This article Hash (SHA 1): 4f5b9f376aa53c6cccca03a2ddd065a59550d73c
No.: Lianyuan Security No.003
On July 3, 2024, the bug bounty platform OpenBounty was revealed to have published unauthorized vulnerability reports on the public chain. This behavior is extremely irresponsible and disrespectful to every infrastructure and security researcher involved in the list. At the same time, because the total bounty value of all vulnerabilities this time exceeded 11 billion US dollars, it also triggered a certain discussion among the entire public group, making the bug bounty platform well-known to the public. The ChainSource Security Team conducted a security analysis and partial disclosure of this leak, hoping to help readers interpret the details and better understand the existence of bug bounty platforms.
Related Information
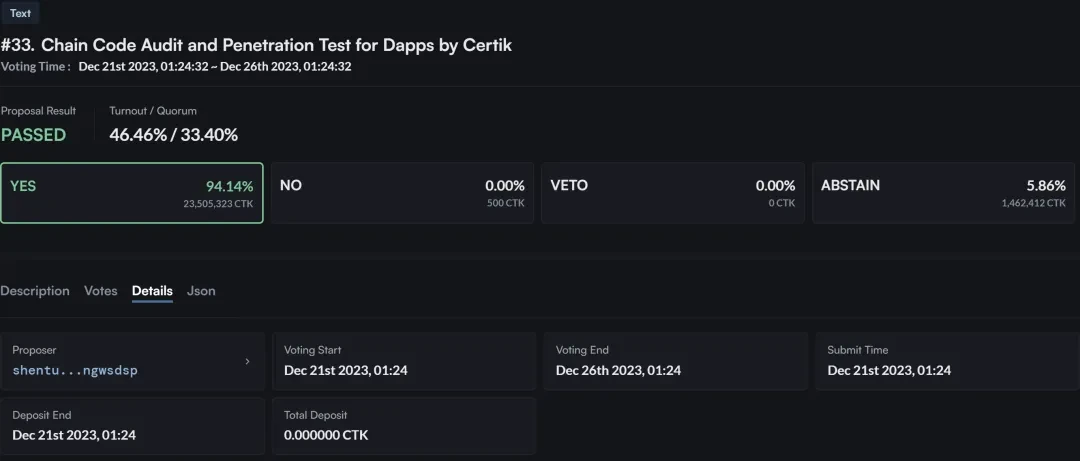
OpenBounty privately disclosed vulnerability report information on the SEHNTU public chain (the relevant proposals on Ethereum have now been deleted):
https://www.mintscan.io/shentu/proposals
https://explorer.shentu.technology/more/proposal
Bug Bounty/Exploitation
The vulnerability bounty platform in the on-chain world is very similar to the hole-hunting platform in traditional network security. The main purpose of both is to attract security researchers and white hat hackers to find and report vulnerabilities in the system through a reward mechanism, thereby improving overall security.
Their operating model is as follows in terms of timeline:
(1) Project-initiated challenges: Both blockchain projects and traditional network applications will launch vulnerability bounty programs on the platform.
(2) Vulnerability reporting: Security researchers and hackers detect project codes or systems and submit detailed reports after discovering vulnerabilities.
(3) Verification and repair: The project team verifies the vulnerabilities in the report and repairs them.
(4) Reward Distribution: After the repair is completed, the discoverer will be given a corresponding reward based on the severity and impact of the vulnerability.
Traditional network security mainly focuses on vulnerabilities in traditional IT such as Web applications, servers, and network devices, such as XXS[ 1 ], SQL injection[ 2 ], CSRF[ 3 ], etc.
Blockchain security focuses more on smart contracts, protocols, and encrypted wallets, such as Sybil attacks[4], cross-chain attacks[5], and abnormal external calls.
Key Vulnerability Reports
In the vulnerability report No. 33 released by OpenBounty in violation of regulations, CertiK conducted an audit and penetration test on the SHENTU chain. From the proposal, we can see that this security test mainly aims to solve the security vulnerabilities and authorization restrictions within SHENTU.
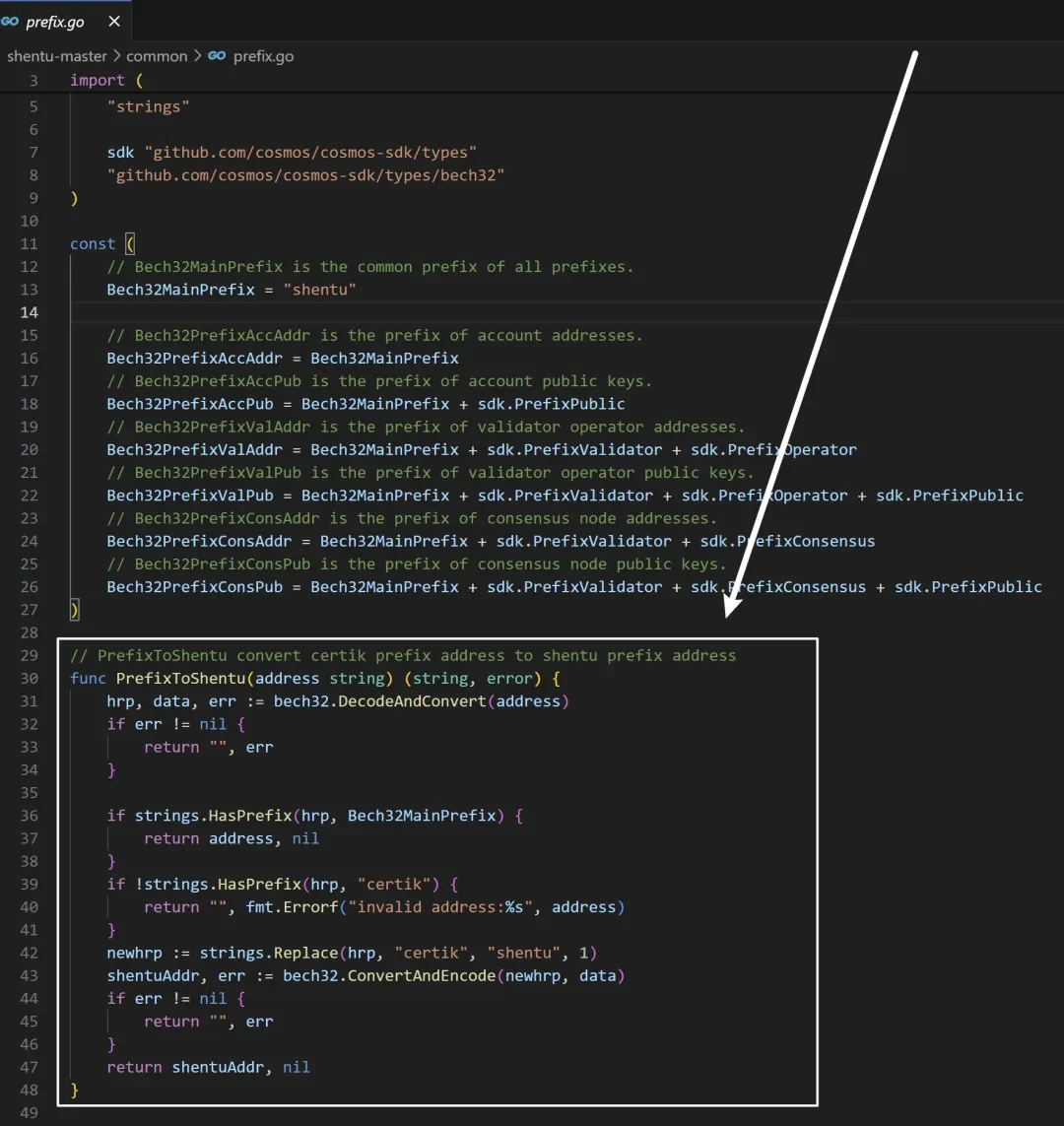
But after reading the source code of SHENTU, I found a code that replaced the prefix of CertiK with the prefix of SHENTU. Although it is understandable in development, as the domain name replacement is only for the convenience of adjustment, it does give people the feeling that CertiK is both a referee and an athlete.
In the other 32 vulnerability reports that SEHNTU has not deleted, you can see descriptions of the problem, voting parties, reward descriptions, and even the codes of each system after the vulnerability update. This unauthorized disclosure of information can easily cause secondary damage to these systems, because each system will have some historical problems or unique coding habits during the development process. For hackers, there is indeed a lot of room for exploitation of this information.
Noun interpretation
[1] XXS: The attacker injects malicious scripts into the web page, causing the script to execute when the user browses the web page. It mainly includes reflected XSS, stored XSS, and DOM XSS.
[2] SQL injection: An attack method that inserts malicious SQL code into input fields (such as forms, URL parameters) and then passes it to the database for execution. This type of attack can lead to the leakage, modification or deletion of database data, or even gain control of the database server.
[3] CSRF: An attack method that uses a users authenticated session to send unauthorized requests to a trusted site. The attacker tricks the user into visiting a specially crafted web page or clicking a link, thereby performing operations without the users knowledge, such as transferring money or modifying personal information.
[4] Sybil attack: In a distributed network, an attacker creates multiple fake identities (nodes) in an attempt to manipulate the decision-making process in the network. The attacker creates a large number of fake nodes to influence the consensus algorithm, thereby controlling transaction confirmation or blocking legitimate transactions.
[5] Cross-chain attack: Attackers can manipulate cross-chain transaction requests, bypass security checks in the contract, and steal or tamper with cross-chain transaction data, such as the Poly Network cross-chain bridge attack.
نتیجہ
In general, as OpenZepplin and HackenProof show, the management of bug bounties must be approved by the publisher. This is a legal and ethical issue that is the basis of many independent developers achievements.
لیان یوان ٹیکنالوجی ایک کمپنی ہے جو بلاک چین سیکیورٹی پر مرکوز ہے۔ ہمارے بنیادی کام میں بلاک چین سیکیورٹی ریسرچ، آن چین ڈیٹا کا تجزیہ، اور اثاثہ اور معاہدے کے خطرے سے بچاؤ شامل ہے۔ ہم نے کامیابی سے افراد اور اداروں کے بہت سے چوری شدہ ڈیجیٹل اثاثے برآمد کر لیے ہیں۔ ایک ہی وقت میں، ہم صنعتی تنظیموں کو پراجیکٹ سیکیورٹی تجزیہ رپورٹس، آن چین ٹریس ایبلٹی، اور تکنیکی مشاورت/معاون خدمات فراہم کرنے کے لیے پرعزم ہیں۔
آپ کے پڑھنے کے لیے آپ کا شکریہ۔ ہم بلاکچین سیکیورٹی مواد پر توجہ مرکوز کرنا اور اس کا اشتراک کرنا جاری رکھیں گے۔
This article is sourced from the internet: OpenBounty Rabbit Hole Time Analysis
Headlines Arkham: Vitaliks total ETH holdings are worth more than $800 million Arkham officially announced on X that the team had written a report on the personal wealth tracking of Ethereum co-founder Vitalik Buterin at the beginning of the year. At that time, the total value of Vitaliks ETH holdings was about US$500 million. With the rise of ETH, the total value of his ETH holdings has now exceeded US$800 million. Justin Sun: This year’s goal is to achieve $1 billion in TRON protocol revenue Justin Sun, founder of TRON and member of Huobi HTX Global Advisory Committee, posted on the X platform that he would set a goal this year to increase TRONs protocol revenue to US$1 billion. The SEC has returned the S-1 form to the ETH spot…