オリジナル|Odaily Planet Daily
著者: jk
On June 19, local time in the United States, cryptocurrency exchange Kraken and blockchain security company CertiK had a public confrontation on social media over a series of serious security vulnerabilities.
The incident originated from a vulnerability discovered by CertiK on Kraken: Nick Percoco, Krakens chief security officer, disclosed on Twitter that he had received an extremely serious vulnerability report in its bug bounty program, which claimed to have found a vulnerability that could artificially increase the account balance. CertiK called it a security test of the Kraken exchange, while Kraken believed that CertiK took advantage of the vulnerability to make a profit. The two sides held their own opinions and could not agree on a solution, resulting in a large-scale melon-eating scene.
Kraken’s Disclosure
Here is the process of events released by Kraken’s Chief Security Officer on the X platform:
“On June 9, 2024, we received an alert from a security researcher through our bug bounty program. Initially there were no specifics, but they claimed to have found an “extremely severe” vulnerability that would allow them to artificially inflate their balance on our platform.
Every day we receive fake vulnerability reports from people claiming to be security researchers. This is nothing new for anyone running a bug bounty program. However, we took this very seriously and quickly assembled a cross-functional team to investigate this issue. Here are our findings.
Within minutes, we discovered an isolated vulnerability that, under certain circumstances, could allow a malicious actor to initiate a deposit and receive funds in their account without fully completing the deposit.
To be clear, customers’ assets were never at risk. However, a malicious actor could effectively generate assets in their Kraken accounts over a period of time.
We rated this vulnerability as critical and within an hour (47 minutes to be exact) our team of experts mitigated the issue. Within a few hours, the issue was fully fixed and will not recur.
Our team discovered that this vulnerability stems from a recent user experience (UX) change that instantly credits customer accounts before their assets are settled — allowing customers to trade cryptocurrency markets in real time. This UX change was not adequately tested for this specific attack vector.
After patching the vulnerability, we conducted a thorough investigation and quickly discovered three accounts that had exploited the vulnerability over a period of several days. Upon further investigation, we noticed that one of the accounts was linked to an individual claiming to be a security researcher through KYC.
The individual found this vulnerability in our funding system and used it to increase his account balance by $4. This was enough evidence to submit a bug bounty report to our team and receive a sizable reward under the terms of our program.
However, the security researcher disclosed the vulnerability to two other people he was working with, who used it to fraudulently generate larger amounts of funds. They ultimately withdrew nearly $3 million from their Kraken accounts. These funds came from Krakens vaults, not other customers assets.
The initial bug bounty report did not fully disclose these transactions, so we reached out to the security researchers to confirm some details so that we could reward them for successfully discovering security vulnerabilities on our platform.
We then asked them to provide a detailed description of their activity, create a proof-of-concept of on-chain activity, and arrange for the return of the funds they had withdrawn. This is common practice for any bug bounty program. The security researchers refused.
Instead, they demanded to speak to their BD team (i.e. their sales reps) and would not agree to return any funds until we provided a hypothetical possible loss amount. This is not white hat hacking, this is extortion!
We have had a bug bounty program at Kraken for nearly a decade. The program is run in-house and is led full-time by some of the brightest minds in the community. Our program, like many others, has clear rules:
-
Do not extract more than is necessary to demonstrate the vulnerability.
-
Demonstrate your work (i.e. provide a proof of concept).
-
Anything withdrawn must be returned immediately.
We have never had any problems working with legitimate researchers and we are always responsive.
In the interest of transparency, we disclosed this vulnerability to the industry today. We are being accused of being unreasonable and unprofessional for asking white hat hackers to return what they stole from us. This is unbelievable.
As a security researcher, your hacker license is enabled by following the simple rules of the bug bounty program you participate in. Ignoring these rules and blackmailing the company will revoke your hacker license. This makes you and your company criminals.
We will not reveal the name of the research company because their actions do not deserve recognition. We are treating this as a criminal matter and coordinating with law enforcement. We appreciate the reporting of this issue, but that is all.
Our bug bounty program continues to play an important role in Kraken’s mission and is a key part of our efforts to enhance the overall security of the crypto ecosystem. We look forward to working with good faith actors in the future and will treat this as a standalone incident.”
CertiK Response
Although Kraken did not release the specific name of the company the security researcher belongs to, a few hours later, CertiK released a response to the incident on the X platform. The following is the response released by the official X platform of CertiK:
“CertiK recently discovered a series of serious vulnerabilities in the Kraken exchange that could have resulted in hundreds of millions of dollars in losses.
Starting with the discovery of an issue with Kraken’s deposit system that may not be able to distinguish between different internal transfer statuses, we conducted a thorough investigation, focusing on the following three issues:
1. Can a malicious actor forge a deposit transaction to a Kraken account?
2. Can malicious actors withdraw counterfeit funds?
3. What risk controls and asset protections may be triggered by large withdrawal requests?
Based on our testing results: Kraken exchange failed all of these tests, indicating that Krakens defense-in-depth systems were compromised in multiple ways. Millions of dollars could be deposited into any Kraken account. Over $1 million in counterfeit cryptocurrency could be withdrawn from accounts and converted into valid cryptocurrency. Worse still, no alarms were triggered during the multi-day testing period. Kraken responded and locked the test account only after we formally reported the incident.
Upon discovery, we notified Kraken, whose security team classified it as “critical,” Kraken’s most severe security incident classification level.
After initially successfully identifying and fixing the vulnerability, Kraken’s security operations team threatened individual CertiK employees to repay unmatched amounts of cryptocurrency within an unreasonable amount of time, without even providing a repayment address.
In the spirit of transparency and our commitment to the Web3 community, we are making this information public to protect the security of all our users. We urge Kraken to cease any threats to white hat hackers.
Together we face the risks and protect the future of Web3.”
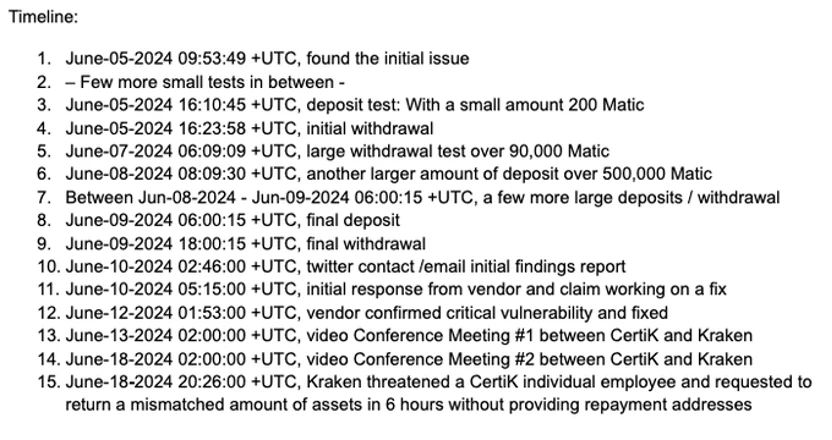
Afterwards, CertiK disclosed the entire timeline and deposit addresses.
Timeline released by CertiK. Source: CertiK official X
At the same time, CertiK also stated that since Kraken did not provide a repayment address and the requested repayment amount did not match at all, we transferred the existing funds to an account accessible to Kraken based on the records.
Other news and follow-up comments
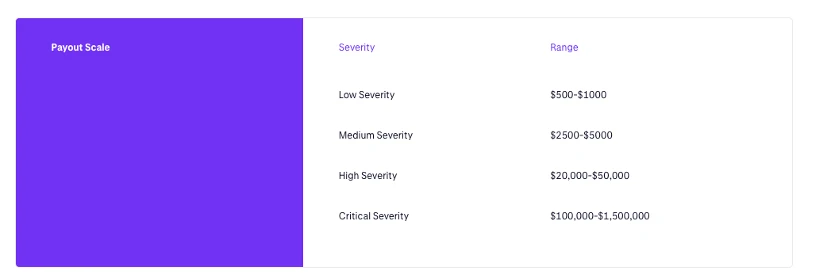
From the background information, the reward amount of Krakens bug bounty program is indeed considerable. The highest security incident level bounty is between 1 million and 1.5 million US dollars. This is quite different from the 3 million US dollars claimed by Kraken. Therefore, some people said in the comment area, I think the hacker should not pay it back, while others replied, Would you rather take the 1 million bounty or go to jail with the 3 million illegal gains?
Kraken bug bounty program rewards. Source: Kraken
Chain Detective ZachXBT said: Story only gets more wild as it goes on.
Another Twitter user, @trading_axe, took a different approach, saying, “I think (CertiK) screwed up… not saying they stole, but a thief would take whatever they can and run. I think they screwed up by only taking $3 million; if they had used this bug to steal over $100 million, then giving it back would have made them look like a white hat (implying that it would make them look like a savior/having the initiative). But you only took $3 million and are now forced to give it back, which makes you look weak.”
This article is sourced from the internet: CertiK vs. Kraken: What is the appropriate standard for white hat hackers?
関連: エッジで生まれる: 分散型コンピューティング パワー ネットワークは、暗号通貨と AI をどのように強化するのか?
原著者:ジェーン・ドウ、チェン・リー 原文ソース:Youbi Capital 1 AIと暗号通貨の交差点 5月23日、チップ大手のNvidiaは2025年度第1四半期の財務報告を発表しました。 財務報告によると、第1四半期のNvidiaの収益は1兆1,000億2,600万米ドルでした。 そのうち、データセンターの収益は昨年より4,271兆9,000億米ドル増加し、驚異的な1兆1,000億2,260万米ドルに達しました。 単独で米国株式市場を救うことができるNvidiaの財務実績の背景には、AIトラックで競争するために世界中のテクノロジー企業の間で爆発的に増加したコンピューティングパワーの需要があります。 トップテクノロジー企業がAIトラックのレイアウトに野心的であるほど、コンピューティングパワーの需要は飛躍的に増加しています。 TrendForcesの予測によると、2024年には、需要は…