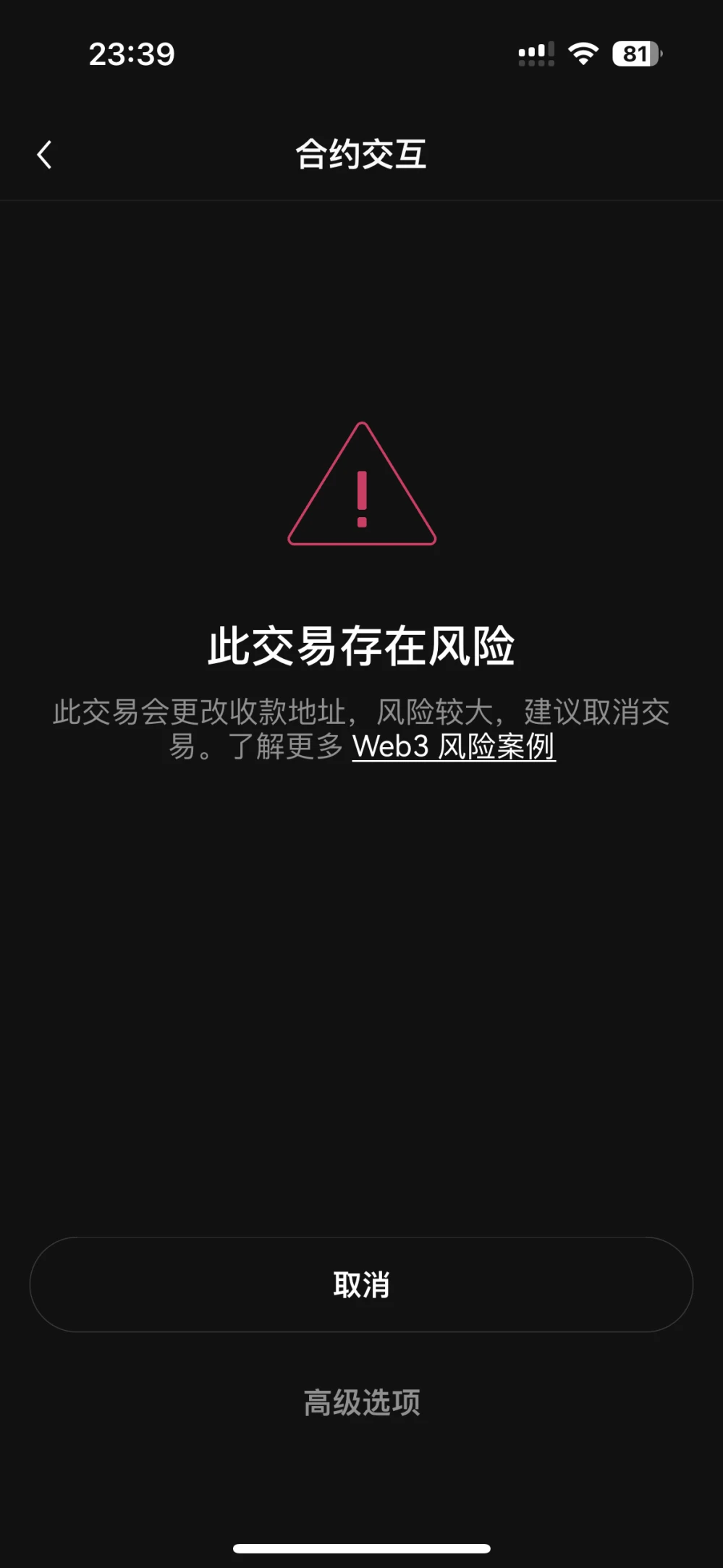
In this scenario, how does the OKX Web3 wallet interception function work?
In response to the EigenLayer phishing attack scenario, the OKX Web3 wallet will parse the related transactions of queueWithdrawal. If it is found that the user is trading on an unofficial website and withdrawing money to an address other than the users own, the user will be warned and forced to further confirm to prevent phishing attacks.
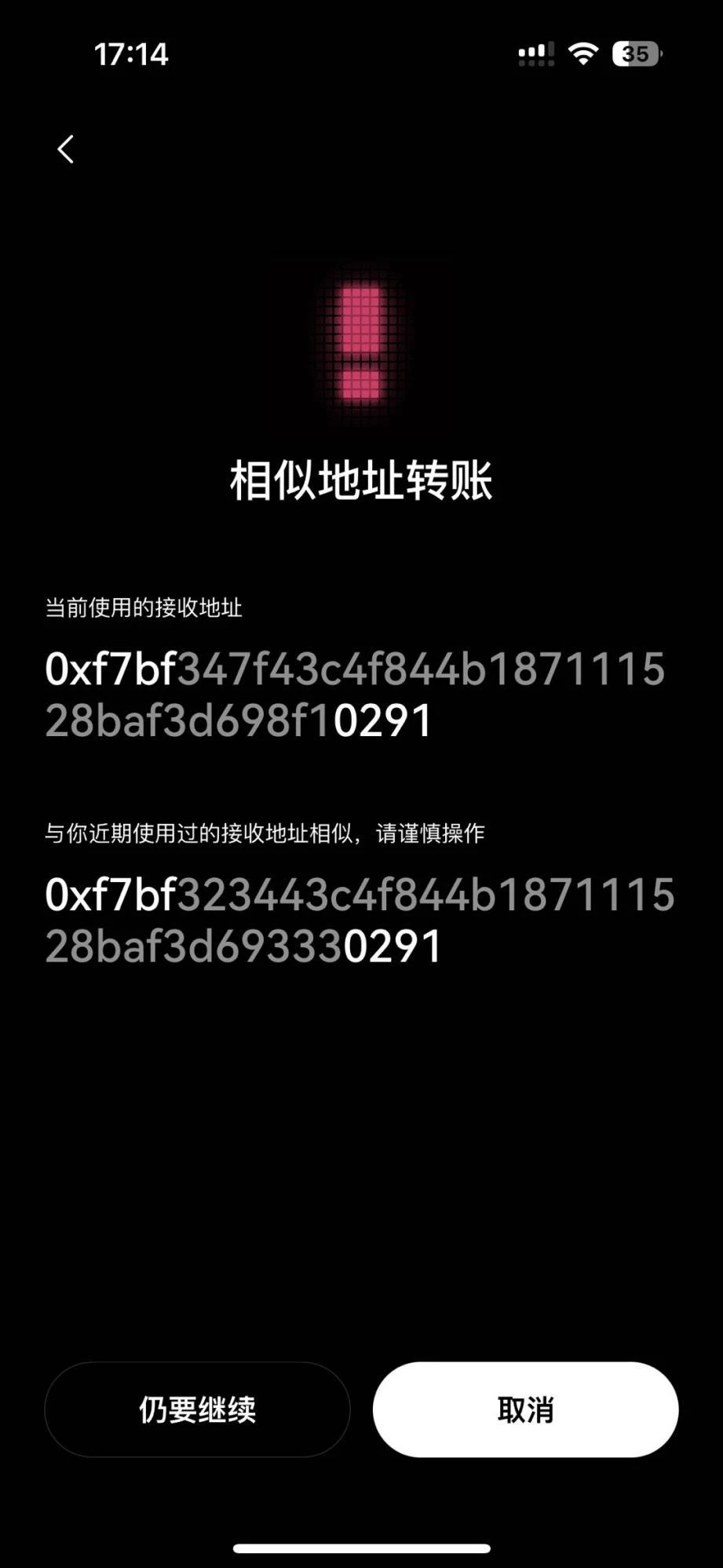
4. Transfers to Similar Addresses
The attack method of similar address transfer is to deceive the victim into using a fake address that is very similar to their real address, so that the funds are transferred to the attackers account. These attacks are usually accompanied by complex obfuscation and concealment techniques. The attacker uses multiple wallets and cross-chain transfers to increase the difficulty of tracking.
On May 3, a whale suffered a phishing attack with the same address with the same first and last numbers, and 1,155 WBTC worth about 70 million US dollars were phished away.
The logic of the attack is that the hacker generates a large number of phishing addresses in batches in advance. After the batch program is distributed and deployed, the hacker launches a phishing attack with the same first and last digits to the target transfer address based on the dynamics of the users on the chain. In this incident, the hacker used an address whose first 4 digits and last 6 digits after removing 0x are the same as the victims target transfer address. After the user transfers the money, the hacker immediately uses the phishing address that is collided (about 3 minutes later) to follow a transaction (the phishing address transfers 0 ETH to the users address), so that the phishing address appears in the users transaction record.
Because users are accustomed to copying recent transfer information from the wallet history, after seeing this trailing phishing transaction, they did not carefully check whether the address they copied was correct, and as a result, 1,155 WBTC were mistakenly transferred to the phishing address.
In this scenario, how does the OKX Web3 wallet interception function work?
OKX Web3 wallet continuously monitors transactions on the chain. If it finds that a suspicious transaction not triggered by the user occurs on the chain shortly after a large transaction occurs, and the interacting party of the suspicious transaction is extremely similar to the interacting party of the large transaction, the interacting party of the suspicious transaction will be determined to be a similar address.
If the user subsequently interacts with similar addresses, OKX Web3 will intercept and remind them; at the same time, transactions related to similar addresses will be directly marked on the transaction history page to prevent users from being induced to paste and cause financial losses. (Currently supports 8 chains)
Phần kết luận
In general, in the first half of 2024, security incidents such as airdrop phishing emails and hacking of official project accounts are still frequent. While users enjoy the benefits brought by these airdrops and activities, they are also facing unprecedented security risks. Hackers use means such as disguised as official phishing emails and fake addresses to trick users into leaking private keys or making malicious transfers. In addition, some official project accounts have also been hacked, resulting in user fund losses. For ordinary users, in such an environment, the most important thing is to raise awareness of prevention and in-depth learning of security knowledge. At the same time, try to choose a platform with reliable risk control.
Cảnh báo rủi ro và Tuyên bố miễn trừ trách nhiệm
Bài viết này chỉ mang tính chất tham khảo. Bài viết này chỉ đại diện cho quan điểm của tác giả và không đại diện cho lập trường của OKX. Bài viết này không nhằm mục đích cung cấp (i) lời khuyên đầu tư hoặc khuyến nghị đầu tư; (ii) lời đề nghị hoặc chào mời mua, bán hoặc nắm giữ tài sản kỹ thuật số; (iii) tư vấn tài chính, kế toán, pháp lý hoặc thuế. Chúng tôi không đảm bảo tính chính xác, đầy đủ hoặc hữu ích của những thông tin đó. Việc nắm giữ tài sản kỹ thuật số (bao gồm cả stablecoin và NFT) có rủi ro cao và có thể dao động đáng kể. Bạn nên cân nhắc cẩn thận xem việc giao dịch hoặc nắm giữ tài sản kỹ thuật số có phù hợp với mình hay không dựa trên tình hình tài chính của bạn. Vui lòng tham khảo ý kiến của các chuyên gia pháp lý/thuế/đầu tư cho tình hình cụ thể của bạn. Vui lòng chịu trách nhiệm hiểu và tuân thủ các luật và quy định hiện hành của địa phương.
This article is sourced from the internet: Fighting phishing: Understand the four risky transaction blocking functions of OKX Web3 wallet in one article







