Hack VC: Blockchain gizlilik teknolojisinin gelecekteki beklentilerini keşfetmek
Original author: Duncan Nevada
Orijinal çeviri: TechFlow
Cryptography’s transparent ledger fundamentally changes our understanding of trusted systems. As the old adage goes, “Don’t trust, verify,” and transparency is what allows us to do that. If all information is public, any falsification can be identified immediately. However, this transparency also shows its limitations in terms of usability. It is true that some information should be public, such as settlement, reserves, reputation (and even identity), but we would never want everyone’s financial and health records to be public along with their personal information.
The need for privacy in blockchain
Privacy is a basic human right. Without privacy, there can be no freedom or democracy.
Just as the early Internet needed encryption technologies such as SSL to enable secure e-commerce and protect user data, blockchains need strong privacy technologies to realize their full potential. SSL enables websites to encrypt data during transmission, ensuring that sensitive information such as credit card numbers cannot be intercepted by malicious actors. Similarly, blockchains require privacy to protect transaction details and interactions while maintaining the integrity and verifiability of the underlying system.
Privacy on blockchain is not only about the protection of individual users, but is also critical to enterprise adoption, compliance with data protection regulations, and opening up new design spaces. No company wants every employee to be able to see every other employees salary, or for competitors to be able to rank their most valuable customers and poach them. In addition, industries such as healthcare and finance have strict regulatory requirements for data privacy, and blockchain solutions must meet these requirements to be viable tools.
A Framework for Privacy-Enhancing Technologies (PETs)
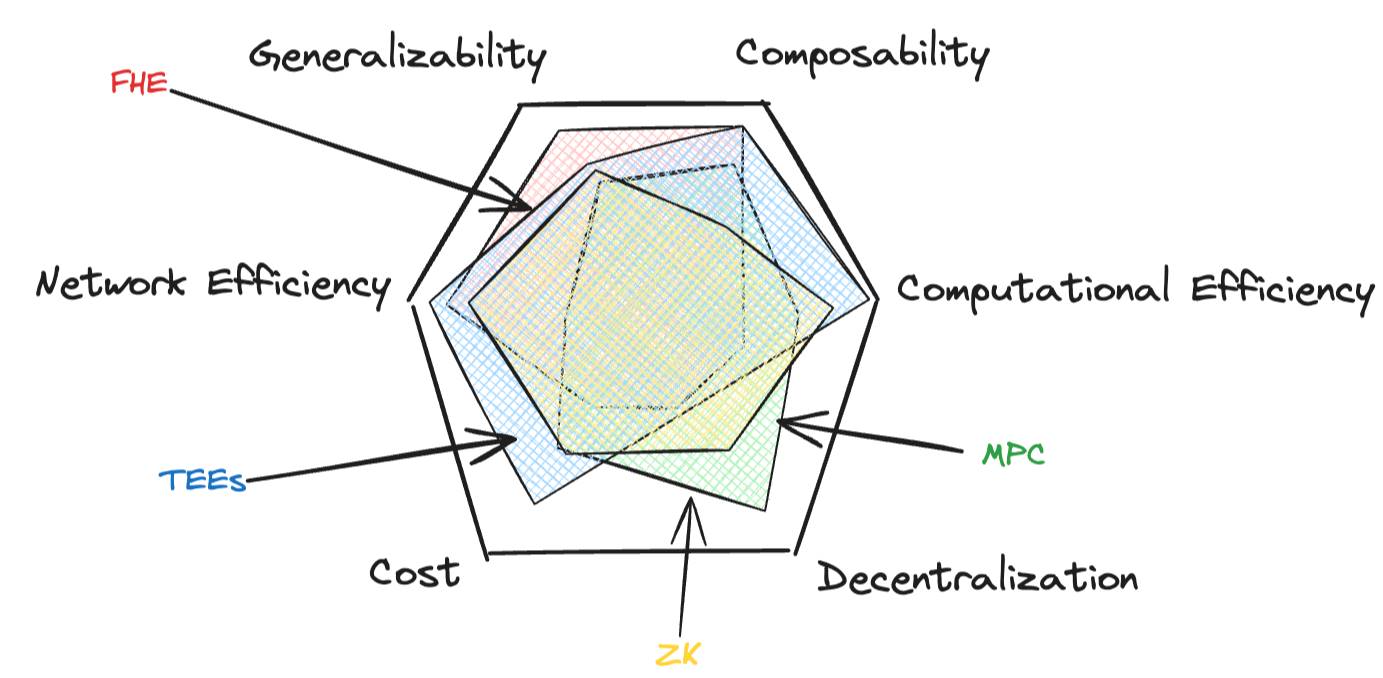
As the blockchain ecosystem develops, several key privacy-enhancing technologies (PETs) have emerged, each with its own unique advantages and trade-offs. These technologies include zero-knowledge proofs (ZK), multi-party computation (MPC), fully homomorphic encryption (FHE), and trusted execution environments (TEE), which cover six key axioms.
-
Generalizability : The applicability of the solution across a wide range of use cases and computations.
-
Combinability : How easily this technique can be combined with other techniques to mitigate shortcomings or open up new design space.
-
Computational efficiency : How efficiently a system performs computations.
-
Network efficiency : The ability of a system to scale as the number of participants or data increases.
-
Merkezi olmayan yönetim : The degree to which the security model is distributed.
-
Cost : The actual cost of privacy.
Just like the scalability, security, and decentralization trilemma facing blockchain, achieving all six properties simultaneously is a challenge. However, recent advances and hybrid approaches are pushing the boundaries of what is possible, bringing us closer to comprehensive, cost-effective, and efficient privacy solutions.
Now that we have a framework in place, we will briefly survey the field and explore the future prospects of these privacy-enhancing technologies.
Overview of Privacy-Enhancing Technologies
Here, I want to provide you with some definitions. Note: I am assuming that you are also actively reading Dune and seeing everything through the lens of Melocha!
Zero-knowledge (ZK) is a technique that allows verification that a computation has occurred and obtained a result without revealing what the inputs were.
-
Generality : Moderate. Circuits are highly application specific, but improvements are being made through hardware abstraction layers (such as Ulvatana and Irreducible) and general interpreters (Nils zkLLVM).
-
Compositionality : Moderate. It works in isolation from a trusted prover, but in a network setting the prover must see all the raw data.
-
Computational efficiency : Moderate. With real ZK applications like Leo Wallet coming online, proofs are gaining exponential improvement through novel implementations. We expect further progress as customer adoption increases.
-
Network efficiency : High. Recent advances in folding technology introduce huge potential for parallelization. Folding is essentially a more efficient way to construct iterative proofs, so it can build on previous work. Nexus is a project worth watching.
-
Merkezi olmayan yönetim : Moderate. In theory, proofs can be generated on any hardware, though in practice, GPUs are preferred here. Further decentralization is possible at the economic level through AVS like Aligned Layer, though hardware becomes more uniform. Inputs are private only when combined with other techniques (see below).
-
Cost : Moderate.
-
The initial implementation cost of circuit design and optimization is high.
-
Moderate operational costs, with proof generation expensive but verification efficient. A significant cost factor is proof storage on Ethereum, but this can be mitigated by using a data availability layer (such as EigenDA) or AVS.
-
To use an analogy from Dune: Imagine Stilgar needs to prove to Duke Leto that he knows the location of the spice fields without revealing their actual location. Stilgar takes Leto, blindfolded, in a bug-bird, flies over the spice fields until the cabin is filled with the sweet scent of cinnamon, and then takes him back to Arrakeen. Leto now knows that Stilgar can find the spices, but he doesn’t know how he’s going to find them.
Multi-party computation (MPC) is a technique that allows multiple participants to jointly compute a result without revealing their inputs to each other.
-
Versatility : High. Considers many specialized variants of MPC (such as secret sharing, etc.).
-
Compositionality : Moderate. Although MPC is secure, compositionality decreases as computational complexity increases, as complexity introduces more network overhead. However, MPC is able to handle private input from multiple users, which is a relatively common use case.
-
Computational efficiency : Moderate.
-
Network efficiency : Low. The amount of network communication required grows quadratically with the number of participants. Companies such as Nillion are working on this issue. Errors can be reduced using erasure coding or Reed-Solomon codes (i.e., splitting data into pieces and saving those pieces), although this is not a traditional MPC technique.
-
Merkezi olmayan yönetim : High. Although there is a possibility of collusion between participants, which could compromise security.
-
Cost : High.
-
The implementation cost is moderate to high.
-
The operating cost is high due to communication overhead and computational requirements.
-
To use an analogy from Dune: imagine the great families of Landsraad make sure they have enough spice reserves to help each other out when needed, but they dont want to reveal how much each family has. The first family can send a message to the second family to add a large random number to their actual reserves. The second family then adds their actual reserves, and so on. When the first family receives the final total, they simply subtract that large random number to get their actual total spice reserves.
Fully homomorphic encryption (FHE) allows computations to be performed on encrypted data without first decrypting it.
-
Versatility : High.
-
Composability : High for single-user input. Must be combined with other techniques for private input from multiple users.
-
Computational efficiency : Low. Although progress in both the mathematical and hardware layers is being made, this will be a huge breakthrough. Zama and Fhenix have done a lot of excellent work in this regard.
-
Network efficiency : High.
-
Merkezi olmayan yönetim : Low. This is partly due to computational requirements and complexity, but as the technology improves, FHE’s decentralization will likely approach that of ZK.
-
Cost : Very high.
-
High implementation cost due to complex encryption and strict hardware requirements.
-
The operating cost is high due to intensive computation.
-
To use an analogy from Dune: imagine a device similar to the Holtzmann shield, but for numbers. You can put digital data into this shield, activate it, and then give it to a Mentat. The Mentat can calculate on those numbers without seeing them. When they are done, they return the shield to you. Only you can close the shield and see the results of the calculations.
A Trusted Execution Environment (TEE) is a secure zone within a computer processor that allows sensitive operations to be executed in isolation from the rest of the system. TEEs are unique in that they rely on silicon and metals, rather than polynomials and curves. So while they may be a powerful technology today, they may theoretically be slower to improve due to the limitations of expensive hardware.
-
Versatility : Medium.
-
Compositionality : High. Although less secure due to possible side-channel attacks.
-
Computational efficiency : High. Approaching server-side efficiency, so much so that NVIDIAs new H100 chipset series is equipped with a TEE.
-
Network efficiency : High.
-
Merkezi olmayan yönetim : Low. Although limited to specific chipsets (such as Intels SGX), this means that it may be vulnerable to side-channel attacks.
-
Cost : Low.
-
The implementation cost is low if existing TEE hardware is used.
-
Low operating costs due to close to local performance.
-
To use an analogy from Dune: imagine a navigation cabin for the space guild Heighliner. Even the guilds own navigators cannot see or interfere with what goes on inside when its in use. The navigators enter this cabin and perform the complex calculations required to fold space, while the cabin itself ensures that all operations remain private and secure. The guild provides and maintains this cabin and keeps it safe, but they cannot see or interfere with the navigators work inside.
Practical application cases
Rather than fighting the spice cartels, perhaps we would be better off ensuring that sensitive data, such as key material, remains private. To contextualize this with reality, here are some real-world use cases for each technology.
Zero-knowledge proofs (ZK) are good for verifying that a process produced the correct result. It is an excellent privacy-preserving technique when used in conjunction with other techniques, but sacrifices trustlessness when used alone, more like data compression. We often use it to verify that two states are the same, such as comparing an uncompressed second-layer state to a block header published to the first layer, or proving that a user is over 18 years old without revealing the users actual personally identifiable information.
Multi-party computation (MPC) is often used for key management, including private or decryption keys, which can be used in conjunction with other technologies. In addition, MPC is also used for distributed random number generation, small confidential computing operations, and oracle aggregation. In general, any scenario that requires multiple participants who should not collude to perform lightweight aggregate computations is very suitable for using MPC.
Fully homomorphic encryption (FHE) is suitable for performing simple, common computations without the computer being able to see the data, such as credit scoring, Mafia in smart contract games, or sequencing transactions without revealing their contents.
Nihayet, Trusted Execution Environments (TEEs) are suitable for more complex operations, provided you are willing to trust the hardware. For example, this is the only viable solution for private base models (large language models that exist in enterprises or financial, medical, or national security agencies). Since TEEs are the only hardware-based solution, mitigation of its shortcomings should theoretically be slower and more expensive than other technologies.
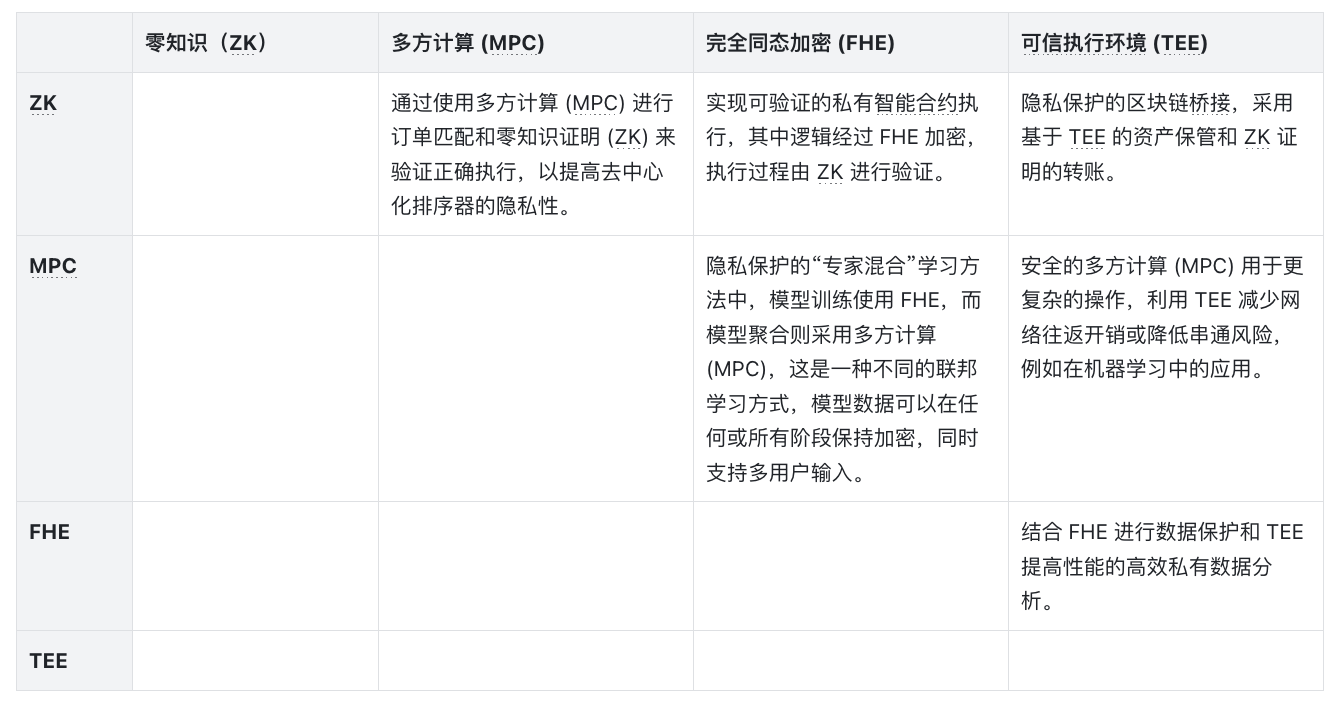
In between
Obviously, there is no perfect solution, and it is unlikely that any one technology will be the perfect solution. Hybrid approaches are exciting because they may leverage the strengths of one technology to compensate for the weaknesses of another. The table below shows some of the design space that can be unlocked by combining different approaches. The actual approaches vary greatly, for example, combining ZK and FHE may require finding the right curve parameters, while combining MPC and ZK may require finding some kind of setting parameters to reduce the final number of network round trips. Hopefully this provides some inspiration if you are building something and want to discuss.
In short, good, scalable privacy technology unlocks countless applications, including gaming (hat tip to Baz’s Tonk for the great write-up), governance, fairer transaction lifecycles (Flashbots), identity (Lit), non-financial services (Oasis), collaboration and coordination. This is one of the reasons we’re excited about Nillion, Lit Protocol, and Zama.
Sonuç olarak
In summary, we see great potential for the application of privacy-enhancing technologies (PETs), but we are still in the early stages of exploring the possibilities. While the various technologies may gradually mature, the overlapping applications of technologies are still an area worth exploring in depth. The application of these technologies will be tailored to specific areas, and as an industry, we still have a lot of work to do.
This article is sourced from the internet: Hack VC: Exploring the future prospects of blockchain privacy technology
In the past week, the market has successfully digested the shipments of various whales and successfully hit the pressure level. How will the market perform next? Recently, weak US economic data has raised expectations for interest rate cuts. Fed Chairman Powell has released dovish signals at hearings for two consecutive days, and the US economy has shown signs of fatigue. Ethereum spot ETF is about to land, and Bitcoin has regained its upward momentum this week. After initially bottoming out at $53,000, it has continued to rebound, and the market has once again called for the slogan of copycat carnival. We believe that if Bitcoin can stand firm at the $60,000 mark, it will rebuild market confidence and is expected to return to the high of $70,000 in the short…