オリジナル锝淥daily Planet Daily
著者: jk
On October 24, local time in the United States, a wallet associated with the US government was hacked, resulting in the theft of funds worth about $20 million. These funds came from assets seized in the Bitfinex hack in 2016, involving multiple encrypted addresses and complex fund flows. Just 20 hours later, the money was transferred back to an address controlled by the US government. What is the whole process of this incident?
For readers who are not familiar with the early history of the 暗号currency world, the Bitfinex hack was a major event in the cryptocurrency world that year.
On August 2, 2016, the Bitfinex exchange was hacked, resulting in the theft of approximately 119,756 Bitcoins from its hot wallets. After the incident, the price of Bitcoin fell by almost 20% , and investors panicked over fears of another Mt. Gox-like collapse. Many traders and investors withdrew their funds from Bitfinex, and the exchange had to suspend trading and deposits for nearly a week. After the incident, Bitfinex issued an IOU token called BFX to affected users as compensation for the stolen Bitcoins. These tokens were later redeemed in full by Bitfinex at a 1:1 ratio.
In 2022, Ilya Lichtenstein and Heather Morgan pleaded guilty to money laundering conspiracy related to the hack, and the government has seized approximately 95, 000 stolen ビットコインs worth approximately $3.6 billion from wallets they controlled, and subsequently seized approximately $475 million in funds related to the incident.
Today, there have been unusual movements in wallets controlled by the US government that were related to the hacking incident that year.
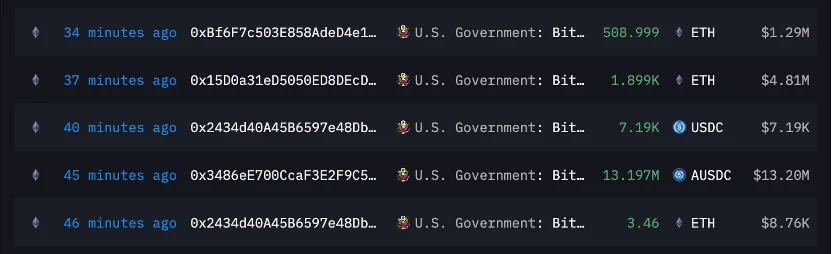
US government wallet transactions monitored by Arkham. Source: Arkham
According to monitoring, the US government address (the address where the Bitfinex hacker seized funds) withdrew $6.57 million worth of stablecoins from Aave early this morning. Subsequently, the hacker transferred $20.71 million of funds to an address starting with 0x 348, including USDC, USDT and aUSDC. Subsequently, a total of about $6.8 million in stablecoins were converted into Ethereum and distributed to multiple addresses, including Binances deposit address and two new addresses. Arkham analysis believes that this is the behavior of hackers who have begun money laundering.
19 hours later, the stolen funds began to be gradually returned by the hackers. The hackers returned a total of more than $19.3 million in five transactions from different addresses, accounting for 88% of the total stolen funds. However, according to the on-chain detective ZachXBT, this amount does not include a small amount of funds that have been transferred to exchanges such as Switchain, HitBTC and N 交換.
Fund returns monitored by Arkham. Source: Arkham
The community has different opinions on the fact that the funds went around in a circle within 20 hours: some people think that this is the result of the FBIs work , which locked the hacker in a short period of time and forced him to return the funds. Others focus on the hackers behavior of transferring funds to Binance, believing that this behavior is likely to make the relationship between Binance and the US government, which had previously eased, become delicate again. Secondly, Binance has a KYC mechanism to identify the true identity of the hacker, and this may be one of the reasons for the final return. Some people even say that this incident may be theft or internal behavior, because this is also the real reason for most hacking incidents in the past.
We will continue to pay attention to the subsequent developments of the incident.
This article is sourced from the internet: The US government wallet was hacked, but the coins came back after a round trip?
Related: Viewpoint: Encryption applications should focus less on technology and more on demand
Original author: rm Original translation: TechFlow Consumer product apps are really hard to make! We, the notorious early adopters, are probably the only ones who get excited about faster transactions than the real world. But let’s be honest, speed doesn’t matter that much if there’s a great waiting interface so users aren’t bored. What really matters is that — to paraphrase Nikita Bier — most consumer apps fall into three categories: enrichment, social, and entertainment, and their intersections. People want to use these apps to make or save money, to entertain themselves, or to meet people (whether colleagues, friends, or future family). These are the basic needs that consumer apps target, not the technology itself. For years, we’ve been asking, “ What can this technology do? ” But for most…