I. Overview
The losses caused by hacker attacks, phishing attacks, and Rugpull scams in the first half of 2024 were approximately $1.492 billion, a year-on-year increase of 116.23% compared to the first half of 2023 (approximately $690 million). This report aims to analyze the global Web3 industry security status, hot events, and key regulatory policies in the first half of 2024. We hope that this report will provide readers with useful information and ideas and contribute to promoting the safe and healthy development of Web3.
2. Trend Analysis
According to data from SharkTeams on-chain intelligent risk identification platform ChainAegis, a total of 551 security incidents occurred in the Web3 field in the first half of 2024 (as shown in Figure 1), with a cumulative loss of more than US$1.492 billion (as shown in Figure 2). Compared with the same period last year, the number of security incidents increased by 25.51% and the amount of losses increased by 116.23%.
Figure 1 Total Count of Security Incidents in 2024 H 1
Figure 2 Total Loss of Security Incidents in 2024 H 1
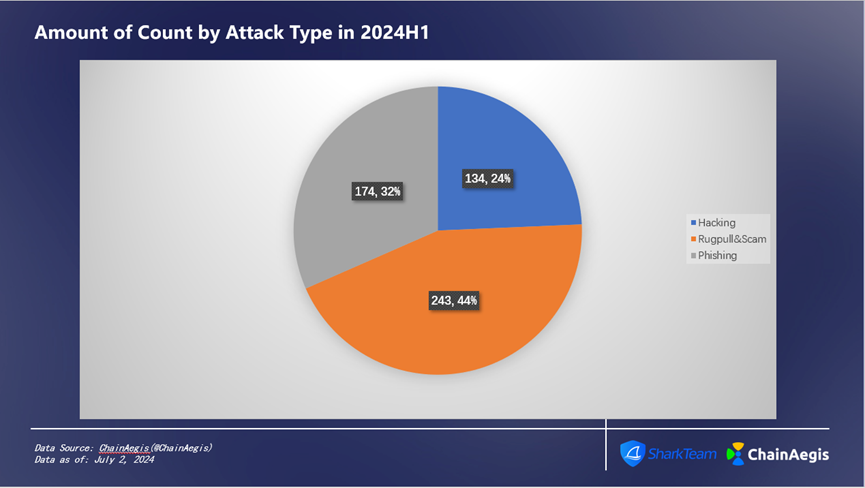
In the first half of 2024, there were a total of 134 hacker attack-type security incidents, an increase of 103.03% compared with H1 2023. The amount of losses reached US$1.08 billion, accounting for 73% (as shown in Figure 3), an increase of 147.71% year-on-year compared with H1 2023 (US$436 million).
There were a total of 243 rug pull incidents in the first half of the year, a surge of 331.15% compared to the 61 incidents in H1 2023, and the amount of losses increased by 258.82%, totaling US$122 million, accounting for 8% of the total H1 loss amount.
There were 174 phishing attacks in total in H1, up 40.32% year-on-year, with losses amounting to $290 million, accounting for 19%.
Figure 3 Amount of Loss by Attack Type in 2024 H 1
Figure 4 Amount of Count by Attack Type in 2024 H 1
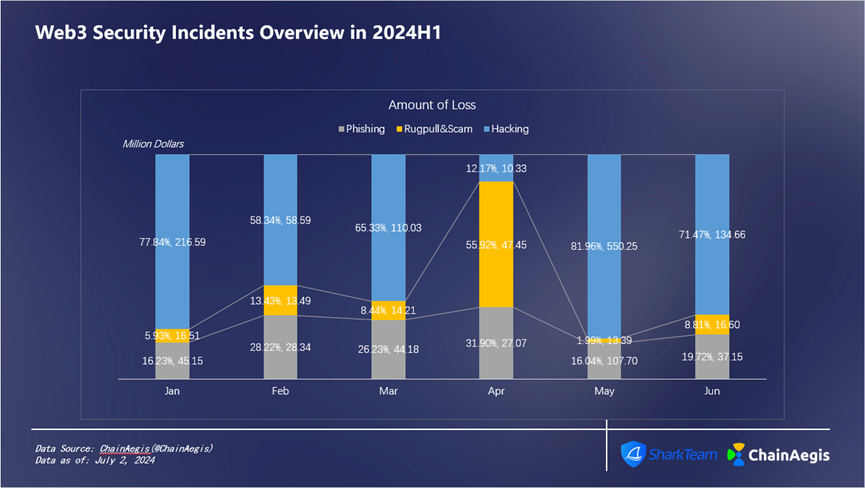
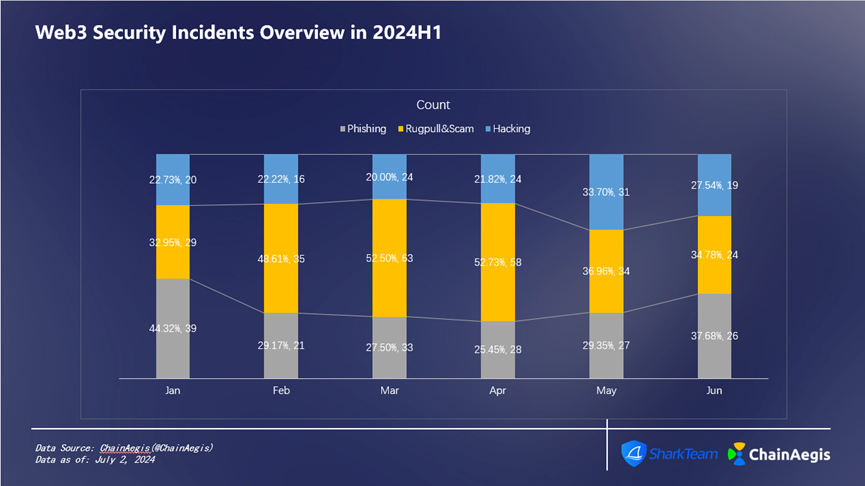
Looking at the monthly data in H1 (see Figure 5 and Figure 6), the loss in May was the most serious, about US$643 million, with 92 security incidents, including 31 hacker attacks, 34 Rugpull incidents, and 27 phishing attacks.
Figure 5 Web3 Security Incidents Loss Overview in 2024 H 1
Figure 6 Web3 Security Incidents Count Overview in 2024 H 1
2.1 Hacker Attacks
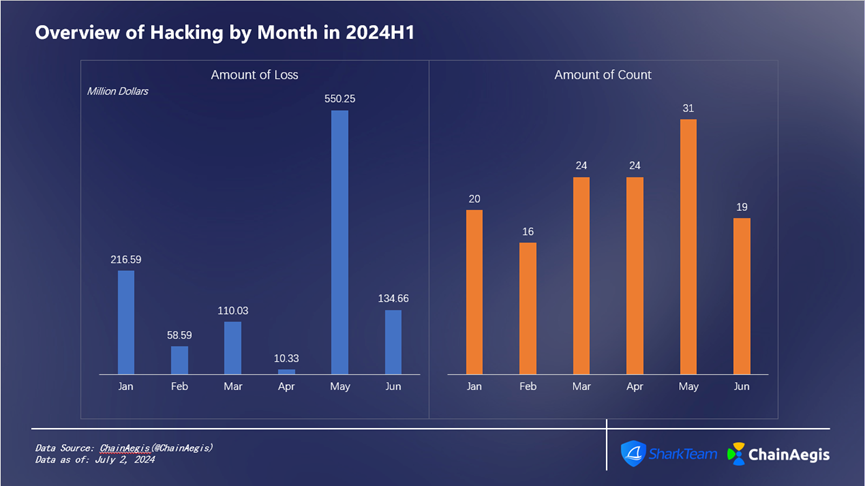
There were 134 hacker attacks in the first half of the year, with a total loss of $1.08 billion. (See Figure 7 for specific data)
On May 21, 2024, the Gala Games protocol on Ethereum was hacked, resulting in a loss of $21.8 million. After the attack, the project took immediate action and blacklisted the hackers address, freezing the authority to sell more tokens.
On May 31, 2024, a huge unauthorized outflow of Bitcoin occurred at DMM Bitcoin Exchange, a subsidiary of Japanese securities company DMM.com. The outflow amount was approximately 48 billion yen (approximately US$300 million), which was the seventh largest cryptocurrency attack in history and the largest attack since December 2022.
Figure 7 Overview of Hacking by Month in 2024 H 1
2.2 Rugpull Scams
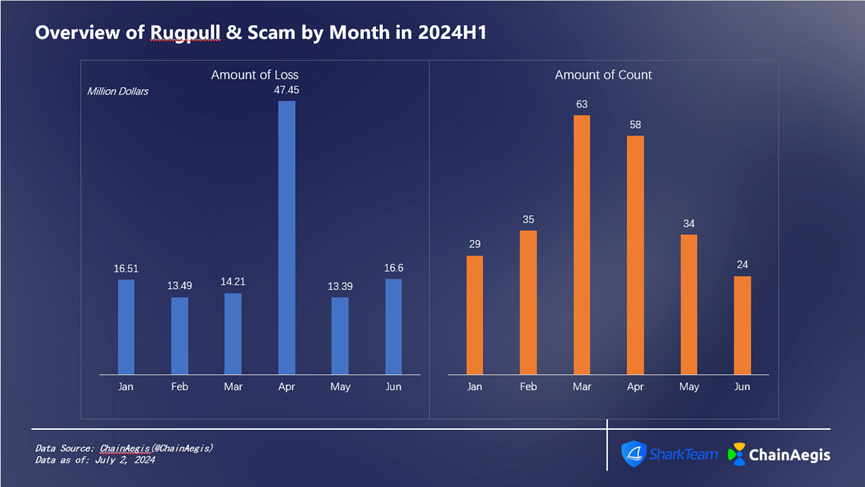
As shown in the figure below (Figure 8), the frequency of Rugpull Scam incidents was as high as 63 in March, and the lowest frequency was in June, with a total of 24 incidents; the loss amount was the highest in April, about 47.45 million US dollars, among which the ZKasino project owner running away was the main reason for the highest loss in April.
Figure 8 Overview of RugpullScam by Month in 2024 H 1
2.3 Phishing Attacks
As shown in the figure below (Figure 9), phishing attacks occurred most frequently in January with 39 incidents, causing losses of approximately $44.15 million; the lowest frequency occurred in February with 21 incidents, causing losses of approximately $28.34 million. Although there were only 27 phishing incidents in May, the amount of losses was the highest in the first half of the year, reaching $108 million. Among them, on May 3, 2024, a user was phished for 1,155 WBTC due to address pollution phishing techniques, worth more than $70 million.
Figure 9 Overview of Phishing by Month in 2024 H 1
3. Typical Case Analysis
3.1 Analysis of Sonne Finance Attack
On May 15, 2024, Sonne Finance was attacked and the project lost more than 20 million US dollars.
Attacker: 0xae4a7cde7c99fb98b0d5fa414aa40f0300531f43
Attack transaction:
0x9312ae377d7ebdf3c7c3a86f80514878deb5df51aad38b6191d55db53e42b7f0
Saldırı süreci şu şekilde işliyor:
1. Flash loan 35,569,150 VELO and transfer these VELO Tokens to the soVELO contract
Because it is a direct transfer (donation), no soVELO Token is minted. Therefore, in the soVELO contract, totalCash increases by 35,569,150 VELO, and soVELOs totalSupply remains unchanged.
2. The attacker creates a new contract 0xa16388a6210545b27f669d5189648c1722300b8b and launches an attack on the target contract in the new contract. The attack process is as follows:
(1) Transfer 2 soVELO to the new contract
(2) Declare soWETH and soVELO as collateral
(3) Borrowed 265, 842, 857, 910, 985, 546, 929 WETH from soWETH
From the execution process of the above borrow function, according to the return value of the getAccountSnapshot function, we find that:
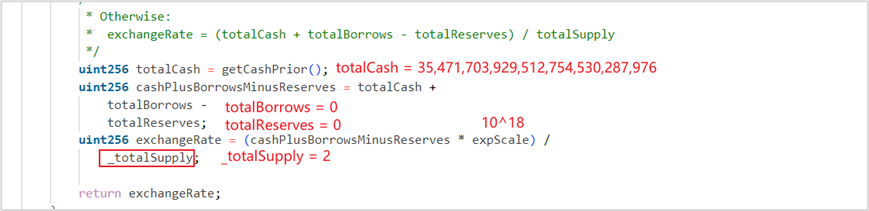
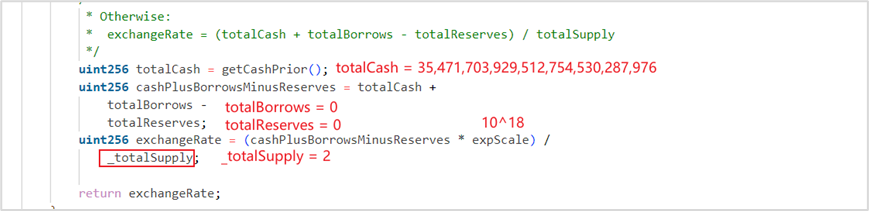
For the soWETH contract, the new contract balance is 0, the loan amount is 0, and the exchange rate is 208, 504, 036, 856, 714, 856, 032, 085, 073
For the soVELO contract, the new contract balance is 2, which means 2 wei of soVELO is pledged, the loan amount is 0, and the exchange rate is 17, 735, 851, 964, 756, 377, 265, 143, 988, 000, 000, 000, 000, 000, 000
exchangeRate is calculated as follows:
With 1 wei of soVELO as collateral, you can borrow no more than 17, 735, 851, 964, 756, 377, 265, 143, 988 VELO. To borrow 265, 842, 857, 910, 985, 546, 929 WETH, you need to pledge at least 265, 842, 857, 910, 985, 546, 929 soWETH,
soWETHPrice = 2,892,868,789,980,000,000,000,
soVELOPrice = 124,601,260,000,000,000
The amount of WETH that can be borrowed by pledging 1 wei of soVELO is as follows:
1 * exchangeRate * soVELOPrice / soWETHPrice = 763, 916, 258, 364, 900, 996, 923
About 763 WETH. Only 1 wei of soVELO collateral is enough to support this loan.
Borrow 265, 842, 857, 910, 985, 546, 929 WETH (about 265 WETH) and convert it into collateral soVELO. The minimum amount of soVELO required for collateral is:
265, 842, 857, 910, 985, 546, 929 * soWETHPrice / soVELOPrice / exchangeRate = 0.348
That is, 1 wei of soVELO collateral will suffice.
In fact, only 1 wei of the 2 wei soVELO collateral was used for lending.
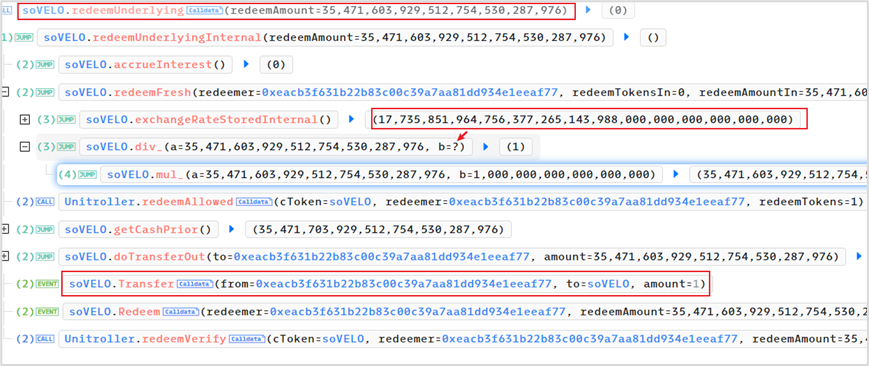
(4) Redemption of underlying assets, i.e. 35, 471, 603, 929, 512, 754, 530, 287, 976 VELO
exchangeRate = 17, 735, 851, 964, 756, 377, 265, 143, 988, 000, 000, 000, 000, 000, 000
The amount of collateral soVELO required to redeem 35, 471, 603, 929, 512, 754, 530, 287, 976 VELO is
35, 471, 603, 929, 512, 754, 530, 287, 976 * 1 e 18 / exchangeRate = 1.99999436
When calculating, because the calculation uses truncation instead of rounding, the actual required collateral is 1 wei of soVELO.
The actual collateral is 2 wei of soVELO, of which 1 wei is used to borrow 265 WETH above, and the remaining 1 wei is used to redeem 35M VELO
(5) Transfer the borrowed 265 WETH and redeemed 35M VELO to the attack contract
3. Create a new contract 3 times (4 times in total) and repeat the attack.
4. Finally, repay the flash loan.
5. Vulnerability Analysis
The above attack exploits two vulnerabilities:
(1) Donation attack: Directly transfer (donate) VELO Token to the soVELO contract, changing the exchangeRate, allowing the attacker to borrow approximately 265 WETH with only 1 wei soVELO as collateral.
(2) Calculation accuracy problem: By taking advantage of the accuracy loss in the calculation process and the modified exchangeRate, 35M VELO can be redeemed with only 1 wei soVELO pledged.
6. Safety Recommendations
In response to this attack, we should follow the following precautions during development:
(1) During the design and development process of the project, the integrity and rigor of the logic must be maintained, especially in the areas of deposits, pledges, updating of status variables, and the trade-offs of multiplication and division results during calculations. As many situations as possible should be considered to ensure that the logic is complete and has no loopholes.
(2) Proje çevrimiçi hale getirilmeden önce, üçüncü taraf bir profesyonel denetim şirketinin akıllı sözleşme denetimi yapması gerekiyor.
3.2 Analysis of common Web3 phishing methods and security recommendations
Web3 phishing is a common attack method against Web3 users. It steals users authorization and signatures through various means, or induces users to make erroneous operations, with the aim of stealing the encrypted assets in users wallets.
In recent years, Web3 phishing incidents have continued to occur, and a black industry chain of Drainer as a Service (DaaS) has developed, posing a severe security situation.
In this article, SharkTeam will conduct a systematic analysis of common Web3 phishing methods and provide security prevention suggestions for your reference, hoping to help users better identify phishing scams and protect the security of their own encrypted assets.
-
Permit off-chain signature phishing
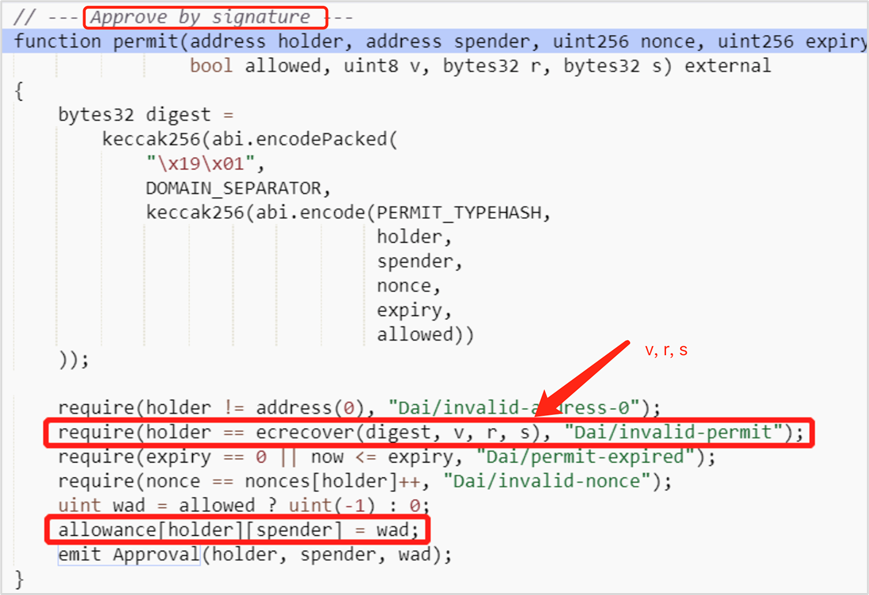
Permit is an extended function for authorization under the ERC-20 standard. In simple terms, you can sign to approve other addresses to move your tokens. The principle is that you use your signature to indicate that the authorized address can use your tokens through this signature, and then the authorized address uses your signature to interact with the on-chain permit to obtain the call authorization and transfer your assets. Permit off-chain signature phishing is usually divided into three steps:
(1) The attacker forges a phishing link or phishing website to trick the user into signing through the wallet (without contract interaction and not on the chain).
(2) The attacker calls the permit function to complete the authorization.
(3) The attacker calls the transferFrom function to transfer the victim’s assets, completing the attack.
Here we first explain the difference between transfer and transferFrom. When we transfer ERC 20 directly, we usually call the transfer function in the ERC 20 contract, and transferFrom is usually used when authorizing a third party to transfer the ERC 20 in our wallet to other addresses.
This signature is a Gas-free off-chain signature. After the attacker obtains it, he will perform the permit and transferFrom on-chain interactions. Therefore, the authorization record cannot be seen in the on-chain record of the victims address, but can be seen in the attackers address. Generally speaking, this signature is one-time and will not be repeated or continue to generate phishing risks.
-
Permit 2 Off-chain Signature Phishing
Permit 2 is a smart contract launched by Uniswap at the end of 2022 for the convenience of users. It is a token approval contract that allows token authorization to be shared and managed in different DApps. In the future, as more and more projects integrate with Permit 2, the Permit 2 contract can achieve a more unified authorization management experience in the DApp ecosystem and save user transaction costs.
Before the emergence of Permit 2, token exchange on Uniswap required authorization (Approve) and then exchange (Swap), which required two operations and also required the gas fee of two transactions. After the launch of Permit 2, users authorized the entire amount to Uniswaps Permit 2 contract at one time, and each subsequent exchange only required an off-chain signature.
Although Permit 2 improves the user experience, it is followed by phishing attacks against Permit 2 signatures. Similar to Permit off-chain signature phishing, Permit 2 is also off-chain signature phishing. This attack is mainly divided into four steps:
(1) The prerequisite is that the user’s wallet has used Uniswap before being phished and authorized the token amount to Uniswap’s Permit 2 contract (Permit 2 will allow the user to authorize the entire balance of the token by default).
(2) The attacker forges a phishing link or phishing page to induce the user to sign. The phishing attacker obtains the required signature information, which is similar to the Permit off-chain signature phishing.
(3) The attacker calls the permit function of the Permit 2 contract to complete the authorization.
(4) The attacker calls the transferFrom function of the Permit 2 contract to transfer the victim’s assets and complete the attack.
Here, the attacker usually has multiple addresses to receive assets. Usually, the recipient with the largest amount is the attacker who carries out phishing, and the others are black market addresses that provide phishing as a service (the supplier addresses of phishing as a service DaaS, such as PinkDrainer, InfernoDrainer, AngelDrainer, etc.).
-
eth_sign on-chain blind signature phishing
eth_sign is an open signature method that can sign any hash. An attacker only needs to construct any malicious data that needs to be signed (such as token transfers, contract calls, obtaining authorization, etc.) and induce users to sign through eth_sign to complete the attack.
MetaMask will have a risk warning when performing eth_sign signing. Web3 wallets such as imToken and OneKey have disabled this function or provided risk warnings. It is recommended that all wallet manufacturers disable this method to prevent users from being attacked due to lack of security awareness or necessary technical accumulation.
-
personal_sign/signTypedData On-chain signature phishing
personal_sign and signTypedData are commonly used signature methods. Usually, users need to carefully check whether the initiator, domain name, signature content, etc. are safe. If there are risks, be extra vigilant.
In addition, if personal_sign and signTypedData are used as blind signatures as in the above case, users cannot see the plain text, which can be easily exploited by phishing gangs and increase the risk of phishing.
-
Authorized fishing
Attackers forge malicious websites or put Trojans on the official website of the project to trick users into confirming operations such as setApprovalForAll, Approve, Increase Approval, and Increase Allowance, thereby obtaining users asset operation authorization and stealing them.
-
Address pollution phishing
Address pollution phishing is also one of the phishing methods that has been rampant recently. The attacker monitors on-chain transactions and then forges malicious addresses based on the counterparty addresses in the target users historical transactions. Usually, the first 4 to 6 digits and the last 4 to 6 digits are the same as the correct counterparty address. These malicious forged addresses are then used to make small transfers or worthless token transfers to the target users address.
If the target user copies the counterparty address from historical transaction orders for transfer in subsequent transactions due to personal habit, it is very likely that the assets will be transferred to a malicious address by mistake due to carelessness.
On May 3, 2024, 1,155 WBTC worth more than 70 million U.S. dollars were phished due to the pollution phishing method of this address.
Correct address: 0xd9A1b0B1e1aE382DbDc898Ea68012FfcB2853a91
Malicious address: 0xd9A1C3788D81257612E2581A6ea0aDa244853a91
Normal transaction:
https://etherscan.io/tx/0xb18ab131d251f7429c56a2ae2b1b75ce104fe9e83315a0c71ccf2b20267683ac
Address pollution:
https://etherscan.io/tx/0x87c6e5d56fea35315ba283de8b6422ad390b6b9d8d399d9b93a9051a3e11bf73
Misdirected transactions:
https://etherscan.io/tx/0x3374abc5a9c766ba709651399b6e6162de97ca986abc23f423a9d893c8f5f570
-
More covert phishing, using CREATE 2 to bypass security detection
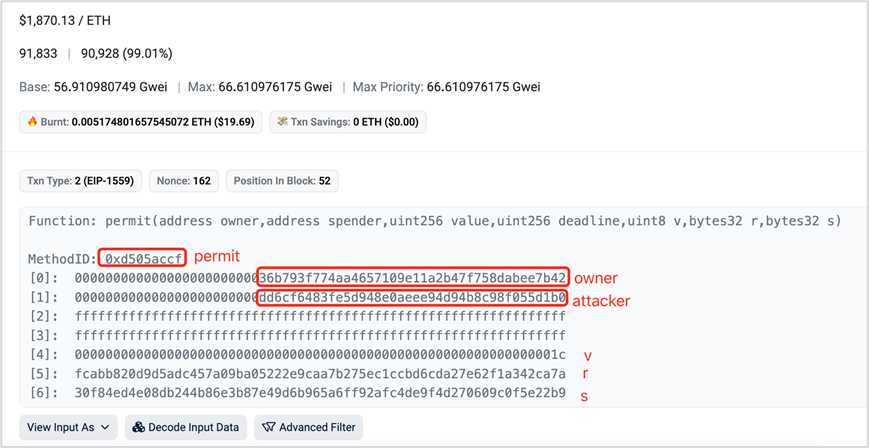
At present, various wallets and security plug-ins have gradually realized visual risk reminders for phishing blacklists and common phishing methods, and the signature information is displayed more and more completely, which improves the ability of ordinary users to identify phishing attacks. However, attack and defense technologies are always confronting each other and constantly evolving, and more covert phishing methods are constantly emerging, so we need to be vigilant. Using CREATE 2 to bypass the blacklist detection of wallets and security plug-ins is a common method recently.
Create 2 is an opcode introduced in the Ethereum Constantinople upgrade that allows users to create smart contracts on Ethereum. The original Create opcode generates a new address based on the creators address and nonce, Create 2 allows users to calculate the address before the contract is deployed. Create 2 is a very powerful tool for Ethereum developers, enabling advanced and flexible contract interactions, parameter-based contract address pre-calculation, off-chain transactions, and flexible deployment and adaptation of specific distributed applications.
Create 2 brings benefits as well as new security risks. Create 2 can be abused to generate new addresses with no malicious transaction history, bypassing the wallets blacklist detection and security alerts. When the victim signs a malicious transaction, the attacker can deploy a contract on a pre-calculated address and transfer the victims assets to that address, and this is an irreversible process.
Features of this attack:
Allowing predictive creation of contract addresses, enabling attackers to trick users into granting permissions before the contract is deployed.
Since the contract has not been deployed at the time of authorization, the attack address is a new address, and the detection tool cannot issue an early warning based on the historical blacklist, which makes it more concealed.
Here is an example of phishing using CREATE 2:
https://etherscan.io/tx/0x83f6bfde97f2fe60d2a4a1f55f9c4ea476c9d87fa0fcd0c1c3592ad6a539ed14
In this transaction, the victim transferred the sfrxETH in the address to the malicious address (0x 4 D 9 f 77), which is a new contract address without any transaction records.
However, when opening the creation transaction of this contract, it can be found that the contract completed a phishing attack at the same time as it was created, transferring assets from the victims address.
https://etherscan.io/tx/0x77c79f9c865c64f76dc7f9dff978a0b8081dce72cab7c256ac52a764376f8e52
Looking at the execution of this transaction, we can see that 0x4d9f7773deb9cc44b34066f5e36a5ec98ac92d40 is created after the call to CREATE 2.
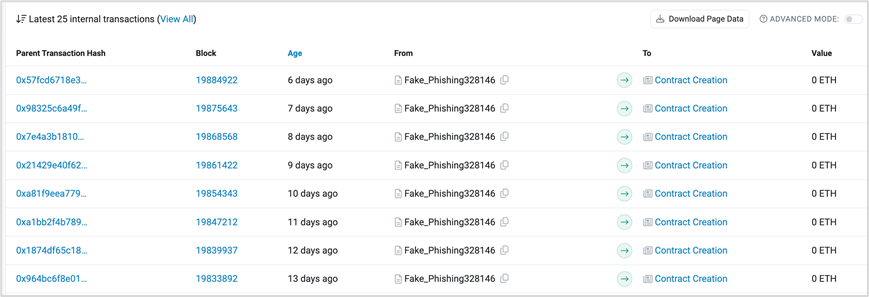
In addition, by analyzing the relevant addresses of PinkDrainer, it can be found that this address creates new contract addresses through CREATE 2 for phishing every day.
https://etherscan.io/address/0x5d775caa7a0a56cd2d56a480b0f92e3900fe9722#internaltx
-
Fishing as a Service
Phishing attacks are becoming increasingly rampant. Due to the huge profits from illegal activities, a black industry chain of Drainer as a Service (DaaS) has gradually developed. The more active ones include:
Inferno/MS/Angel/Monkey/Venom/Pink/Pussy/Medusa, etc. Phishing attackers purchase these DaaS services and quickly and easily build thousands of phishing websites and fraudulent accounts, rushing into this industry like a flood and threatening the security of users assets.
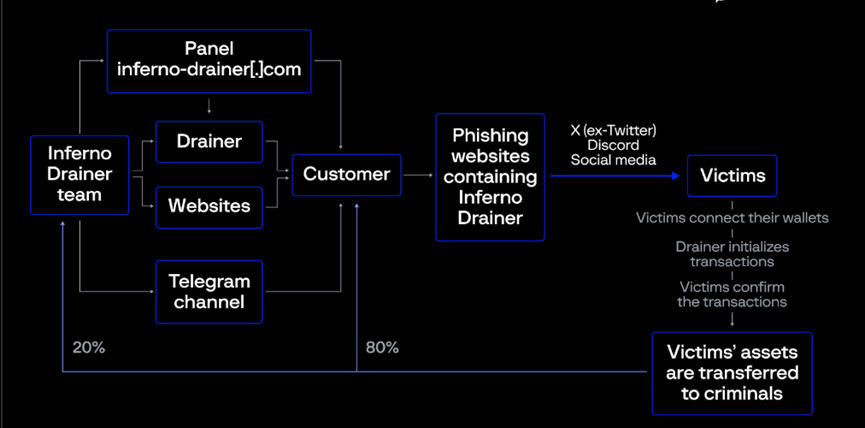
Take Inferno Drainer as an example. This is a notorious phishing gang that implements phishing by embedding malicious scripts on different websites. For example, they spread seaport.js, coinbase.js, and wallet-connect.js, disguised as popular Web3 protocol functions (Seaport, WalletConnect, and Coinbase) to induce users to integrate or click. After the user confirms, the users assets will be automatically transferred to the attackers address. At present, more than 14,000 websites containing malicious Seaport scripts, more than 5,500 websites containing malicious WalletConnect scripts, more than 550 websites containing malicious Coinbase scripts, and more than 16,000 malicious domain names related to Inferno Drainer have been found, and the brand names of more than 100 crypto brands have been affected.
Under the phishing-as-a-service framework, usually 20% of the stolen assets are automatically transferred to the Inferno Drainer organizer address, and the phishing implementer retains the remaining 80%. In addition to this, Inferno Drainer regularly provides free services for creating and hosting phishing websites, and sometimes phishing services also require a fee of 30% of the defrauded funds. These phishing websites are designed for phishing attackers who are able to attract victims to visit but lack the technical ability to create and host websites or simply do not want to perform this task themselves.
So, how does this DaaS scam work? Here’s a step-by-step description of Inferno Drainer’s crypto scam scheme:
1) Inferno Drainer promoted their service through a Telegram channel called Inferno Multichain Drainer, and sometimes the attackers also accessed the service through the Inferno Drainer website.
2) The attacker uses the DaaS service function to set up and generate his own phishing website and spread it through X (Twitter), Discord and other social media.
3) Victims are lured into scanning QR codes or other methods contained on these phishing websites to connect their wallets.
4) The Drainer checks the victim’s most valuable and easily transferable assets and initiates a malicious transaction.
5) The victim confirms the transaction.
6) Assets were transferred to criminals. Of the stolen assets, 20% was transferred to the Inferno Drainer developers and 80% was transferred to the phishing attackers.
-
Safety Tips
(1) First of all, users must not click on unknown links disguised as positive news such as rewards or airdrops;
(2) There are more and more cases of official social media accounts being hacked. Official messages may also be phishing messages, and official messages are not necessarily absolutely safe.
(3) When using wallets, DApps and other applications, be sure to be careful to identify and beware of fake sites and fake apps;
(4) Any transaction or message that requires confirmation needs to be handled with caution, and cross-confirmation should be done based on the target, content, and other information. Refuse blind signatures, stay vigilant, and doubt everything to ensure that every step is clear and safe.
(5) In addition, users need to understand the common phishing attack methods mentioned in this article and learn to actively identify phishing features. Understand common signatures, authorization functions and their risks, and understand the contents of fields such as Interactive (interactive URL), Owner (authorizer address), Spender (authorized party address), Value (authorized quantity), Nonce (random number), Deadline (expiration time), and transfer/transferFrom (transfer).
IV. Analysis of FIT 21
On May 23, 2024, the U.S. House of Representatives officially passed the FIT 21 Crypto Act (Financial Innovation and Technology for the 21st Century Act) with 279 votes in favor and 136 votes against. U.S. President Biden announced that he would not veto the bill and called on Congress to cooperate on a comprehensive and balanced regulatory framework for digital assets.
FIT 21 aims to provide a way for blockchain projects to be launched safely and efficiently in the United States, clarify the boundaries of responsibilities between the U.S. Securities and Exchange Commission (SEC) and the Commodity Futures Trading Commission (CFTC), distinguish whether digital assets are securities or commodities, and strengthen supervision of cryptocurrency exchanges to better protect American consumers.
4.1 What are the important contents of FIT 21?
-
Definition of Digital Assets
Original text of the bill: IN GENERAL.—The term digital asset means any fungible digital representation of value that can be exclusively possessed and transferred, person to person, without necessary reliance on an intermediary, and is recorded on a cryptographically secured public distributed ledger.
The bill defines digital assets as an exchangeable digital representation that can be transferred from person to person without relying on an intermediary and recorded on a cryptographically protected public distributed ledger. This definition includes a wide range of digital forms, from cryptocurrencies to tokenized physical assets.
-
Classification of digital assets
The bill proposes several key elements to distinguish whether digital assets are securities or commodities:
(1) Investment Contract (The Howey Test)
If the purchase of a digital asset is considered an investment and the investor expects to make a profit through the efforts of the entrepreneur or a third party, the asset is generally considered a security based on the standard established by the U.S. Supreme Court in SEC v. WJ Howey Co., commonly known as the Howey test.
(2) Use and consumption
If a digital asset is primarily used as a medium for consumption of goods or services rather than as an investment in the expectation of capital appreciation, such as tokens that can be used to purchase specific services or products, although in the actual market these assets may also be purchased and held speculatively, from the perspective of design and primary use, it may not be classified as a security, but rather as a commodity or other non-security asset.
(3) Degree of decentralization
The bill specifically emphasizes the degree of decentralization of the blockchain network. If the network behind a digital asset is highly decentralized, with no centralized authority controlling the network or assets, the asset may be more likely to be considered a commodity. This is important because there are key differences between the definitions of commodities and securities, which have an impact on how they are regulated.
The U.S. Commodity Futures Trading Commission (CFTC) will regulate digital assets as a commodity “if the blockchain or digital ledger on which it runs is functional and decentralized.”
The U.S. Securities and Exchange Commission (SEC) will regulate a digital asset as a security “if its associated blockchain is functional but not strictly decentralized.”
The bill defines decentralization as, among other requirements, “no person has unilateral control over the blockchain or its use, and no issuer or associated person controls 20% or more of the ownership or voting power of the digital asset.”
The specific criteria for defining the degree of decentralization are as follows:
Control and Influence: In the past 12 months, no individual or entity has had the unilateral power, directly or by contract, arrangement or otherwise, to control or materially change the functionality or operation of the blockchain system.
Ownership Distribution: No individual or entity associated with a digital asset issuer owns more than 20% of the total digital asset issued in the past 12 months.
Voting Power and Governance: No individual or entity associated with the digital asset issuer has been able to unilaterally direct or influence more than 20% of the voting power in the digital asset or related decentralized governance system in the past 12 months.
Code Contributions and Modifications: In the past three months, the digital asset issuer or related personnel have not made substantial, unilateral modifications to the source code of the blockchain system, unless these modifications are to address security vulnerabilities, maintain routines, prevent network security risks or other technical improvements.
Marketing and Promotion: In the past 3 months, the digital asset issuer and its affiliates have not marketed the digital asset to the public as an investment.
Among these definition criteria, the more rigid ones are the distribution of ownership and governance rights. The 20% boundary line is of great significance for the definition of digital assets as securities or commodities. At the same time, because of the openness, transparency, traceability and immutability of blockchain, the quantification of this definition standard will become clearer and fairer.
(4) Functions and technical characteristics
The connection between digital assets and the underlying blockchain technology is also one of the important factors in determining the direction of regulation. This connection usually includes how digital assets are created, issued, traded and managed:
Asset issuance: Many digital assets are issued through the programmatic mechanism of blockchain, which means that their creation and distribution are based on preset algorithms and rules rather than human intervention.
Transaction verification: Transactions of digital assets need to be verified and recorded through the consensus mechanism in the blockchain network to ensure the correctness and immutability of each transaction.
Decentralized governance: Some digital asset projects have implemented decentralized governance, where users holding specific tokens can participate in the project’s decision-making process, such as voting on the project’s future development direction.
These characteristics directly affect how assets are regulated. If digital assets primarily provide economic returns through automated processes on the blockchain or allow voting to participate in governance, they may be considered securities because it indicates that investors are expecting to gain benefits through management or corporate efforts. If digital assets function primarily as a medium of exchange or are used directly to obtain goods or services, they may be more likely to be classified as commodities.
-
Promotion and sales of digital assets
How digital assets are promoted and sold in the market is also an important part of FIT 21. If a digital asset is marketed primarily through the expected return on investment, it may be considered a security. The content here is extremely important because it regulates the regulatory framework for digital assets and will affect what the next digital asset that may be available through a spot ETF will be.
(1) Registration and supervision responsibilities
There are two definitions of digital assets: digital commodities and securities. The bill stipulates that the supervision of digital assets will be jointly responsible by two main agencies, depending on the definition:
Commodity Futures Trading Commission (CFTC): Responsible for regulating digital commodity trading and related market participants.
Securities and Exchange Commission (SEC): Responsible for regulating digital assets that are deemed to be securities and the platforms on which they are traded.
(2) Lock-up period for token insiders
Original text of the bill: A restricted digital asset owned by a related person or an affiliated person may only be offered or sold after 12 months after the later of— (A) the date on which such restricted digital asset was acquired; or (B) the digital asset maturity date. .
The provision requires that insiders’ token holdings be locked up for at least 12 months from the date of acquisition, or 12 months from the defined “digital asset maturity date,” whichever is later.
This ability to delay sales helps prevent insiders from taking advantage of undisclosed information or unfairly influencing market prices. By aligning the interests of insiders with the long-term goals of the project, it helps avoid speculation and market manipulation, helping to create a more stable and fair market environment.
(3) Restrictions on sales of digital assets by related parties
Original text of the Act: Digital assets may be sold by an affiliated person under the following conditions: (1) The total volume of digital assets sold by the person does not exceed 1% of the outstanding volume in any three-month period; (2) the affiliated person must immediately report to the Commodity Futures Trading Commission or the Securities and Exchange Commission any order to sell more than 1% of the outstanding volume.
Digital assets may be sold by related persons in the following circumstances:
-
The total amount of digital assets sold in any 3-month period shall not exceed 1% of the stock;
-
A related person must immediately report to the Commodity Futures Trading Commission or the Securities and Exchange Commission any orders to sell more than 1% of the inventory.
This measure ensures market stability and health by limiting the amount of sales by related persons in a short period of time, preventing market manipulation and excessive speculation.
(4) Project information disclosure requirements
Original text of the bill: Digital asset issuers must disclose the information described in Section 43 on a public website prior to selling digital assets under Section 4(a)( 8).
The specific information required by the project disclosure is not detailed in the excerpt provided, but will typically include:
The nature of the digital asset: what the digital asset represents (e.g., shares in a company, rights to future earnings, etc.);
Related risks: potential risks involved in investing in this digital asset. ;
Development Status: The current status of the project or platform related to the digital asset, such as development milestones or market readiness;
Financial information: any financial details or forecasts related to the digital asset;
Management team: Information about the people behind the project or company that issues the digital asset.
The bill requires digital asset issuers to provide detailed project information, including the nature, risks, and development status of the assets, so that investors can make informed investment decisions. This move enhances market transparency and protects the interests of investors.
(5) Principle of safe isolation of customer funds
Original text of the bill: Digital commodity exchanges shall hold customer funds, assets, and property in a manner that minimizes the risk of loss or unreasonable delay in access by customers to their funds, assets, and property.
This regulation requires digital asset service providers to take measures to ensure the security of customer funds and prevent customer fund loss or access delays due to operational problems of the service provider.
(6) Customer funds and company operating funds must not be mixed
Original text of the bill: Funds, assets, and property of a customer shall not be commingled with the funds of the digital commodity exchange or be used to secure or guarantee the trades or balances of any other customer or person.
This means that service providers must strictly separate customer funds from company operating funds to ensure the independence of customer funds, avoid using customer funds for unauthorized activities, and enhance the security and transparency of funds.
In certain operations, such as for settlement convenience, it is allowed to deposit customer funds and funds of other institutions in the same account if it complies with regulations. However, it is necessary to ensure the separate management and proper record of these funds to ensure the safety of each customers funds and property.
4.2 Encourage and support innovation
The FIT 21 Act also contains many provisions that encourage and support innovation.
-
Establishment of the CFTC-SEC Joint Advisory Committee
The CFTC-SEC Joint Advisory Committee on Digital Assets was established to:
-
Advise the Commission on its rules, regulations, and policies related to digital assets;
-
Further promote regulatory coordination on digital asset policies among the Commissions;
-
Research and disseminate methods for describing, measuring, and quantifying digital assets;
-
Study the potential of digital assets, blockchain systems and distributed ledger technologies to improve the operational efficiency of financial market infrastructures and better protect financial market participants;
-
Discuss the implementation of this bill and its amendments by the Committee.
The goal of this committee is to promote cooperation and information sharing between the two major regulators on digital asset supervision.
-
Strengthening and expanding the SEC’s Strategic Center for Innovation and FinTech (FinHub)
The bill proposes to strengthen and expand the SEC’s Strategic Center for Innovation and Fintech (FinHub), with the goal of:
-
Help develop the Commission’s approach to technological advances;
-
Examining financial technology innovations by market participants;
-
Coordinate the Commission’s response to emerging technologies in financial, regulatory, and supervisory systems.
Its responsibilities are:
-
Promote responsible technological innovation and fair competition within the Commission, including around financial technology, regulatory technology and supervisory technology;
-
Providing internal education and training on FinTech to the Commission;
-
Advise the Commission on financial technology that serves the Commissions functions;
-
Analyze the impact of technological advances and regulatory requirements on fintech companies;
-
Provide advice to the Commission on rulemaking or other agency or staff actions related to fintech;
-
Providing information about the Commission and its rules and regulations to businesses in the emerging fintech sector;
-
Companies working in emerging technology areas are encouraged to engage with the Commission and obtain its feedback on potential regulatory issues.
FinHubs primary mission is to promote policy development related to fintech and provide guidance and resources to market participants on emerging technologies. It is required to provide Congress with a report on FinHubs activities in the previous fiscal year each year. It is also required to provide documents and information that ensure that FinHub has full access to the Commission and any self-regulatory organization to perform the functions of FinHub. The Commission should establish a detailed record system (as defined in Section 552a of Title 5 of the United States Code) to assist FinHub in communicating with relevant parties.
-
Establishment of the CFTC’s laboratory (LabCFTC)
The bill proposes the creation of LabCFTC, whose objectives are to:
-
Promote responsible financial technology innovation and fair competition for the benefit of the American public;
-
Act as an information platform to inform the Commission of new financial technology innovations;
-
Providing advocacy to financial technology innovators to discuss their innovations and the regulatory framework established by this Act and regulations promulgated thereunder.
Its responsibilities are:
-
Provide advice to the Commission on rulemaking or other agency or staff actions regarding financial technology;
-
Providing internal education and training to the Commission on financial technology;
-
Provide advice to the Commission on financial technology to strengthen the Commission’s oversight function;
-
To engage with academics, students and professionals on financial technology issues, ideas and techniques relevant to the activities of this Act;
-
Providing information to those working in the emerging technology sector regarding the role of the Commission, its rules and regulations, and registered futures associations;
-
Personnel working in the field of emerging technologies are encouraged to engage with and obtain feedback from the Committee on potential regulatory issues.
Similar to FinHub, LabCFTC’s mission is to promote the formulation of relevant policies and provide technical guidance and exchanges. LabCFTC is also required to provide Congress with a report on its activities every year. It should also ensure that LabCFTC has full access to documents and information from the Commission and any self-regulatory organization or registered futures association to perform LabCFTC’s functions and establish a detailed record system.
-
Emphasize and strengthen research on decentralized finance, non-homogeneous digital assets, derivatives, etc.
The Commodity Futures Trading Commission (CFCA) and the Securities and Exchange Commission (SEC) should jointly conduct research on innovative content such as decentralized finance (DeFi), non-fungible digital assets (NFTs), derivatives, etc., study their development trends, and evaluate their impact on traditional financial markets and potential regulatory strategies.
In this part, the attitude towards Crypto compliance is basically established. The clearer direction is the research on DeFi and NFT, which means that DeFi and NFT may also usher in gradually clear regulatory strategies in the future.
4.3 The significance of FIT 21
Although the crypto industry has existed for more than a decade, there is no comprehensive regulatory framework for digital assets globally. The existing regulatory framework is fragmented, incomplete and lacks clarity. This regulatory uncertainty not only hinders the development of innovative businesses, but also provides opportunities for bad actors.
Therefore, the adoption of FIT 21 is of great significance.
Its passage has an important positive effect on establishing a regulatory environment that supports the development of blockchain technology, and at the same time puts forward relatively clear requirements for protecting the crypto market and consumer safety. Specifically, it includes: clearly specifying that different types of digital assets are regulated by the CFTC or SEC; setting consumer protection measures, such as customer fund isolation, lock-up periods for token insiders, limiting annual sales volume and disclosure requirements, etc.
Blockchain technology and digital assets are another epoch-making invention of human civilization after the Internet. They have huge development potential and prospects. We are all trendsetters of the new era by embracing supervision and innovative development.
V. Sonuç
Compared with the first half of 2023, the total losses caused by hacker attacks, project Rugpull, phishing scams, etc. in the first half of 2024 have increased significantly, reaching 1.492 billion US dollars. Overall, the situation in the field of Web3 security is very serious.
However, the overall market situation is improving, the security awareness of project parties and Web3 users is gradually increasing, and relevant compliance policies are also being steadily improved.
Web3 is a new world, full of imagination and opportunities. I believe that in this land, security and compliance will play an increasingly important role in protecting the security of users’ encrypted assets.
This article is sourced from the internet: SharkTeam: Web3 Security Report for the First Half of 2024
Original author: Lao Bai A while ago, a public account I like very much, Orange Book, published an article titled Crypto Impotence. A terrible boredom is spreading in the Crypto world, like the Black Death. No one knows where it started, but before you know it, you find that this disease is everywhere. Come to think of it, there is really nothing worth writing about in the recent circle of technology. The only hot topics are concentrated on memes such as Pepe, Trump, and Jenner. The last technology-oriented hot topic was probably the duality of image and currency Pandora? The primary market is also affected. Fortunately, innovation is always happening. Although we still don’t see anything truly 0 to 1, things from 1 to 10 are still happening in all…