छिपे हुए खतरे जिन्हें नज़रअंदाज़ नहीं किया जा सकता: BTC लेयर 2 तकनीक की सुरक्षा चुनौतियाँ और खतरे
This article Hash ( एसएचए1 ): a9cd1d6904562d958f8347fae26c5e32cfbf63d1
No.: Lianyuan Security Knowledge No.018
Bitcoin (BTC) is an open source cryptocurrency system based on blockchain decentralized consensus and runs through peer-to-peer network communication. It is maintained by computer networks and nodes around the world. However, with the continuous development and growth of the crypto community and ecosystem, the early BTC technology can no longer meet the users demand for the scalability of the cryptocurrency system. Directly modifying the underlying BTC protocol is not only complicated, but also faces huge community resistance, increases system risks, and may cause hard forks and community splits. Therefore, the BTC Layer 2 solution becomes a more suitable choice – by building a new layer, it is compatible with BTC without changing BTC, and meets the users demand for scalability. The ChainSource Security Team comprehensively analyzed the security of BTC Layer 2 from multiple aspects such as L2 solutions, protective measures and future development, hoping to provide valuable reference for everyone.
BTC Layer 2 solutions and potential security issues
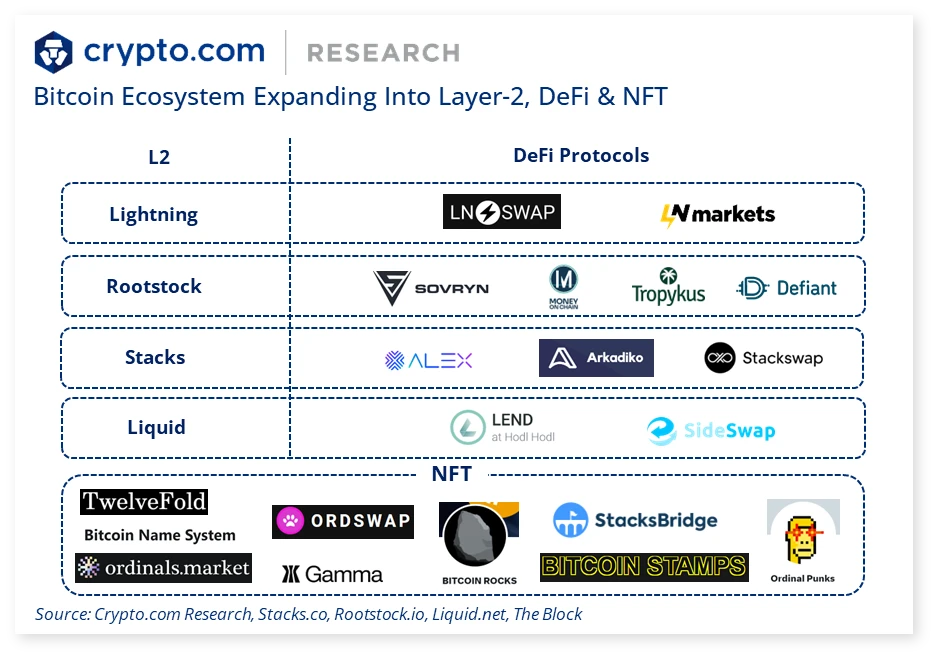
BTC Layer 2 refers to the second-layer expansion technology of Bitcoin (BTC), which aims to increase the transaction speed of Bitcoin, reduce handling fees, and increase scalability, solving a series of problems faced by BTC. There are many BTC Layer 2 solutions at present, and the more well-known ones are Lightning Network, Rootstock, Stacks, etc. In addition, some projects and protocols such as Liquid, Rollkit, RGB, etc. also have certain usage scenarios.
1. लाइटनिंग नेटवर्क
The Lightning Network is probably the most well-known BTC Layer 2 solution. It operates as an off-chain network that allows participants to conduct fast, low-cost transactions without having to record every transaction on the Bitcoin blockchain. By creating a network of payment channels, the Lightning Network supports microtransactions and significantly reduces congestion on the main chain.
Use scenarios:
Micropayments/peer-to-peer payments/e-commerce and retail transactions for content creators.
प्रमुख विशेषताऐं:
-
Instant Payments: Transactions are settled instantly.
-
Low Fees: Fees are extremely low, suitable for micro-transactions.
-
Scalability: Ability to handle millions of transactions per second.
Security Question:
-
Channel Attacks: The Lightning Network relies on payment channels, which can be attacked by attackers exploiting stale transactions or fraudulent channel closures.
-
Liquidity issues: If funds are concentrated in a few nodes, these nodes may become targets of attack, resulting in reduced decentralization of the network.
-
Network Splitting Attacks An attacker may attempt to split the network, causing different parts of the network to become out of sync with each other.
2. Rootstock (RSK)
Rootstock, or RSK for short, is a smart contract platform built on Bitcoin. It leverages the security of Bitcoin while supporting smart contracts compatible with Ethereum. RSK runs as a sidechain of Bitcoin, using a two-way anchor mechanism to allow BTC to flow between the Bitcoin network and the RSK blockchain.
Use scenarios:
Decentralized Finance (DeFi) applications/issuing tokens on the Bitcoin network/cross-chain applications.
प्रमुख विशेषताऐं:
-
Smart Contract: Compatible with Ethereum and supports DeFi applications.
-
Merged mining: Bitcoin miners can mine RSK simultaneously, enhancing network security.
-
Interoperability: Bridging Bitcoin and Ethereum-like functionality.
Security Question:
-
Double-Spending: RSK as a sidechain may be subject to double-spending attacks in some cases, especially when transferring BTC between Bitcoin and RSK.
-
Smart contract vulnerabilities: RSK allows the deployment of smart contracts, which makes it also face the risks of smart contract vulnerabilities similar to Ethereum, such as reentrancy attacks, integer overflows, etc.
3. Stacks
Stacks is a unique Layer 2 solution that brings smart contracts and decentralized applications (dApps) to Bitcoin. Unlike other Layer 2s, Stacks introduces a new consensus mechanism – Proof of Transfer (PoX), which anchors Stacks transactions to the Bitcoin blockchain.
Use scenarios:
lNFT platform/decentralized finance (DeFi) services/governance and identity solutions.
प्रमुख विशेषताऐं:
-
Smart Contracts: Clarity, a secure language designed for predictable smart contracts.
-
Bitcoin Anchored: Transactions are secured by Bitcoin.
-
Decentralized Applications (dApps): Allow developers to build decentralized applications on Bitcoin.
Security Question:
-
Consensus Attacks: Since Stacks’ consensus mechanism PoX relies on the Bitcoin network, attackers may attempt to influence Stacks’ consensus by manipulating the Bitcoin network.
-
Smart Contract Vulnerabilities: Similar to other smart contract platforms, Stacks is also exposed to potential vulnerabilities in smart contract code.
4. Liquid
Liquid is a sidechain-based Layer 2 solution dedicated to improving Bitcoins transaction speed and privacy. Developed by Blockstream, Liquid is particularly suitable for traders and exchanges, supporting faster settlement and confidential transactions.
Use scenarios:
High-frequency trading/cross-border payments/tokenized asset issuance.
प्रमुख विशेषताऐं:
-
Confidential Transactions: Transaction amounts are hidden to enhance privacy.
-
Fast Settlement: Trades settle in approximately 2 minutes.
-
Asset issuance: Allows the creation of digital assets on the Bitcoin network.
Security Question:
-
Mainchain Dependency Risks: As a sidechain, Liquid relies on the security of the Bitcoin mainnet. Any attacks or vulnerabilities on the mainnet may affect Liquid.
-
Privacy Risk: Although Liquid supports confidential transactions, privacy can still be compromised if keys are not managed properly.
5. Rollkit
Rollkit is an emerging project that aims to bring Rollups, a popular scaling solution in the Ethereum ecosystem, to Bitcoin. Rollups aggregate multiple transactions into a single batch before submitting them to the Bitcoin blockchain, reducing network load and lowering fees.
Use scenarios:
Scalable DeFi applications/micropayment aggregation/high-throughput decentralized applications.
प्रमुख विशेषताऐं:
-
Scalability: Significantly increase transaction throughput.
-
Cost efficiency: Reduce fees by batching transactions.
-
Security: Inherits Bitcoin’s security model.
Security Question:
-
Data Availability Attacks: In the Rollups scheme, if the data is unavailable, the validator may be unable to verify the validity of the transaction.
-
Economic incentive issues: Rollups need to design strong economic incentive mechanisms to prevent participants from trying to gain benefits through improper means.
6. RGB
RGB is a smart contract system that leverages Bitcoins UTXO model. It is designed to support complex smart contracts while maintaining Bitcoins privacy and scalability. RGB focuses on creating an off-chain environment where smart contracts can be executed with minimal impact on the main chain.
Use scenarios:
Asset tokenization/privacy applications/flexible smart contract development.
प्रमुख विशेषताऐं:
-
UTXO-based: Maintaining Bitcoin’s security and privacy features.
-
Off-chain execution: Minimizes on-chain usage.
-
Customization: Supports a wide range of smart contract application scenarios.
Security Question:
-
Complexity risk of smart contracts: Smart contracts in the RGB system may be very complex, leading to increased potential security vulnerabilities.
-
Credibility issues of off-chain execution: RGB relies on the off-chain environment to execute smart contracts. If the execution environment is attacked or manipulated, it may affect the security of the contract.
Existing safety measures
The BTC Layer 2 solution shows great potential in improving the scalability and functionality of the Bitcoin network, but it also introduces a series of new security challenges. Security will become one of the key factors for its success and widespread application. In order to deal with potential security risks, BTC Layer 2 can take the following major security precautions:
-
Channel security and capital protection
Multisig Timelocks: For example, in the Lightning Network, funds are usually stored in multi-signature addresses, and funds can only be transferred after all relevant parties reach a consensus. The time lock mechanism ensures that in the event of a dispute, the funds are not permanently locked and can eventually be returned to the owner.
Reliability of off-chain transactions: By using off-chain transactions, users can make transactions quickly, but these transactions still need to be synchronized with the main chain regularly to prevent double spending or loss of funds.
-
Fraud Proofs and Challenge Mechanisms
Fraud Proofs: In some Layer 2 solutions (such as Rollup), fraud proofs are used to detect and respond to malicious operations. For example, if a party attempts to submit an invalid state update, other participants can challenge it through fraud proofs to prevent invalid transactions from being uploaded to the chain.
Challenge Period: Gives users a period of time to review and challenge suspicious transactions, thereby improving the security of the network.
-
Network and protocol robustness
Protocol upgrades and audits: The protocol is regularly reviewed and upgraded to fix known vulnerabilities and enhance security. For example, in Rootstock or Stacks, code audits and community reviews are critical to ensuring the security of smart contracts.
Decentralized operation nodes: By increasing the degree of node distribution, the possibility of single point failure in the network is reduced, thereby improving the networks anti-attack capability.
-
Privacy and Data Protection
Encrypted communication: Ensures that communications between all participants are encrypted to prevent man-in-the-middle attacks or data leaks.
Zero-Knowledge Proofs: In some Layer 2 solutions, zero-knowledge proofs are introduced to enhance privacy and security and avoid leaking sensitive information of the transaction parties.
-
User education and risk warnings
Improve user security awareness: educate users about the risks of the second-layer network and encourage them to use reliable wallets and safe operations.
Risk Warning: When using Layer 2 solutions, users are alerted to possible risks, such as the complexity of off-chain transactions or disputes when channels are closed.
-
Security of off-chain transactions
State Channel Security: Ensure the integrity of the off-chain state and submit state updates to the main chain regularly to reduce the risk of fund theft or fraud.
These measures work together to ensure the security of the Bitcoin Layer 2 network and provide users with a reliable and scalable trading environment.
Future security trends
The industry is changing rapidly, and new BTC L2 is born every second, but what remains unchanged is the inevitable trend of BTC ecology to develop towards the second layer. BTC is a train that everyone wants to get on. Despite the challenges, the future of BTC ecology is full of infinite possibilities. From the consensus of fair distribution to the expansion plan based on inscriptions, and then to the pursuit of a fully mature expansion plan that shares strong security with BTC, the Bitcoin ecology is undergoing a historic change:
-
Unlocking the DeFi Market: By enabling features such as EVM-compatible Layer 2 solutions, Bitcoin can enter the multi-billion dollar DeFi market. This not only expands the utility of Bitcoin, but also unlocks new financial markets that were previously only accessible through Ethereum and similar programmable blockchains.
-
Expanded use cases: These Layer 2 platforms support not only financial transactions, but also a variety of applications in fields such as finance, games, NFTs, or identity systems, greatly expanding the original scope of Bitcoin as a simple currency
The second-layer network uses zero-knowledge proofs to enhance security, Rollup technology to improve scalability, fraud proofs to ensure the security of its transactions, etc. These technologies are not only expected to significantly improve the scalability and efficiency of the BTC network, but will also introduce new asset types and trading methods, opening up new opportunities for users and developers. However, the successful achievement of these goals requires the joint efforts of community consensus, technological maturity, and practical verification. In the process of exploring the most effective L2 solution, security, decentralization, and optimized user experience will remain top priorities. Looking to the future, with technological advancement and community collaboration, BTC L2 technology is expected to unleash new potential for the Bitcoin ecosystem and bring more innovation and value to the world of cryptocurrency.
निष्कर्ष
Driven by the huge market demand and the free competition in the market, technological innovation will definitely emerge. The future of L2 solutions is closely related to the overall development of blockchain technology. By deeply analyzing the solutions and potential security challenges of BTC Layer 2, we reveal the risks it faces in smart contracts, identity authentication, data protection, etc. Although there are currently a variety of protection measures, with the continuous development of technology, BTC Layer 2 still needs to continue to innovate in ZK technology, cross-chain security, and even quantum encryption to meet future security challenges. As blockchain technology matures further, we can foresee that there will be more innovations and changes. First, with the continuous maturity and standardization of technology, L2 solutions will be more stable and reliable. Secondly, with the continuous expansion of the ecosystem, Bitcoin will be applied in more scenarios and industries, thereby further promoting the development of the entire cryptocurrency industry. In general, the intensive launch of the mainnet of the Bitcoin Layer 2 project marks a new milestone for the Bitcoin network.
लियानयुआन टेक्नोलॉजी एक ऐसी कंपनी है जो ब्लॉकचेन सुरक्षा पर केंद्रित है। हमारे मुख्य कार्य में ब्लॉकचेन सुरक्षा अनुसंधान, ऑन-चेन डेटा विश्लेषण और परिसंपत्ति और अनुबंध भेद्यता बचाव शामिल है। हमने व्यक्तियों और संस्थानों के लिए कई चोरी की गई डिजिटल संपत्तियों को सफलतापूर्वक पुनर्प्राप्त किया है। साथ ही, हम उद्योग संगठनों को परियोजना सुरक्षा विश्लेषण रिपोर्ट, ऑन-चेन ट्रेसबिलिटी और तकनीकी परामर्श/सहायता सेवाएं प्रदान करने के लिए प्रतिबद्ध हैं।
पढ़ने के लिए धन्यवाद। हम ब्लॉकचेन सुरक्षा सामग्री पर ध्यान केंद्रित करना और उसे साझा करना जारी रखेंगे।
This article is sourced from the internet: Hidden dangers that cannot be ignored: security challenges and threats of BTC Layer 2 technology
Related: एयरड्रॉपs are not dead, but don’t chase hot projects too much
Original article by Axel Bitblaze Original translation: TechFlow With all the major airdrops like $ZRO and $ZK now complete, the sentiment around airdrops seems to have cooled down a bit. So, is the airdrop beta over? Are they still worth farming? What’s next for airdrops? I’ll share my thoughts in this post. What’s next for the airdrop? A few months ago I wrote an article about “Current Airdrop Betas” where I mentioned that there were three major airdrop projects that had yet to be launched. Now that they have all been completed, here are my thoughts on the upcoming betas. ( See tweet for details) Are airdrops dead? The short answer is no. The longer answer is that airdrops vary. It can be understood that in games, there will always…