要約
-
In order to solve the data island and security issues faced by ecological projects when deploying multiple chains, the modular BTC Layer 2 B² Network launched the B² information sharing protocol.
-
The B² information sharing protocol uses zero-knowledge proof and verifier mechanism, which not only ensures the privacy, security and decentralization of cross-chain message transmission, but also improves the scalability of the system.
-
The B² information sharing protocol implementation scenarios include: improving the security of cross-chain transmission, achieving seamless information transmission between chains, synchronizing governance decisions, and supporting message sharing and direct transaction calls.
-
The B² information sharing protocol is a universal messaging protocol that will be extended to multiple chains and multiple ecosystems.
The need for information sharing
With the rapid development of blockchain technology, the number of blockchain networks is also increasing. Bitcoin, as the earliest blockchain, is mainly used to process peer-to-peer decentralized payment systems. With the emergence of Ethereum, smart contracts and decentralized applications (dApps) have become important application areas of blockchain technology. Later, with the rise of many public chains such as Polkadot, Cosmos, Avalanche, Solana, TON, etc., various blockchain networks have sprung up, bringing different consensus algorithms, governance models, transaction mechanisms and application scenarios.
However, this diversity also brings a huge challenge: the isolation between blockchains. Traditionally, different blockchains are independent and isolated from each other. They each run on independent networks and have no native communication mechanism, which leads to interoperability issues in the blockchain ecosystem. In this context, the need to share messages between blockchains has gradually become prominent, becoming one of the key factors in promoting the maturity and coordinated development of the blockchain ecosystem.
In the existing blockchain architecture, it is difficult for blockchains to interact directly with each other. The Bitcoin and Ethereum networks are two completely independent ecosystems, and users cannot directly transfer value or information from one network to another. For example, users cannot directly transfer Bitcoin from the Bitcoin network to the Ethereum chain and use it for smart contract transactions. Similarly, developers cannot use data or events on different blockchains to build cross-chain applications. This limitation restricts the widespread application of blockchain technology and the development of the ecosystem.
Message sharing can solve this problem. Through message sharing between blockchains, data, value, and events on different chains can be transmitted and utilized to break the blockchain island phenomenon. The implementation of message sharing can not only enhance the collaboration between different chains, but also pave the way for the widespread application of blockchain technology.
B² Message Sharing Protocol
B² Network is the most practical modular BTC Layer 2 solution. It pioneered the verification of the second-layer rollup on the Bitcoin mainnet through proof of commitment, and extended this solution to other Layer 2s, thus creating the first implemented Bitcoin DA layer. Currently, the total transaction volume of the B² Network mainnet exceeds 70 million, with more than 7.61 million independent addresses.
B² Message Sharing Protocol is a cross-chain message sharing protocol of B² Network based on zero-knowledge proof technology and validator mechanism, which aims to achieve secure and efficient message transmission and data sharing between different blockchain networks (including EVM-compatible chains and non-EVM-compatible chains). At the same time, it provides a trigger mechanism to provide transaction calls between any chains while achieving message data sharing. With the development of blockchain technology, the number of blockchain networks continues to increase, and their underlying technologies and consensus mechanisms often have large differences, making communication and data exchange between blockchains very difficult. Through innovative design, the B² Message Sharing Protocol breaks through the limitations of traditional cross-chain technology and provides a new solution for inter-chain interoperability of ecological dApps.
Goals of the B² Message Sharing Protocol
The core goal of the B² message sharing protocol is to solve the island effect between blockchains, that is, different chains cannot directly share information or data. To this end, B² uses the following technical means:
-
Zero-knowledge proof technology: ensures the privacy of messages during transmission, while providing reliable verifiability to ensure the authenticity and integrity of messages.
-
Validator mechanism: A decentralized validator network is responsible for the verification and transmission of inter-chain messages, ensuring security and decentralization while improving the scalability of the system.
The B² message sharing protocol is designed to be compatible with multiple blockchains, including not only EVM-compatible chains such as Ethereum, BNB Chain, various EVM-compatible Layer 2, etc., but also non-EVM-compatible chains such as Polkadot, Cosmos, Solana, and TON, etc. This makes the B² message sharing protocol a universal solution for cross-chain communication, enabling message intercommunication between diverse blockchain ecosystems.
Application of Zero-Knowledge Proof in B² Message Sharing Protocol
Zero-Knowledge Proofs (ZKP) is one of the key technologies in the B² message sharing protocol. Zero-Knowledge Proofs allow the prover to prove the authenticity and reliability of a message to the verifier without revealing the specific content of the message. This provides crucial privacy protection and security for cross-chain communication.
In the B² message sharing protocol, the cross-chain message transmission process is verified by zero-knowledge proof. For example, when a transaction or status update message is generated on a chain, the message will be packaged and a corresponding zero-knowledge proof will be generated to prove that the message does comply with the state rules on the chain. Then, the proof and the message are sent to the target chain together, and the target chain can verify the zero-knowledge proof to ensure the authenticity and legitimacy of the message and ensure the decentralization of the process.
Advantages of zero-knowledge proof:
-
Privacy: The verifier can verify the authenticity of the message without knowing the specific content of the message, thus avoiding the leakage of sensitive information.
-
Computational efficiency: Zero-knowledge proof can improve the efficiency of inter-chain communication by simplifying complex on-chain verification logic while ensuring security.
-
Security: Zero-knowledge proof can effectively prevent forged messages and replay attacks, ensuring the authenticity of cross-chain messages.
The B² message sharing protocol uses zero-knowledge proof to ensure that the verification of cross-chain messages is highly protected in terms of privacy and security, building a strong trust foundation for data sharing between different blockchains, ensuring the authenticity and validity of messages, and ensuring the trustlessness and decentralization of the entire process.
Validator Mechanism
Another core mechanism of the B² message sharing protocol is the validator network. Validators are a network of decentralized nodes that are responsible for receiving, verifying, and transmitting messages between chains through a P2P network. The validator mechanism ensures the validity of cross-chain messages while preventing single points of failure or centralized attacks.
The workflow of the validator network is as follows:
-
Receiving messages: When a blockchain needs to share information with another blockchain, the message is first sent to the validator network. The message is intercepted by the proposer and a zero-knowledge proof is generated to ensure the legitimacy and integrity of the message.
-
Verify the message: The verifier transmits the message and proof through the P2P network, verifies the zero-knowledge proof and message content, confirms whether the message complies with the status rules of the initiating chain, and performs signature confirmation.
-
Collecting signatures: The validator sends the verified message signature to the proposer through the P2P network, and the proposer collects the validators signatures.
-
Forwarding message: After the proposer collects enough validator signatures, it submits the zero-knowledge proof, message content and validator signature to the message contract of the target chain.
Advantages of the validator mechanism:
-
Decentralization: The validator network is decentralized and jointly participated by different nodes, avoiding the single point of failure problem in cross-chain communication.
-
Efficiency: The validator mechanism optimizes the performance of cross-chain message sharing by reducing the amount of computation performed directly on the chain, which is particularly efficient when complex messages need to be verified.
-
Security and fault tolerance: Even if some validator nodes are attacked or fail to work properly, the validator network can still ensure the delivery and verification of messages through other nodes, enhancing the systems fault tolerance.
Data standards and adaptation layers
An important feature of the B² message sharing protocol is the abstraction of a unified data standard, which enables message sharing between EVM-compatible chains, between EVM-compatible chains and non-EVM-compatible chains, and between non-EVM-compatible chains through smart contract adapters.
In the blockchain field, different chains have huge differences in smart contract architecture, consensus mechanism and virtual machine design. For example:
-
EVM-compatible chains use the Ethereum virtual machine architecture and support smart contracts in the Solidity language, such as Ethereum, Binance Smart Chain, and Avalanche.
-
Non-EVM-compatible chains use different virtual machine architectures and smart contract languages, such as Polkadots Substrate framework, Cosmos Tendermint consensus, and Solanas high-performance architecture.
This difference brings technical challenges to cross-chain message sharing. To address these challenges, the B² message sharing protocol introduces an adaptation layer that specifically handles data format conversion and smart contract call logic between different chains. The adaptation layer includes the following functions:
-
Data format conversion: The data formats (such as transaction structure and status data) on different chains are different. The B² message sharing protocol abstracts a unified data standard and uses the adaptation layer to automatically convert the formats of messages on different chains.
-
Smart contract adaptation: The B² message sharing protocol adapts to different virtual machine architectures of smart contracts, allowing EVM-compatible chains and non-EVM-compatible chains to interact smoothly across chains.
Through the adaptation layer, the B² message sharing protocol can ensure that cross-chain message sharing is carried out efficiently and securely between different types of blockchain networks, truly realizing a cross-chain communication solution that is compatible with multiple chains.
Application scenarios of B² message sharing protocol
The B² message sharing protocol provides strong technical support for the widespread application of blockchain technology, especially in the following scenarios:
-
Asset cross-chain: There are currently many cross-chain bridges that use the notary mechanism. The B² message sharing protocol can share the cross-chain transaction information of the source chain to the target chain. The cross-chain bridge that adopts the notary mechanism can use the B² message sharing protocol to provide the security of the cross-chain bridge and solve the centralized trust problem of the notary mechanism.
-
Decentralized Finance (DeFi): In the cross-chain DeFi ecosystem, different DeFi protocols and users can seamlessly transmit price difference information or share market data between different chains through the B² message sharing protocol.
-
Cross-chain governance: The B² message sharing protocol supports the implementation of cross-chain governance mechanisms, enabling governance decisions on multiple blockchains to work together and improve the governance efficiency of cross-chain projects.
-
Cross-chain transactions: The B² message sharing protocol implements triggers in the target chain, supporting message sharing between different blockchain networks while directly triggering transaction calls on the target chain.
Technical Implementation of B² Message Sharing Protocol
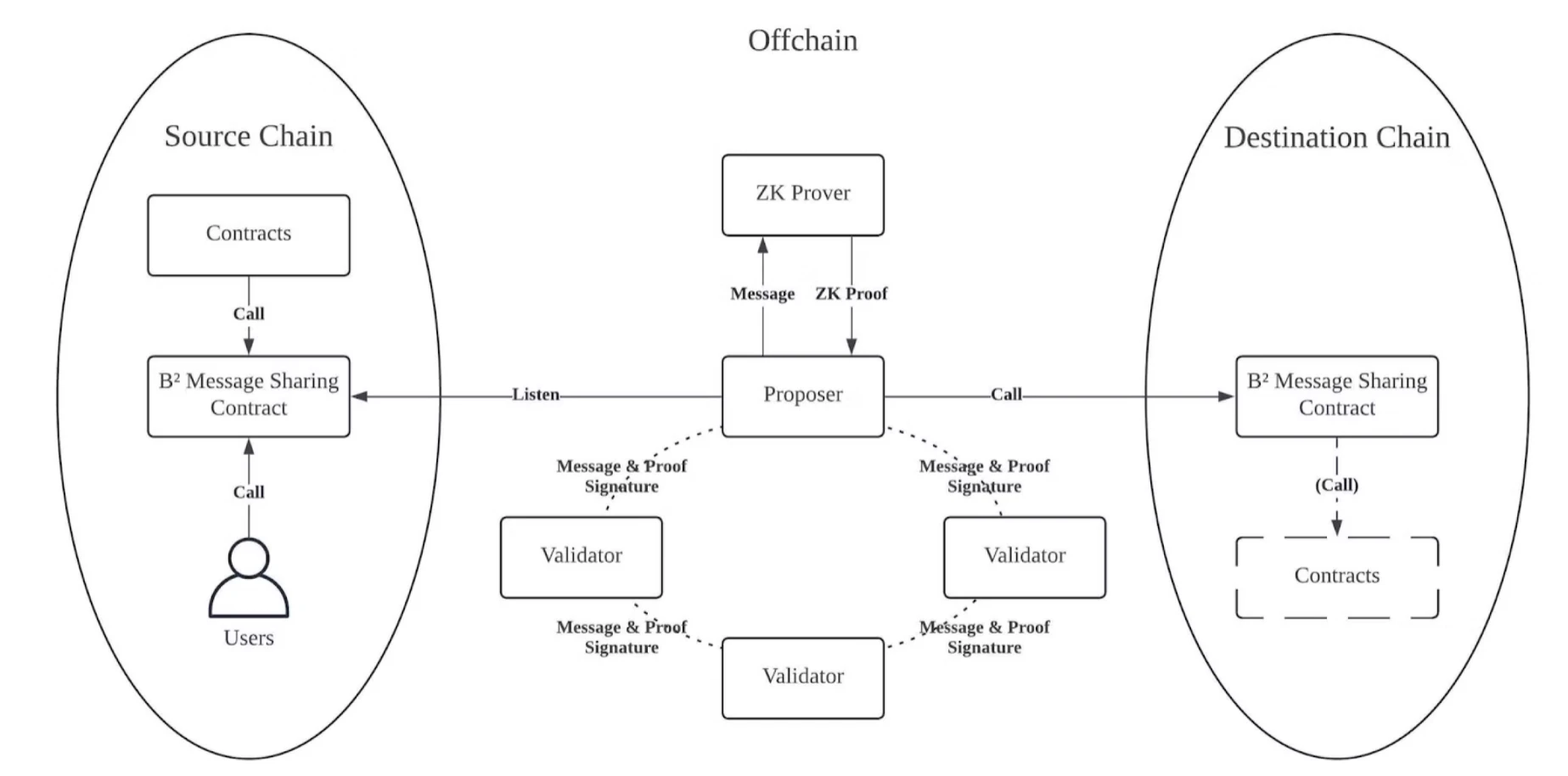
On the source chain, users or contracts can call the B² message sharing contract and send the message to be shared to the B² message sharing contract. At the same time, users or developers can implement a trigger contract on the target chain according to the contract calling standard of the B² message sharing protocol.
In the decentralized validator network off-chain, there is a Proposer role, which is responsible for monitoring the events of the B² message sharing contract on the source chain. When the Proposer monitors the message event of the source chain, it first sends the message to the ZK Prover to generate a zero-knowledge proof, then signs the message and the content summary of the zero-knowledge proof, and finally the Proposer broadcasts the message, zero-knowledge proof and signature in the decentralized validator p2p network.
There are multiple validators in the decentralized validator network. After receiving the message, zero-knowledge proof and signature of the proposer, the validator verifies the message, zero-knowledge proof and signature. After the verification is passed, the validator signs the content summary of the message and zero-knowledge proof and broadcasts it to the p2p network.
The proposer collects signatures from validators in the p2p network. When enough signatures are collected (the mn principle, there are n validators in the network. When m signatures are collected, it is considered that the protocol requirements are met. m and n are the parameters for starting the protocol), the proposer will assemble the call transaction of the B² message sharing contract of the target chain and send it to the target chain.
On the target chain, users or developers obtain the message content on the source chain through the B² message sharing contract. At the same time, users or developers can also set the trigger contract call of the target chain in the transaction of the source chain. When the target link receives the shared message, the contract will automatically call the trigger contract to trigger different business processes.
When using a trigger contract, the user or developer needs to specify the maximum gas consumption in the transaction on the source chain and pay the gas fee.
The B² message sharing protocol successfully breaks down the information barriers between different blockchain networks by combining zero-knowledge proof technology and a decentralized validator mechanism, providing a secure, efficient, and multi-chain compatible message sharing solution. Whether it is an EVM-compatible chain or a non-EVM-compatible chain, the B² message sharing protocol can effectively support interoperability between different blockchain ecosystems, providing strong support for the innovation and expansion of decentralized applications.
This article is sourced from the internet: B² launches message sharing protocol to break down “data silos”
関連:分散型AIデータプロトコルVanaの分析:CoinbaseとParadigmが支援する総額$25百万米ドルの資金調達
原文|Odaily Planet Daily(@OdailyChina)著者|Nan Zhi(@Assassin_Malvo)本日、分散型AIデータプロトコルVanaがCoinbase主導で$5百万の資金調達を発表した後、そのTelegramゲームData HeroがXプラットフォームで広く宣伝され、コミュニティはそれをParadigmが投資した唯一のAIプロジェクトとして宣伝しました。 Vanasの実際のコアビジネスは何ですか?エアドロップを受け取るために対話できますか?この記事ではOdailyが説明します。 プロジェクトの背景 プロジェクトビジネスの解釈 Vanaは、ユーザー所有のプライベートデータ用に設計された分散型ネットワークです。これは、ユーザーがData DAOと呼ばれる組織を通じて提供するデータとAIモデルを所有、管理、および利益を得るEVM互換のレイヤー1ブロックチェーンで構成されています。 Vanaのコアコンポーネントは…