Комплексный анализ безопасности уровней L0, L1, L2 и L3 блокчейна
This article Hash (SHA 1):73c704b01c20bcc2137e83c1446832be2b4f779f
No.: Lianyuan Security Knowledge No.013
Blockchain technology has become an important infrastructure in many fields such as modern finance, supply chain, and data storage due to its decentralized and transparent characteristics. However, with the development of technology, blockchain systems are also facing increasingly complex security challenges. The ChainSource Security Team will analyze from different levels: L0 (underlying infrastructure), L1 (main chain), L2 (extension solution), and L3 (application layer). We will comprehensively analyze the security of these four main levels of blockchain, and explore the challenges and coping strategies they face, with specific cases attached.
Layer 0: underlying infrastructure security
The L0 layer is the infrastructure of the blockchain, including hardware, network, and consensus mechanism, etc. The security of this layer directly affects the stability and security of the entire blockchain system.
Security Challenges:
-
Hardware security: Hardware devices may be subject to physical attacks or failures, resulting in data leakage or system crashes.
-
Network security: Blockchain networks may suffer DDoS attacks, affecting the normal operation of the network.
-
Consensus mechanism security: Consensus mechanisms (such as PoW, PoS, etc.) may be attacked, leading to double-spending attacks or fork problems.
Safety measures:
-
Hardware Cryptography: Use Hardware Security Modules (HSMs) and Trusted Execution Environments (TEEs) to protect keys and sensitive data.
-
Network protection: Deploy firewalls and DDoS protection mechanisms to ensure network stability.
-
Consensus mechanism optimization: Improve the consensus algorithm and increase the difficulty of attack, such as increasing the computational complexity of Proof of Work (PoW) or adopting a multi-level verification mechanism of Proof of Stake (PoS).
Case: Ethereum Classic is a forked chain of Ethereum, which inherits the original chain of Ethereum. In 2019 and 2020, the ETC network suffered multiple 51% attacks. The attacker controlled more than 50% of the network computing power and carried out multiple reorganization attacks, resulting in double spending, losing millions of dollars in assets, and seriously affecting the credibility and security of the network. After that, the ETC community strengthened network monitoring, introduced tools to detect and defend against 51% attacks, and increased the cost of attacks.
Layer 1: Mainchain security
The L1 layer refers to the main chain part of the blockchain, which involves the blockchains protocol and data structure. The security of this layer is related to the integrity of the blockchain network and the immutability of the data.
Security Challenges:
-
Protocol vulnerabilities: Blockchain protocols may have design flaws or implementation vulnerabilities that can be exploited maliciously.
-
Smart contract vulnerabilities: Smart contract code may contain vulnerabilities, resulting in theft of funds or abuse of the contract.
-
Node security: Nodes may be attacked, affecting the normal operation of the entire blockchain network.
Safety measures:
-
Protocol Audit: Regularly conduct security audits on blockchain protocols to identify and fix potential vulnerabilities.
-
Smart Contract Audit: Use tools and third-party audit services to conduct a comprehensive review of smart contract code to ensure its security.
-
Node protection: Deploy intrusion detection systems (IDS) and firewalls to protect nodes from attacks.
Case: In 2016, Ethereums DAO (decentralized autonomous organization) was attacked. This incident involved the security of the Ethereum network. The attacker used a vulnerability in the DAO smart contract (recursive call vulnerability) to conduct a double spending attack, and the hacker stole about $50 million worth of Ethereum. This incident led to the Ethereum communitys decision to conduct a hard fork to roll back the stolen funds, resulting in Ethereum (ETH) and Ethereum Classic (ETC), and the introduction of stricter contract auditing and security review mechanisms to enhance the security of the network.
Layer 2: Scaling solution security
Blockchain L2 (Layer 2) security mainly involves expansion solutions on top of the blockchain network, which are designed to improve the scalability and performance of the network while maintaining high security. L2 solutions include side chains, state channels, lightning networks, etc. The security of this layer involves cross-chain communication and transaction confirmation. Security challenges:
-
Cross-chain communication security: Cross-chain communication protocols may have vulnerabilities and be maliciously exploited for attacks.
-
Transaction confirmation security: The L2 transaction confirmation mechanism may have defects, resulting in double payment or unconfirmed transactions.
-
Extension solution implementation security: The implementation of the extension solution may have design flaws or implementation vulnerabilities, affecting the security of the system.
-
Safety measures:
-
Cross-chain protocol audit: Conduct a comprehensive audit of the cross-chain communication protocol to ensure its security.
-
Transaction confirmation mechanism optimization: Improve the transaction confirmation mechanism to ensure the uniqueness and immutability of transactions.
-
Security verification of extension scheme: Use formal verification and security testing tools to fully verify the extension scheme to ensure its security.
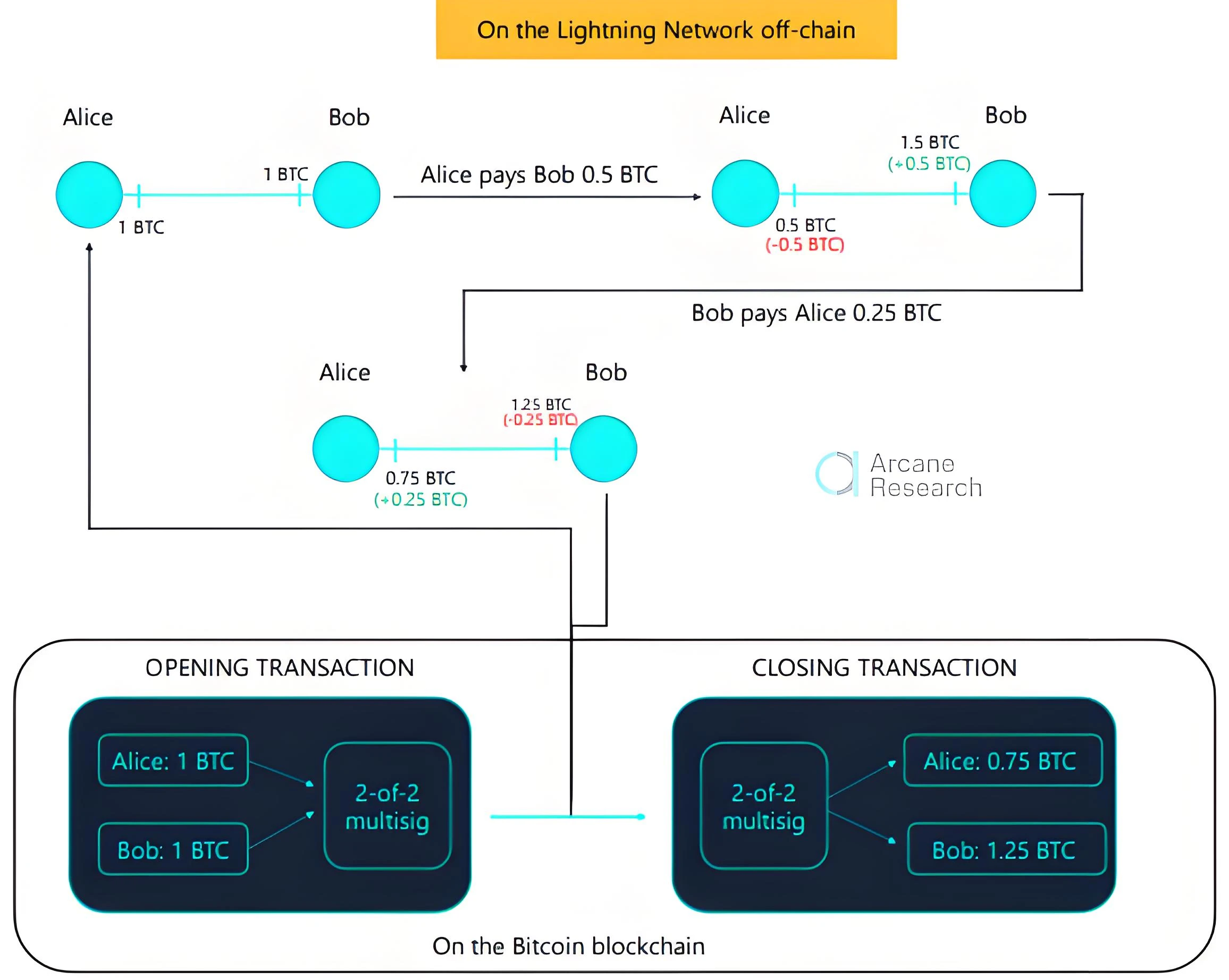
Case: Lightning Network is an L2 expansion scheme for fast small payments in Bitcoin. In 2019, researchers discovered a vulnerability that allowed attackers to steal users funds through malicious transactions. Attackers can send invalid transactions before the channel is closed, resulting in the theft of user funds. Although the vulnerability has not been exploited on a large scale, it exposes the potential risks of Lightning Network in terms of security. The development team quickly released a patch, recommended users to upgrade to the latest version, and strengthened security audits.
Layer 3: Application layer security
The L3 layer refers to blockchain-based applications, including the security of smart contracts, the security of dApps, and on-chain governance mechanisms, such as decentralized applications (DApps) and smart contract platforms. The security of this layer involves the security of user data and application logic.
Security Challenges:
-
User data security: User data may be leaked or tampered with, resulting in privacy leakage or data loss.
-
Application logic vulnerabilities: Application logic may have vulnerabilities that can be exploited by malicious actors to launch attacks.
-
Authentication security: User authentication mechanisms may have flaws and be exploited by malicious actors to carry out attacks.
-
Safety measures:
-
Data encryption: Encrypt user data for storage to protect user privacy.
-
Application logic audit: Use security audit tools and third-party audit services to conduct a comprehensive review of application logic to ensure its security.
-
Multi-factor authentication: Use multi-factor authentication mechanism to improve the security of user identity authentication.
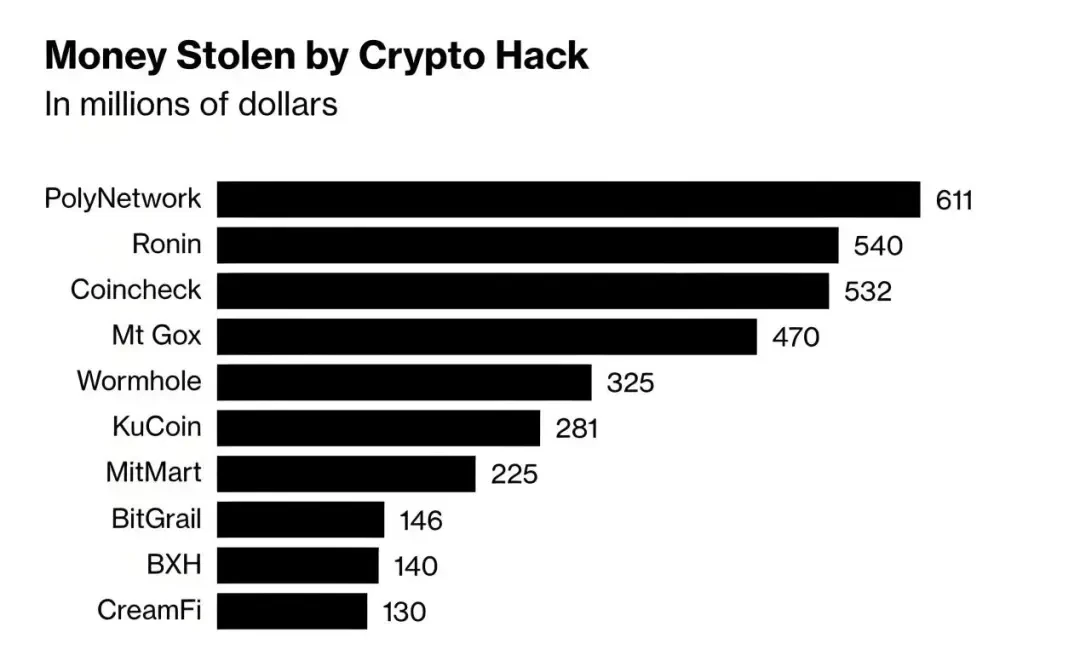
Case: In August 2021, the cross-chain interoperability protocol Poly Network was suddenly hacked. O 3 Swap, which uses the protocol, suffered serious losses. The assets on the three major networks of Ethereum, Binance Smart Chain, and Polygon were almost looted. Within 1 hour, 250 million, 270 million, and 85 million US dollars of crypto assets were stolen, respectively, with a total loss of up to 610 million US dollars. This attack was mainly caused by the replacement of the public key of the relay chain validator. That is, the attacker replaced the intermediate validator of the cross-chain and controlled it by the attacker himself. This incident prompted more decentralized exchanges to strengthen the security audit of smart contracts and the implementation of multi-factor authentication.
Заключение
The security of blockchain is a multi-layered issue that requires comprehensive analysis and response at all levels from L0 to L3. The overall security of the blockchain system can be greatly improved by strengthening hardware and network security, improving consensus mechanisms, regularly auditing protocols and smart contracts, optimizing cross-chain communication and transaction confirmation mechanisms, and ensuring the security of user data and application logic at the application layer.
Our ChainSource security team will continue to conduct security research and technical improvements to ensure the healthy development of blockchain technology so that users can conduct transactions more safely. We firmly believe that only by continuously improving security at all levels can we truly realize the vision of blockchain decentralization, transparency and security.
Lianyuan Technology — компания, ориентированная на безопасность блокчейна. Наша основная работа включает исследование безопасности блокчейна, анализ данных в цепочке и восстановление уязвимостей активов и контрактов. Мы успешно восстановили множество украденных цифровых активов для частных лиц и учреждений. В то же время мы стремимся предоставлять отчеты по анализу безопасности проектов, отслеживаемость в цепочке и услуги технического консалтинга/поддержки для отраслевых организаций.
Спасибо за чтение. Мы продолжим уделять внимание и делиться контентом по безопасности блокчейна.
This article is sourced from the internet: Comprehensive analysis of the security of blockchain L0, L1, L2 and L3 layers
Related: The US SEC finally let Paxos go. Has BUSD become a victim of the policy struggle?
Original|Odaily Planet Daily Author: jk On July 11, local time in the United States, after a year-long investigation, the U.S. Securities and Exchange Commission (SEC) decided to end its investigation into Paxos Trust Company and the Binance USD (BUSD) stablecoin. Paxos received a formal termination notice from the SEC stating that it would not recommend enforcement action against the company. This news marks a major victory for Paxos in the legal dispute related to the Binance USD (BUSD) stablecoin. Background: SEC’s Wells Notice caused BUSD, with a market value of $20 billion, to gradually fade away What is Paxos? Paxos is a blockchain infrastructure and tokenization platform that works with major global companies to tokenize, custody and trade assets. Partners include PayPal, Interactive Brokers, Mastercard, Free Market and Nubank, and…