Looking Ahead to 2025: 20 Predictions from Scaling to Privacy
Penulis asli: Equilibrium Research
Original translation: Yuliya, PANews
Predicting the future is a challenging, if not impossible, task. Yet everyone is involved in some form of forecasting and making decisions based on their understanding of the future.
Equilibrium has released its first annual forecast report, looking ahead to what is likely to happen and where the industry is headed by the end of next year. The report was produced jointly by Equilibriums lab and venture capital arm.
Before we get into the details, here is the methodology used to develop these forecasts:
-
These predictions focus on being relevant (technical oriented), specific, and falsifiable. Therefore, there will be no price predictions or sweeping statements (e.g. ZK will become faster and cheaper) in the report.
-
The scope of the forecasts is strictly limited to professional capabilities. These forecasts reflect Equilibriums mission to design, build and invest in the core infrastructure of the decentralized network. As such, the report does not include forecasts for applications, stablecoins, decentralized finance, governance, etc., although these areas are equally worthy of attention.
Scaling
1. The number of Ethereum scaling solutions (L2/L3) will exceed 2,000
Currently, L2 Beat lists 120 L2 and L3 projects (collectively referred to as Ethereum Scaling Solutions). Ethereums modularization process will continue to accelerate in 2025, and the number of scaling solutions will exceed 2,000 by the end of the year, an increase of about 17 times from the current scale.
The newly added L2/L3 projects mainly come from two directions: application-specific scaling solutions (games, decentralized finance, payments, social networking, etc.) and enterprise-level L2 solutions (traditional companies expanding into the blockchain field, such as Coinbase or Kraken).
2. Ethereum’s expansion multiple will exceed 200 times
The scaling multiple refers to the ratio of the Ethereum scaling solution to the daily average UOPS or TPS of the Ethereum L1 layer (data from L2 Beat and rollup.wtf). The current value fluctuates around 25 times, and it will take at least 8 times to reach more than 200 times (this growth will be achieved by optimizing existing solutions and launching new solutions).
The L2 scaling multiple reflects both user demand for Ethereum L2/L3 applications and the scaling capabilities of the underlying infrastructure. From a broader perspective, it shows the success of Ethereums rollup-centric scaling roadmap relative to Ethereums L1 layer block space requirements.
Comparison of daily average UOPS of Ethereum expansion solution and Ethereum L1 (data source: L2 Beat)
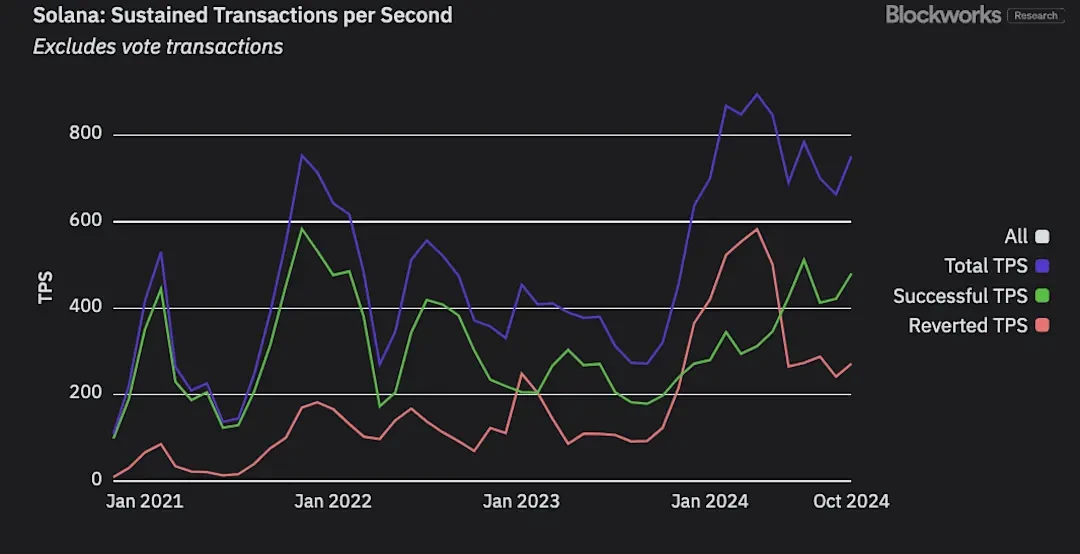
3. Solana transaction processing capacity will exceed 5,000 TPS (non-voting transactions)
Over the past year, Solanas block space demand has remained high due to the development of the decentralized financial ecosystem, meme coin hype, DePIN, and demand growth in multiple areas. This not only enables sufficient stress testing, but also drives the core team to continuously improve network performance. Although more and more teams are beginning to work on Solana network expansion, improving Solana L1 performance is undoubtedly still the top priority of the core development team.
Data source: Solana Roadmap
In recent months, Solana’s non-voting transaction processing capacity has averaged 700-800 transactions per second, with a peak of 3,500 transactions. It is expected that by 2025, this number will increase to an average of more than 5,000 non-voting transactions per second, a 6-7x increase from the current level. The peak level may be much higher than this.
Solanas average transaction processing capacity in recent months has remained at 700-800 transactions per second (data source: Blockworks Research)
Key network upgrades to achieve this goal are expected to include:
-
Full Firedancer client on mainnet: This is the most anticipated major upgrade. While there may be incremental steps in terms of stake distribution, the overall performance gains look pretty significant (not to mention the robustness of having two clients in production).
-
Improving the core Anza client: Another core client developed by Anza can learn from some of Firedancers experience and design choices to improve its own design.
-
Other performance optimizations: including a more fine-grained fee market, more efficient scheduling, and program compression schemes to improve on-chain resource usage efficiency. Another observation is that Solanas blocks are close to the capacity limit (average computing units are 40m and the upper limit is 48m), so increasing the block size is also an option.
4. More than 80% of L2/L3 data will be published to the alternative DA layer
L2 and L3 can choose to publish data to Ethereum (in the form of blobs or calldata), to alternative DA layers such as Avail, Celestia, EigenDA, and NearDA, or to external data availability committees (in the extreme case, the data is stored in only one node).
Currently, about 35% of L2/L3 data is published to alternative DA layers (excluding Avail, NearDA and EigenDA in the figure below), and the rest is published to Ethereum (mainly in the form of blobs). Related indicators and data dashboards can be viewed on Celestia, Ethereum and GrowThePie.
Alternative DA layers are expected to grow to over 80% by 2025. Depending on the increase in target and max blobs in the Pectra update, this will represent a 10-30x increase in data posted to alternative DA layers from today’s levels. This growth will be driven by both high-throughput rollups like Eclipse and MegaETH, which are expected to power Celestia and EigenDA, as well as the native rollup ecosystem that develops on top of Celestia and Avail.
Data source: GrowThePie
5. ZK-based scaling solutions will exceed Optimistic solutions (by number of deployments)
Currently, only about 25% (30 out of 120) of the scaling solutions listed by L2 Beat are validity rollups or validium (leveraging ZKP to prove the correctness of state transitions and publish data to Ethereum or an alternative DA layer/external data availability committee).
As ZK proofs and verifications become faster and cheaper, the long-term advantage of optimistic scaling solutions is diminishing. Validity rollups like Starknet are already setting records in scaling (and this is just the beginning). At the same time, ZK-based scaling solutions provide stronger guarantees on asynchronous interoperability than optimistic solutions. Finally, with faster and cheaper proofs and verifications, latency (or finality time) is naturally reduced without weakening the underlying trust guarantees.
As a result, we expect ZK-based scaling solutions to grow to over 50% by the end of 2025 (and likely significantly more than that). Multiple ZK stacks are expected to launch their production-ready chain development toolkits (Polygon, ZK Sync, Scroll, etc.), which will make it easier to deploy new validity rollups or validiums. In addition, there is growing interest in converting existing optimistic rollups to validity rollups (e.g., by leveraging OP Succinct or Kakarot zkEVM for proofs).
6. Ethereums maximum Gas limit will double to 60m Gas per block
While Ethereum is focused on a rollup-centric expansion roadmap, the L1 layer still plays an important role for many high-value applications that are less sensitive to gas fees. Over the past year, many parties inside and outside the Ethereum Foundation have called for raising the gas limit.
The current maximum gas limit per block is 30m Gas (target 15m), a value that has not changed since 2021. Since then, blocks have been kept at the target level (50% of the maximum limit). It is expected that this limit will double in 2025, with the new maximum limit reaching 60m Gas and the block target being 30m Gas. However, this requires the following conditions to be met:
-
Fusaka Update to be implemented in 2025
-
Ethereum core developer community agrees to increase gas limit as part of Fusaka
ZK Proofs
7. Every Ethereum block will be proven by the end of 2025
ZK-proofing Ethereum blocks could make it easier to verify correct execution. For example, this would benefit light clients that currently rely only on consensus/validator signatures.
Proving each Ethereum block is feasible today by running EVM execution through a general-purpose zkVM at an annual cost of around $1 million (probably less at the time of this posting given the rate of technological progress).
While proofs are delayed by several minutes (currently the average proof for an Ethereum block takes this long), this is still beneficial for services that are not too time-sensitive. As costs and proof times decrease, relying on ZK proofs will become feasible for a wider range of use cases. This leads to the next prediction:
8. Universal zkVM will be able to prove Ethereum mainnet blocks in 30 seconds
The Ethereum roadmap includes eventually embedding its own zkEVM into the core protocol, which would help avoid duplicate execution and enable other services to easily verify the correctness of execution. However, implementation could still take years.
In the meantime, state transitions can be proven using a general-purpose zkVM, which has seen significant performance improvements over the past year and provides a simple developer experience (e.g., only needing to write programs in Rust).
Proving Ethereum blocks in 30 seconds is an ambitious goal, but Risc Zero has claimed to have achieved 90 second proof times. However, in the long run, proof times need to be reduced by at least an order of magnitude to achieve real-time proofs for Ethereum. Given a 12 second block time, proofs need to be fast enough to allow time for communication, verification, and voting.
9. More than 90% of all ZK proofs across blockchains will be generated in a decentralized manner
Currently, most ZKPs are generated in a centralized manner by core teams. This is costly (less efficient in hardware utilization), reduces censorship resistance, and adds complexity for teams that need ZKPs but don’t necessarily want to run their own proof infrastructure.
While it is possible to build decentralized proofs of stake for specific networks (i.e., only for a specific L2 or use case), decentralized proof of stake networks can offer lower prices, operational simplicity, and better censorship resistance. The price advantage comes from the ability of decentralized networks to find the cheapest computing resources around the world, as well as higher utilization of hardware (users only pay for the computing resources they use).
For these reasons, it is expected that most projects will choose to outsource their proofs (several projects are already doing this), and decentralized proof networks will generate more than 90% of all ZK proofs by the end of 2025. Gevulot will be the first production-ready proof network capable of handling large proof volumes, and more will follow as the industry expands.
privasi
10. Privacy blockchain applications will have their ChatGPT moment
Before ChatGPT, most people didn’t think about the use cases of AI and LLM and their benefits. That changed overnight and today most people have interacted with LLM or at least understand how they work.
A similar shift is likely to occur in the area of blockchain privacy. While many people are still skeptical about the severity of the on-chain privacy issue (or are not even aware of it), privacy is important for protecting both individuals and businesses using blockchains, while also expanding the expressive power of blockchains (i.e., what can be built on top of them).
While privacy itself is rarely a selling point, the following framework can be used to identify the categories in which privacy is most valued:
1. The cost of transparency (not privacy) is high:
-
Individual level (e.g. political polling apps, where exposing one’s identity could make one a political opponent)
-
Business aspects (e.g. regulations related to customer data privacy or disclosure of competitive information)
2. Privacy brings direct economic benefits:
-
Better execution and avoidance of front-running (dark pools)
-
Prevent others from seeing and copying trading strategies, etc.
3. Collaboration has high friction:
-
Privacy can be a “business enabler”, especially when collaboration is impossible or costly
-
If the goal is to reduce trust in a single third party, programmable and expressive private computation is needed.
4. Enable new use cases:
-
By expanding the expressive power of blockchain, new applications that were not possible before can be realized
-
Most attractive in the long run, especially for applications that require private shared state (such as games, social graphs, etc.)
11. Zama’s MPC threshold decryption library will become the de facto standard
Zama, which develops FHE infrastructure for blockchain and AI, is expected to release its MPC decryption network library soon. This will be the first major open source library of its kind.
Given that there is little competition, it could become the de facto standard for everyone to benchmark and compare against — similar to what Arkworks and MP-SPDZ have done in the ZKP and MPC space. Much will depend on how permissive the license is, though.
12. Nym’s decentralized VPN network will reach 10% of TOR network users
Nym focuses on the base layer and network privacy. The Nym obfuscation network can be integrated into any blockchain, wallet or application to protect IP addresses and traffic patterns. Meanwhile, NymVPN provides a decentralized VPN (currently in public beta) with the following features:
-
New 5-hop Nym mix network, providing stronger privacy guarantees through advanced onion encryption, data segmentation, mixing and shielding traffic
-
2-hop secure WireGuard decentralized VPN, fast two-hop decentralized mode with onion encryption but unshielded traffic
To incentivize the supply side, Nym plans to run incentivized privacy provisioning to increase the number of nodes on its VPN network. However, for the demand side, they need to prove that their product is worth using.
10% of TOR usage (2-3 million users on average) would translate into 200,000-300,000 NymVPN users. This goal is achievable, provided the team executes effectively in terms of marketing. Cryptoeconomic incentives could also be used in the short term to memandu demand and subsidize usage.
13. At least one major Rollup provider will integrate private computing (in production)
In addition to the privacy-first approach taken by teams like Aztec, Aleo, and Namada, another approach is for existing transparent networks to outsource computations that require privacy guarantees. This add-on privacy or privacy-as-a-service approach enables applications and networks to achieve some privacy guarantees without having to redeploy to a new privacy-centric network and lose existing network effects.
There are multiple approaches to private/confidential computing, and providers include:
-
Focusing on MPC: Arcium, Nillion, Taceo, SodaLabs, etc.
-
Focusing on FHE: Zama, Fhenix, Inco, etc.
-
Focusing on TEE: Secret Network and Oasis Protocol
It is expected that at least one major rollup provider (Optimism, Arbitrum, Base, Starknet, ZK Sync, Scroll, etc.) will integrate one or more of these confidential computing providers and enable their upper-layer applications to be used in production environments.
14. More than 3 startups will raise funds to accelerate the development of IO (Indistinguishable Obfuscation)
Indistinguishable obfuscation (IO) is simply a form of kriptography that is able to hide (obfuscate) the implementation of a program while still allowing users to execute it. It involves converting a program or circuit into an obfuscated version that is difficult to reverse engineer, but the scrambled program still performs the same functions as the original program. In addition to providing verifiable computational guarantees similar to ZKP, IO can also support private multi-party computations, maintaining secrets and using them only under specific conditions.
While IO is currently slow, costly, and practically infeasible, the same was true of ZKPs a few years ago. Recent examples include teams working on MPC- and FHE-based programmable privacy in blockchains, which have made significant progress in the past year. Overall, when capable teams are well-funded, a lot of progress can be made in a seemingly short period of time.
As far as we know, only a few teams such as Sora and Gauss Labs are working on some implementations. Given the potential of IO, it is expected that at least three new startups will raise venture capital to accelerate development and make it more practical.
15. Crypto mempool adoption is still low (
Encrypted memory pools are a way to reduce harmful MEV (such as front-running and sandwich attacks) by keeping transactions encrypted (commit-reveal) until the order is determined. There are many different approaches in practice, mainly on two dimensions of trade-offs:
1. Product Integration:
-
External protocols (such as Shutter)
-
Integrate as part of a wider product (such as the shared ordering protocol Radius)
2. Trust guarantee for decryption:
-
Trusted Third Party
-
TEE
-
Threshold Decryption
-
Time Delay
While the overall benefits of crypto mempools appear positive, external protocols may have difficulty gaining adoption. On the other hand, among projects that offer crypto mempools as part of a broader product, adoption of crypto mempools depends on the success of the broader product. The clearest path to adoption is to incorporate the solution into the core protocol itself, but this may take more than a year to implement (especially for Ethereum, although it is in the roadmap).
Consensus and P2P Network
16. At least one existing network will move from PoW or BFT-based PoS to DAG-based consensus
The consensus mechanism based on directed acyclic graphs (DAGs) is able to separate the communication (data propagation) from the consensus layer (linear ordering of transactions) in a way that is more suitable for distributed systems. The data structure makes the ordering deterministic, as long as every node (eventually) has the same DAG, all nodes will eventually get the same ordering.
A key advantage of this approach is the reduced communication overhead. Instead of building and distributing official blocks, leaders only need to certify the identified sub-DAG. After receiving this certification, other nodes can deterministically build equivalent blocks locally. In addition to early pioneers Aptos and Sui, newer protocols such as Aleo have also implemented DAG-based consensus. It is expected that this trend will continue and at least one major protocol will decide to move from proof-of-work or BFT-based proof-of-stake consensus to DAG-based consensus.
Due to the complexity of implementation (even with existing implementations such as Narwhal-Bullshark or Mysticeti), the likelihood of a full transformation by the end of 2025 is low. However, if a team is able to execute quickly, this prediction could be overturned.
17. The QUIC transport layer will be open to security components other than TLS (reducing binding to HTTP)
QUIC (Quick UDP Connections) is a modern transport layer protocol developed by Google and later adopted as a standard by the Internet Engineering Task Force (IETF). It is designed to reduce latency, improve connection reliability, and increase security.
QUIC uses UDP (User Datagram Protocol) as its basis, rather than the traditional TCP used in HTTP 2/1. However, HTTP 2 benefits from decades of optimizations—both protocol-level optimizations and offloading workloads to the kernel level—which gives it a performance advantage.
While there are already some proposals to incorporate QUIC into the kernel, a QUIC implementation that does not rely on TLS will make hardware acceleration easier. This will alleviate some performance issues and may drive more use of QUIC in P2P networks. Currently, among the major blockchains, only Solana, Internet Computer, and Sui are known to use QUIC.
User Experience
18. At least one Solana application will run in a Rollup/network extension mode, but the user experience will be like at L1
While the Solana core team is focused on improving L1, the industry has observed a trend toward Solana modularity. A key difference is that Solana network extensions (L2s) are less focused on pure scaling and more focused on providing developers (and users) with new experiences that are not possible with current L1s. This includes lower latency and custom/sovereign blockspace, which is primarily applicable to use cases that work well in isolated environments and don’t rely too much on accessing shared state (such as games or certain DeFi applications).
Given the user and product-oriented nature of the broader Solana ecosystem, this is expected to extend to these network extensions as well. Expect to see at least one Solana application launched as a rollup/network extension, but users won’t notice they have left Solana L1. Potential competitors include applications built on Magic Block or Bullet (ZetaX).
A great example in the Ethereum ecosystem is Payy – a mobile app that provides private USDC payments. It has an easy onboarding flow and a smooth user experience, but in the background it runs as an Ethereum validium built on the Polygon technology stack.
*Disclaimer: Equilibrium Ventures is an investor in Magic Block and Zeta.
19. More than 25% of on-chain transactions will be generated in a chain-abstract manner
Chain abstraction is an umbrella term for a variety of approaches that are used to abstract away the complexity of navigating blockchains, especially in a multi-chain world. While early adopters (expert users) are willing to go through more hassles, chain abstraction can provide a reasonable tradeoff for less experienced users. Another way to look at it is risk transfer, which is trusting an external party (such as an intent resolver) to manage and handle multi-chain complexity on behalf of the user.
It is expected that by the end of 2025, at least 25% of all on-chain transactions will be generated in a chain-abstract manner, meaning that end users do not need to know which underlying chain they are using.
While chain abstraction does increase trust assumptions and obscure risk, something like an on-chain rating agency (e.g. L2 Beat, etc.) could emerge that rates different solutions. This would allow users to set preferences, such as only interacting with chains above a certain security level (such as rollups with forced exits). Another risk factor relates to the solver market, which should be competitive enough to ensure users get good results and minimize censorship risk.
Ultimately, expert users can still choose to operate in the same way as before, while those who do not feel expert enough about the different options can outsource the decision making to a more professional third party.
20. Most new Rollups will be launched on the ZK stack with native interoperability
Based on the effectiveness of the shared L1 bridge design, rollup clusters provide stronger (asynchronous) interoperability guarantees than their counterparts. With each additional rollup launched, the network effect of the rollup cluster increases.
Most new rollups expected to launch in 2025 will be built on the ZK stack with native interoperability. While the cluster consists of multiple different chains, the goal is to make users feel like they are using a single chain. This allows developers to focus more on applications, user experience, and onboarding flows.
Meringkaskan
Infrastructure and expansion
We are already starting to see the first applications expand their user base, but there is still a lot of work to be done to ensure that the underlying infrastructure can accommodate more users and wider applications.
Despite significant progress made during past bear markets, new scaling bottlenecks and the need for infrastructure financing will emerge. This is a dynamic that has been observed in multiple cycles, and there is no reason to think it will be different this time. In other words, there is no such thing as full capacity. Every time capacity increases, new use cases become feasible, driving up demand for block space.
Privacy issues
Privacy is probably the last major problem to be solved in blockchain. Currently, the understanding of the future roadmap is relatively clear, and the key is to integrate all the parts and improve performance. The recent positive decision in the Tornado Cash case has raised expectations for a more open attitude by the government, but there is still a lot of work to be done at the technical and social levels.
User Experience
The industry has done a pretty good job of abstracting complexity in terms of single blockchain usage over the past few years. However, as more and more new chains and L2/L3 are launched, optimizing the cross-chain user experience becomes increasingly critical.
ZK Proof Technology
Multiple predictions for next year are based on ZK proofs becoming cheaper and faster, enabling more use cases. This trend is expected to continue in 2025, driven primarily by:
Software Optimization
More professional hardware
Decentralized Proof of Stake Network
-
Can search for the cheapest computing resources around the world
-
Allows users to avoid paying for idle time
Overall, the outlook for 2025 is promising and the industry will continue to move forward.
This article is sourced from the internet: Looking Ahead to 2025: 20 Predictions from Scaling to Privacy
Original | Odaily Planet Daily ( @OdailyChina ) Author | Fu Howe ( @vincent 31515173 ) While the AI and life science meme wave continues, TikTok has once again brought memes to new traffic heights. TikTok meme coin CHILL GUY has been rising since the 19th, with a 24-hour trading volume of over $300 million and a market value of $500 million, which has attracted the markets attention to TikTok meme. At the same time, many popular TikTok meme coins have been created, and the market FOMO sentiment has continued to increase. But which TikTok meme coins have really come out? As Buffett said, only after the tide has passed can you tell who is swimming naked. Odaily Planet Daily also experienced the TikTok meme wave in depth at the…