เผยข้อมูลโจรกรรม GCR: แฮกเกอร์คือใคร ทำเงินได้เท่าไหร่?
ผู้เขียนต้นฉบับ: ZachXBT
เรียบเรียงโดย : Odaily Planet Daily Azuma
หมายเหตุของบรรณาธิการ: บทความนี้เป็นการวิเคราะห์ข้อมูลโดย ZachXBT ซึ่งเป็นนักสืบออนเชนชื่อดัง เกี่ยวกับการโจรกรรมบัญชี X ของเทรดเดอร์ในตำนานอย่าง GCR เมื่อสุดสัปดาห์ที่แล้ว
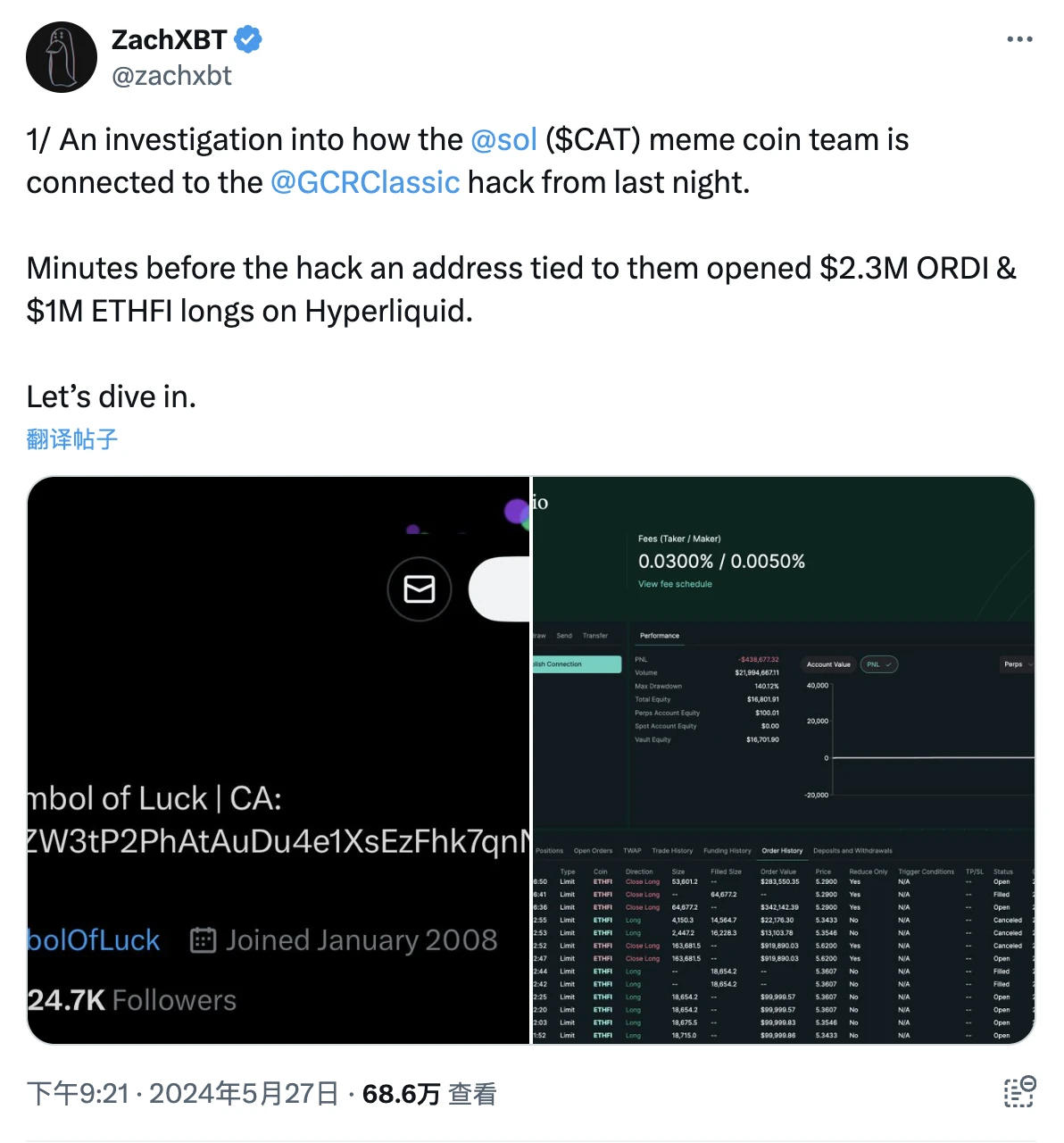
เมื่อสุดสัปดาห์ที่ผ่านมา บัญชี GCRs X (@GCRClassic) ถูกขโมย และได้เผยแพร่เนื้อหาเกี่ยวกับการสั่งการเกี่ยวกับ ORDI และ ETHFI ส่งผลให้ตลาดสกุลเงินที่เกี่ยวข้องผันผวนอย่างรุนแรงในระยะสั้น ZachXBT ค้นพบผ่านการวิเคราะห์แบบออนเชนว่าการขโมยดูเหมือนจะเกี่ยวข้องกับทีมพัฒนา Sol (ไม่เกี่ยวข้องกับทีม Solana) ของโทเค็น CAT บน Solana
ต่อไปนี้เป็นเนื้อหาต้นฉบับของ ZachXBT แปลโดย Odaily Planet Daily
บทความนี้เป็นการวิเคราะห์ความเชื่อมโยงระหว่างทีมพัฒนา CAT Sol และเหตุการณ์โจรกรรม GCR
ไม่กี่นาทีก่อนการแฮ็ก ที่อยู่ที่เชื่อมโยงกับทีม “Sol” ได้เปิดสถานะซื้อ ORDI จำนวน $2.3 ล้านและ ETHFI จำนวน $1 ล้านบน Hyperliquid
มาเริ่มเปิดเผยความลับกันเลยดีกว่า
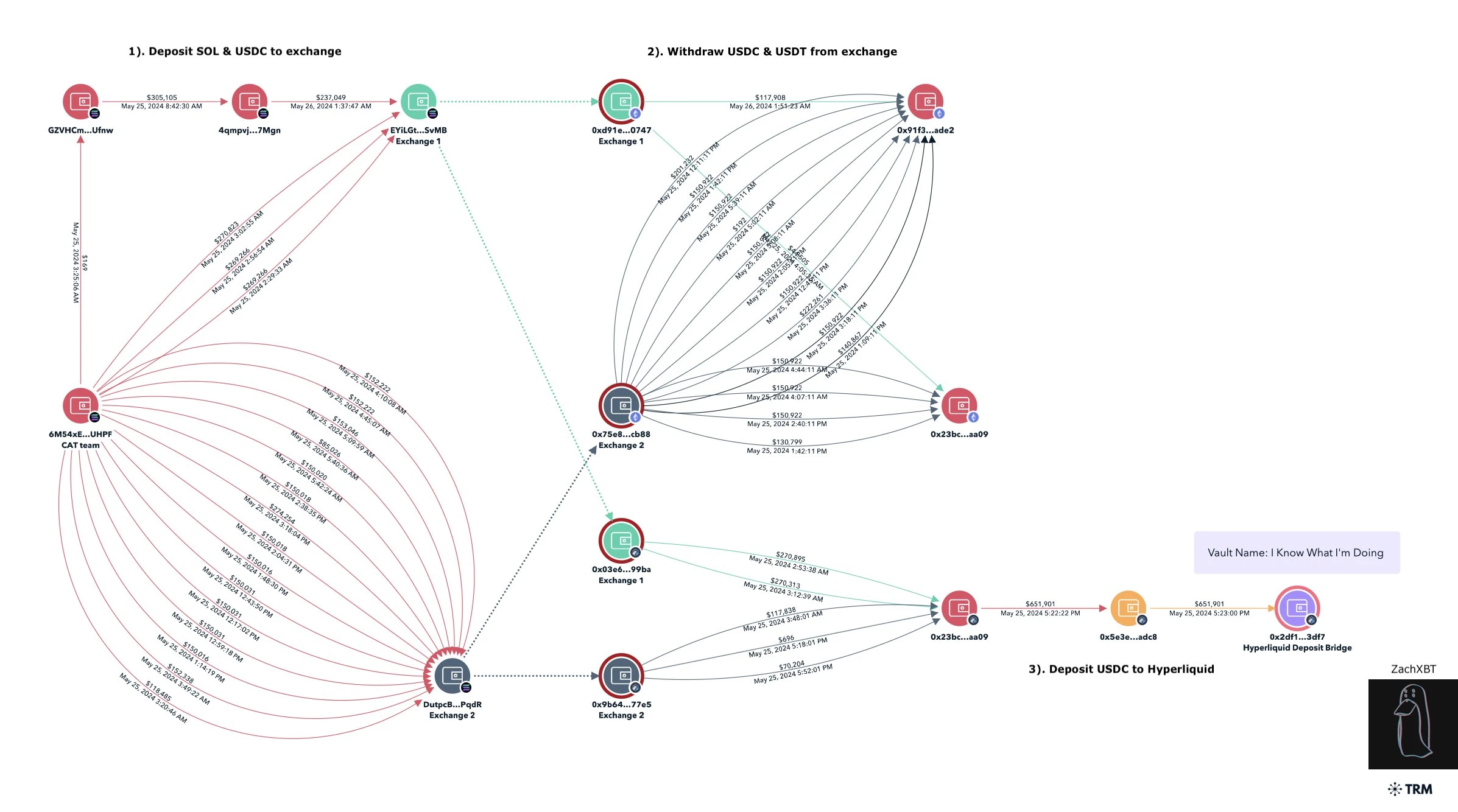
บริการวิเคราะห์แบบออนเชน Lookonchain มี ตรวจสอบ และชี้ให้เห็นว่าทีม Sol ถูกสงสัยว่าแอบขโมยโทเค็น CAT ที่ออกโดยตัวเอง ซึ่งควบคุมอุปทานโทเค็น 63% ปัจจุบันทีม Sol ขายได้ในราคาสูงกว่า 5 ล้านเหรียญสหรัฐ และกำไรก็ถูกกระจายและโอนไปยังที่อยู่หลายแห่ง
ในจำนวนนี้ ที่อยู่ซึ่งขึ้นต้นด้วย 6M54x (6M54xEUamVAQVWPzThWnCtGZ7qznomtbHTqSaMEsUHPF) ได้รับประมาณ 15,000 SOL (มูลค่าประมาณ 2.5 ล้านเหรียญสหรัฐ) และเริ่มฝากเงินไปยัง Kucoin (ประมาณ 4,800 SOL) และ MEXC (ประมาณ 4,800 SOL และ 1.4 ล้านเหรียญสหรัฐ) ในวันที่ 25 พฤษภาคม
จากการวิเคราะห์เวลา ฉันพบว่าไม่นานหลังจากทำธุรกรรมฝากเงินสองรายการบน Solana เสร็จเรียบร้อย ธุรกรรมถอนเงินสองรายการบน Kucoin และ MEXC ก็ปรากฏขึ้นบน Ethereum และ Arbitrum และจำนวนเงินที่ถอนออกมาใกล้เคียงกับจำนวนเงินที่ฝากมาก ที่อยู่ที่เกี่ยวข้องมีดังต่อไปนี้:
-
0x23bcf31a74cbd9d0578bb59b481ab25e978caa09;
-
0x91f336fa52b834339f97bd0bc9ae2f3ad9beade2.
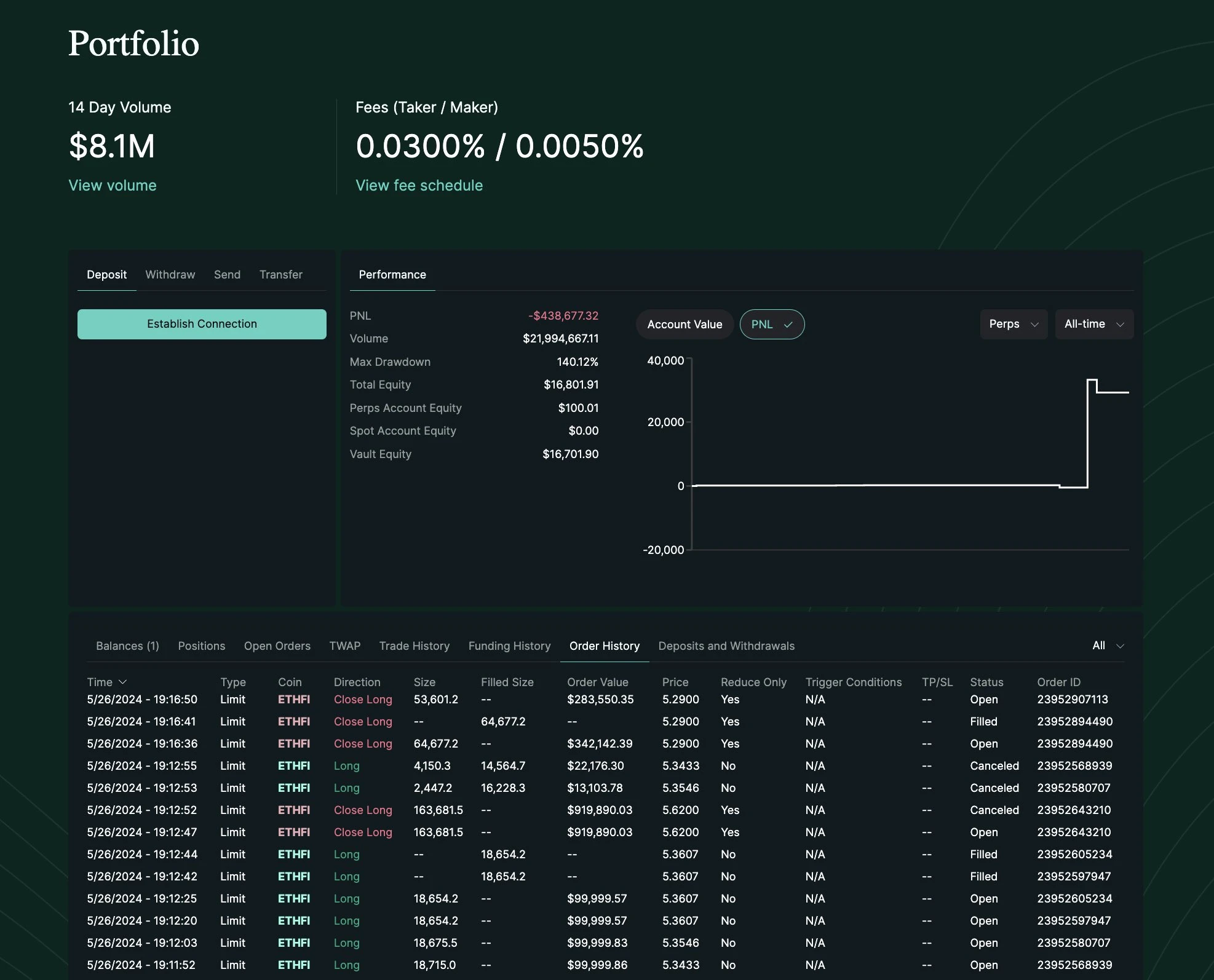
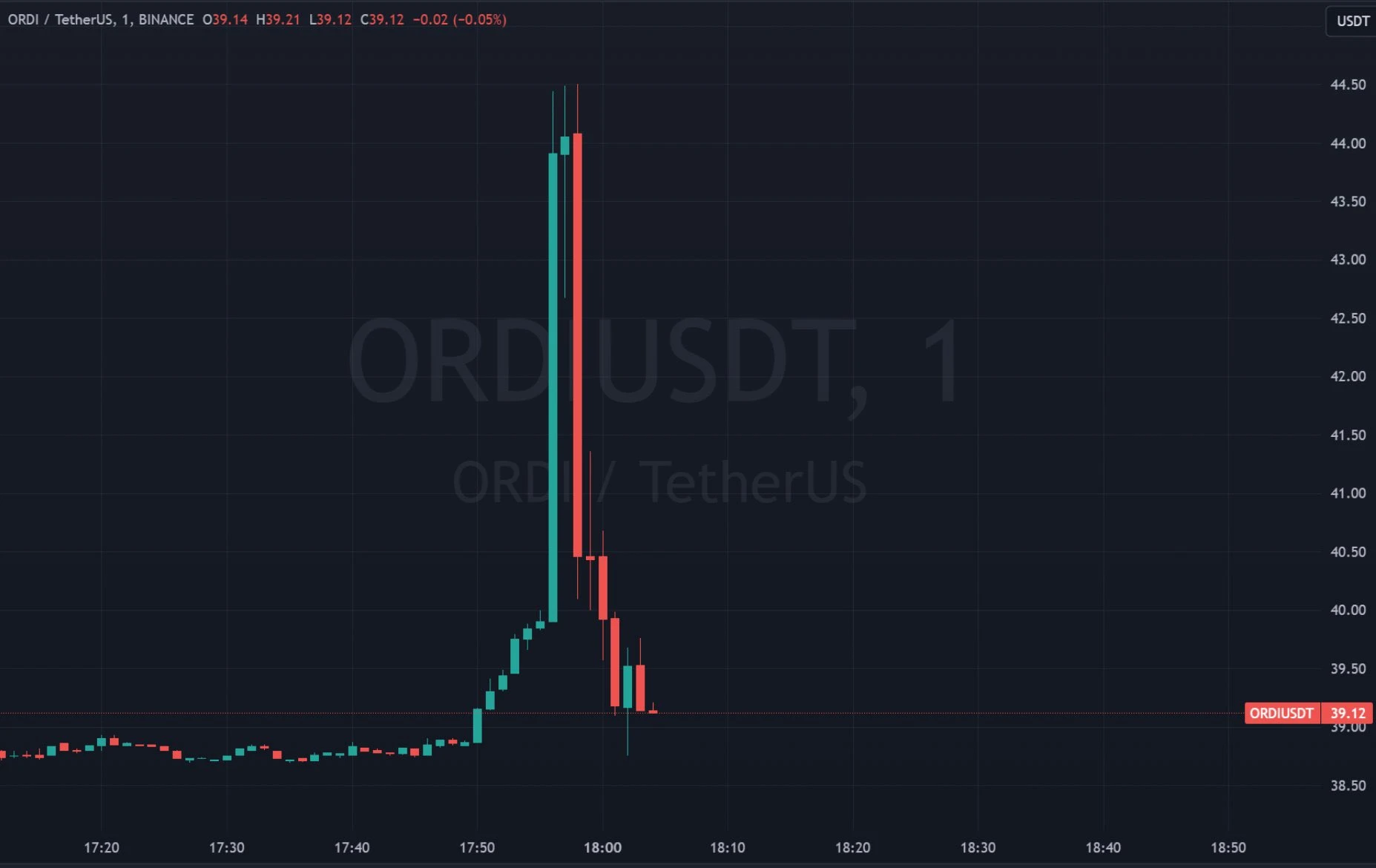
เวลา 17:22 น. ของวันที่ 25 พฤษภาคม (ตามเวลา UTC ทั้งหมด) ที่อยู่ข้างต้นซึ่งเริ่มต้นด้วย 0x 23 bc ได้โอน $650,000 USDC ไปยังที่อยู่ซึ่งเริ่มต้นด้วย 0x 5 e 3 (0x 5 e 3 edeb 4 e 88 aafcd 1 f 9 be 179 aa 6 ba 2c 87 cbbadc 8) และฝากไว้ใน Hyperliquid สำหรับการซื้อขายตามสัญญา ในเวลาต่อมา ระหว่างเวลา 17:45 ถึง 17:56 น. ของวันที่ 26 พฤษภาคม ที่อยู่เริ่มต้นด้วย 0x 5 e 3 ได้เปิดสถานะซื้อของ ORDI มูลค่า $2.3 ล้านบน Hyperliquid
เมื่อเวลา 17:55 น. ของวันที่ 26 พ.ค. ได้โพสต์บัญชี GCRs X โพสต์เกี่ยวกับ ORDI (มีแนวโน้มขาขึ้นและลงทุนใน ORDI อย่างหนัก) ทำให้ราคาของ ORDI พุ่งสูงขึ้นในระยะสั้น ที่อยู่ที่เริ่มต้นด้วย 0x5e3 ปิดตำแหน่งระหว่าง 17:56 น. ถึง 18:00 น. ทำให้มีกำไรประมาณ $34,000
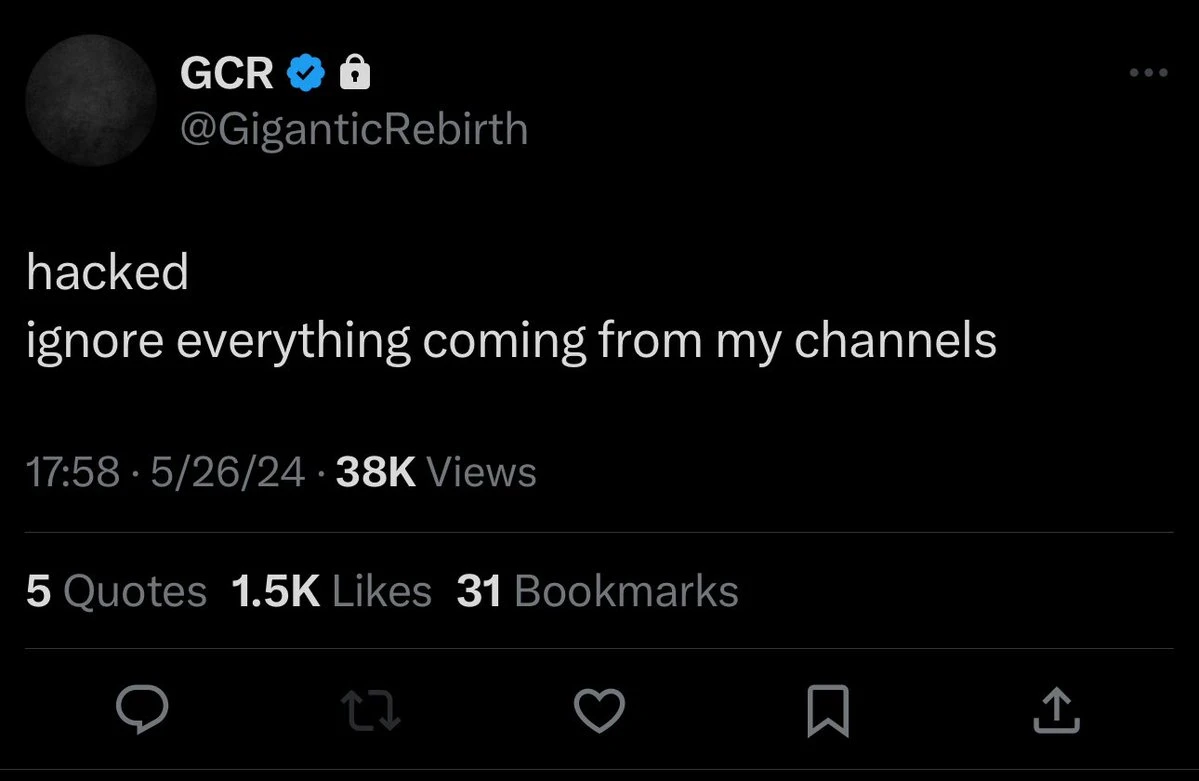
เมื่อเวลา 17:58 น. ของวันที่ 26 พฤษภาคม GCR ได้โพสต์ข้อความบนบัญชี X อีกบัญชีของเขาเพื่อยืนยันว่าบัญชีหลักของเขาถูกขโมยไป
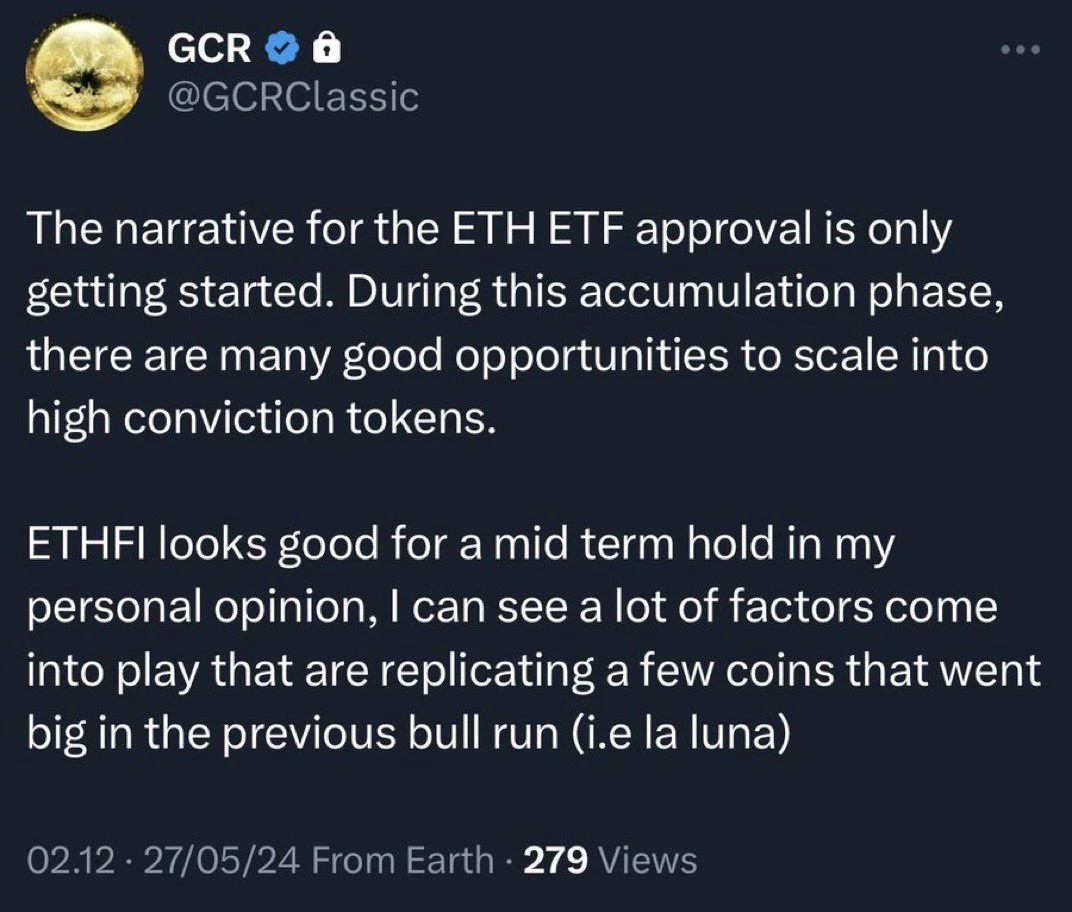
ระหว่างเวลา 19:04 น. ถึง 19:12 น. ของวันที่ 26 พฤษภาคม แฮกเกอร์ได้ใช้กลอุบายเดิมๆ อีกครั้ง โดยที่อยู่ซึ่งเริ่มต้นด้วย 0x5e3 ได้เปิดตำแหน่งซื้อ $1 ล้านใน ETHFI บน Hyperliquid เป็นครั้งแรก จากนั้นในเวลา 19:12 น. แฮกเกอร์ได้ใช้บัญชี GCR ที่ขโมยมาเพื่อโพสต์คำสั่งขายอีกครั้งเกี่ยวกับ ETHFI
อย่างไรก็ตาม ในครั้งนี้ดูเหมือนว่าตลาดจะตื่นตัวแล้ว และ ETHFI ก็ไม่ได้เลียนแบบแนวโน้มของ ORDI ระหว่างเวลา 19:16 น. ถึง 19:45 น. ที่อยู่ที่เริ่มต้นด้วย 0x5e3 ถูกบังคับให้ปิดตำแหน่ง ส่งผลให้สูญเสียไปประมาณ US$3,500
ข้างต้นคือการวิเคราะห์เหตุการณ์การแฮ็กครั้งนี้ของ ZachXBT จากมุมมองของข้อมูล กำไรขั้นสุดท้ายของแฮกเกอร์จาก "ธุรกรรมที่ถูกจัดการ" ทั้งสองรายการอยู่ที่ "เพียง" ประมาณ $30,000 และแม้แต่รายการหนึ่งก็จบลงด้วยการขาดทุน ซึ่งดูเหมือนว่าจะน้อยกว่าที่หลายคนคาดเดา
ที่น่ากล่าวถึงคือเนื่องจาก ZachXBT เคยเตือนตลาดเกี่ยวกับพฤติกรรมที่น่าสงสัยที่ไม่ดีของทีม Sol ก่อนหน้านี้ ชุมชนโทเค็น CAT จึงล้อเลียน ZachXBT เมื่อราคาเหรียญเพิ่มขึ้นในระยะสั้นในช่วงสองวันที่ผ่านมา (ลดลง 75% ในช่วง 24 ชั่วโมงที่ผ่านมา)
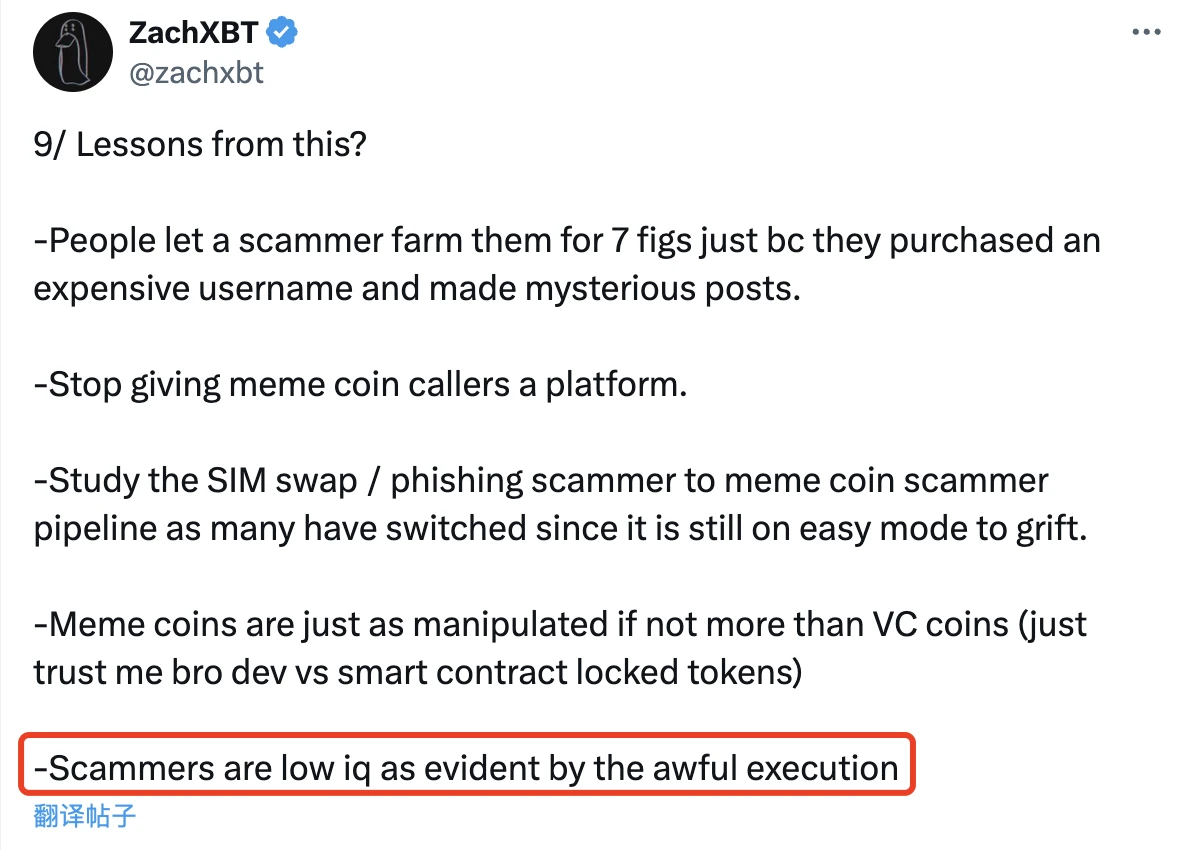
ตอนนี้ที่เขาพบโอกาสนี้แล้ว ZachXBT ก็ไม่ลืมที่จะแสดงความคิดเห็นเชิงประชดประชัน และตอนท้ายบทความ เขาได้ระบุอย่างชัดเจนว่า จากการปฏิบัติการอันแปลกประหลาดของพวกเขา จะเห็นได้ว่าแฮ็กเกอร์มี IQ ต่ำมาก
บทความนี้มีที่มาจากอินเทอร์เน็ต: เปิดเผยการโจรกรรม GCR: แฮกเกอร์คือใคร ทำเงินได้เท่าไหร่?
ที่เกี่ยวข้อง: Mantle (MNT) รีบาวด์? การวิเคราะห์ผลกระทบของการขาย $36 ล้าน
ราคา Brief Mantle ถือเป็นจุดสูงสุดใหม่ตลอดกาลในสัปดาห์นี้ โดยแตะ $1.31 ก่อนที่จะปรับฐานเล็กน้อย วาฬขายได้ประมาณ 30 ล้าน MNT ในช่วงสามวัน ซึ่งเป็นผลลัพธ์ที่คาดหวัง ที่อยู่ที่ใช้งานอยู่ตามความสามารถในการทำกำไรแสดงให้เห็นว่าผู้เข้าร่วมน้อยกว่า 12% มีกำไร ซึ่งบ่งชี้ว่าไม่น่าจะขายต่อได้ ราคา Mantle (MNT) ยังคงสร้างความประทับใจให้กับนักลงทุนด้วยการเพิ่มขึ้นและการเพิ่มขึ้น ซึ่งส่งผลให้อัลท์คอยน์ทำจุดสูงสุดใหม่ตลอดกาล คำถามก็คือว่าผู้ถือ MNT สามารถรักษาการชุมนุมนี้ไว้หรือย้ายไปขายโทเค็นได้หรือไม่ นักลงทุน Mantle ย้ายราคา Mantle อย่างรวดเร็วถึงระดับสูงสุดที่ $1.31 ในสัปดาห์ที่ผ่านมาก่อนที่จะปรับฐานซื้อขายที่ $1.22 ในขณะที่เขียนบทความนี้ อัลท์คอยน์ยังคงรองรับ Exponential Moving Average (EMA) 50 วัน อย่างไรก็ตาม เนื่องจาก...