Beosin: 2024 Web3 Blockchain Security Situation Annual Report

Préface
This research report was initiated by the Blockchain Security Alliance and co-authored by alliance members Beosin and Footprint Analytics. It aims to comprehensively explore the development of global blockchain security in 2024. Through the analysis and evaluation of the current status of global blockchain security, the report will reveal the current security challenges and threats, and provide solutions and best practices.
Through this report, readers will be able to gain a more comprehensive understanding of the dynamic evolution of the Web3 blockchain security situation. This will help readers evaluate and respond to the security challenges facing the blockchain field. In addition, readers can also obtain useful suggestions on security measures and industry development directions from the report to help them make wise decisions and actions in this emerging field. Blockchain security and regulation are key issues in the development of the Web3 era. Through in-depth research and discussion, we can better understand and respond to these challenges and promote the security and sustainable development of blockchain technology.
1. Overview of Web3 blockchain security situation in 2024
 According to the Alert platform of security audit company Beosin, the total loss of Web3 due to hacker attacks, phishing scams and project party Rug Pulls reached 2.513 billion US dollars in 2024. Among them, there were 131 major attack incidents with a total loss of about 1.792 billion US dollars; 68 project party Rug Pull incidents with a total loss of about 148 million US dollars; the total loss of phishing scams was about 574 million US dollars.
According to the Alert platform of security audit company Beosin, the total loss of Web3 due to hacker attacks, phishing scams and project party Rug Pulls reached 2.513 billion US dollars in 2024. Among them, there were 131 major attack incidents with a total loss of about 1.792 billion US dollars; 68 project party Rug Pull incidents with a total loss of about 148 million US dollars; the total loss of phishing scams was about 574 million US dollars.
In 2024, the amount of hacker attacks and phishing scams increased significantly compared to 2023, among which phishing scams surged by 140.66% compared to 2023. The amount of losses in the Rug Pull incident of the project party decreased significantly, down by about 61.94%.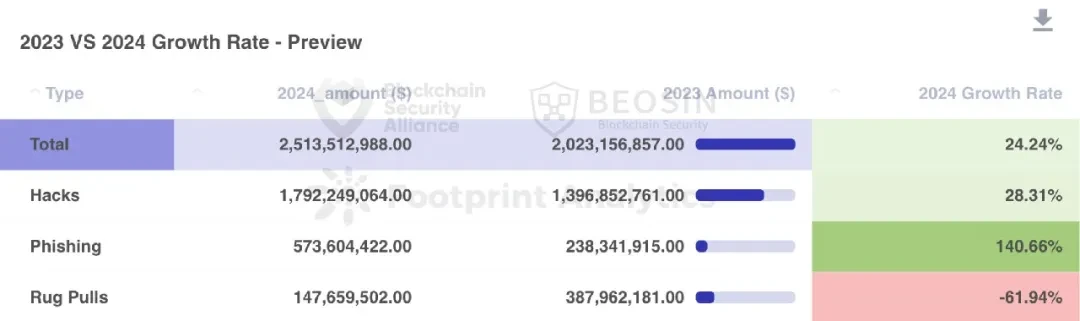
The types of projects attacked in 2024 include DeFi, CEX, DEX, public chains, cross-chain bridges, wallets, payment platforms, gambling platforms, crypto brokers, infrastructure, password managers, development tools, MEV robots, TG robots, etc. DeFi is the most frequently attacked project type, and 75 attacks on DeFi caused a total loss of approximately US$390 million. CEX is the project type with the highest total loss amount, and 10 attacks on CEX caused a total loss of approximately US$724 million.
In 2024, more types of public chains were attacked, and there were multiple security incidents of theft on multiple chains. Ethereum is still the public chain with the highest loss. 66 attacks on Ethereum caused a loss of approximately US$844 million, accounting for 33.57% of the total loss for the year.
In terms of attack methods, 35 private key leakage incidents caused a total loss of approximately US$1.306 billion, accounting for 51.96% of the total losses, which was the attack method that caused the most losses.
Contract vulnerability exploitation is the most common attack method. Among 131 attack incidents, 76 were caused by contract vulnerability exploitation, accounting for 58.02%.
About $531 million of stolen funds were recovered throughout the year, accounting for about 21.13%. About $109 million of stolen funds were transferred to mixers throughout the year, accounting for about 4.34% of the total stolen funds, a decrease of about 66.97% compared to 2023.
2. Top 10 Security Events in Web3 Ecosystem in 2024
In 2024, there were five attacks with losses exceeding 100 million USD: DMM Bitcoin ($304 million), PlayDapp ($290 million), WazirX ($235 million), Gala Games ($216 million) and Chris Larsen theft ($112 million). The total loss of the top 10 security incidents was approximately $1.417 billion, accounting for approximately 79.07% of the total amount of annual attacks.
No.1 DMM Bitcoin
Amount of loss: $304 million
Attack method: private key leakage
On May 31, 2024, the Japanese cryptocurrency exchange DMM Bitcoin was attacked and more than $300 million worth of Bitcoin was stolen. The hackers dispersed the stolen funds to more than 10 addresses in an attempt to launder them.
No.2 PlayDapp
Amount of loss: $290 million
Attack method: private key leakage
On February 9, 2024, the blockchain gaming platform PlayDapp was attacked, and hackers minted 2 billion PLA tokens worth $36.5 million. After negotiations with PlayDapp failed, on February 12, hackers minted another 15.9 billion PLA tokens worth $253.9 million and sent part of the funds to the Gate exchange. The PlayDapp project team subsequently suspended the PLA contract and migrated the PLA tokens to PDA tokens.
No.3 WazirX
Amount of loss: $235 million
Attack methods: Cyber attacks and phishing
On July 18, 2024, more than $230 million was stolen from a multi-signature wallet of WazirX, an Indian cryptocurrency exchange. The multi-signature wallet was a Safe wallet smart contract wallet. The attacker induced the multi-signature signer to sign a contract upgrade transaction. The attacker directly transferred the assets in the wallet through the upgraded contract, and eventually transferred out all the assets of more than $230 million.
No.4 Gala Games
Amount of loss: $216 million
Attack method: Access control vulnerability
On May 20, 2024, a privileged address of Gala Games was controlled. The attacker used the mint function of the token through the address to directly mint 5 billion GALA tokens, worth about 216 million US dollars, and exchanged the additional tokens for ETH in batches. Subsequently, the Gala Games team used the blacklist function to stop the hacker and recovered the losses.
No.5 Chris Larsen (Ripples co-founder)
Amount of loss: $112 million
Attack method: private key leakage
On January 31, 2024, Chris Larsen, co-founder of Ripple, said that four of his wallets were hacked, resulting in a total loss of approximately $112 million. The Binance team successfully froze $4.2 million worth of stolen XRP tokens.
No.6 Munchables
Amount of loss: $62.5 million
Attack method: social engineering attack
On March 26, 2024, Munchables, a Web3 gaming platform based on Blast, was attacked and lost approximately $62.5 million. The project was attacked because it hired North Korean hackers as developers. All stolen funds were eventually returned by the hackers.
No.7 BTCTurk
Amount of loss: $55 million
Attack method: private key leakage
On June 22, 2024, the Turkish cryptocurrency exchange BTCTurk was hacked, losing approximately $55 million. Binance assisted in freezing more than $5.3 million in stolen funds.
No.8 Radiant Capital
Amount of loss: $53 million
Attack method: private key leakage
On October 17, 2024, the multi-chain lending protocol Radiant Capital was attacked, and the attacker illegally obtained the permissions of three owners in the Radiant Capital multi-signature wallet. Since the multi-signature wallet uses the 3/11 signature verification mode, the attacker used these three private keys to sign off-chain, and then initiated an on-chain transaction to transfer the ownership of the Radiant Capital contract to a malicious contract controlled by the attacker, causing a loss of more than $53 million.
No.9 Hedgey Finance
Amount of loss: $44.7 million
Attack method: Contract vulnerability
On April 19, 2024, Hedgey Finance was attacked multiple times by attackers. The attackers exploited the token approval vulnerability and stole a large number of tokens from the ClaimCampaigns contract, with the value of tokens stolen from the Ethereum chain exceeding $2.1 million and the value of tokens stolen from the Arbitrum chain being approximately $42.6 million.
No.10 BingX
Amount of loss: $44.7 million
Attack method: private key leakage
On September 19, 2024, the hot wallet of BingX exchange was hacked. Although BingX launched an emergency plan, including emergency transfer of assets and suspension of withdrawals, according to Beosin statistics, the total loss of abnormal outflow of assets from the hot wallet was as high as 44.7 million US dollars, and the stolen assets involved multiple blockchains such as Ethereum, BNB Chain, Tron, Polygon, Avalanche, and Base.
3. Types of Attacked Projects
In addition to common types such as DeFi, CEX, DEX, public chains, cross-chain bridges, wallets, etc., the types of projects attacked in 2024 also appeared in payment platforms, gambling platforms, crypto brokers, infrastructure, password managers, development tools, MEV robots, TG robots and other project types.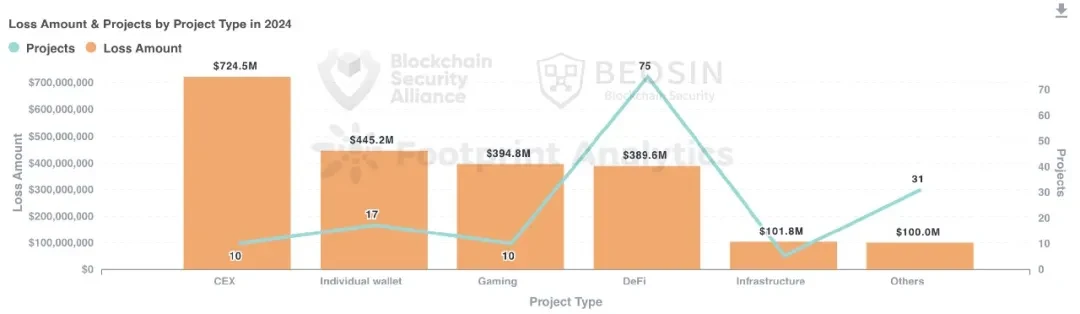
In 2024, there were 75 attacks on DeFi projects, making it the most attacked project type (about 50.70%). The total loss amount from DeFi attacks was about 390 million US dollars, accounting for about 15.50% of all losses, making it the fourth largest project type in terms of loss amount.
The CEX (centralized exchange) ranked first in terms of loss amount, with 10 attacks causing a total loss of approximately US$724 million, making it the project type with the largest loss amount. Overall, exchange-type security incidents occurred frequently in 2024, and exchange security is still the biggest challenge for the Web3 ecosystem.
The second largest loss was in personal wallets, with a total loss of approximately $445 million. 12 attacks on crypto whales and a large number of phishing attacks and social engineering attacks on ordinary users caused the total loss of personal wallets to surge by 464.72% compared to 2023, becoming the second largest challenge after exchange security.
4. Loss Amount of Each Chain
Compared with 2023, the types of public chains attacked in 2024 are also more extensive. The top five in terms of loss amount are Ethereum, Bitcoin, Arbitrum, Ripple, and Blast:

The top six by number of attacks are
Ethereum, BNB Chain, Arbitrum, Others, Base, Solana:
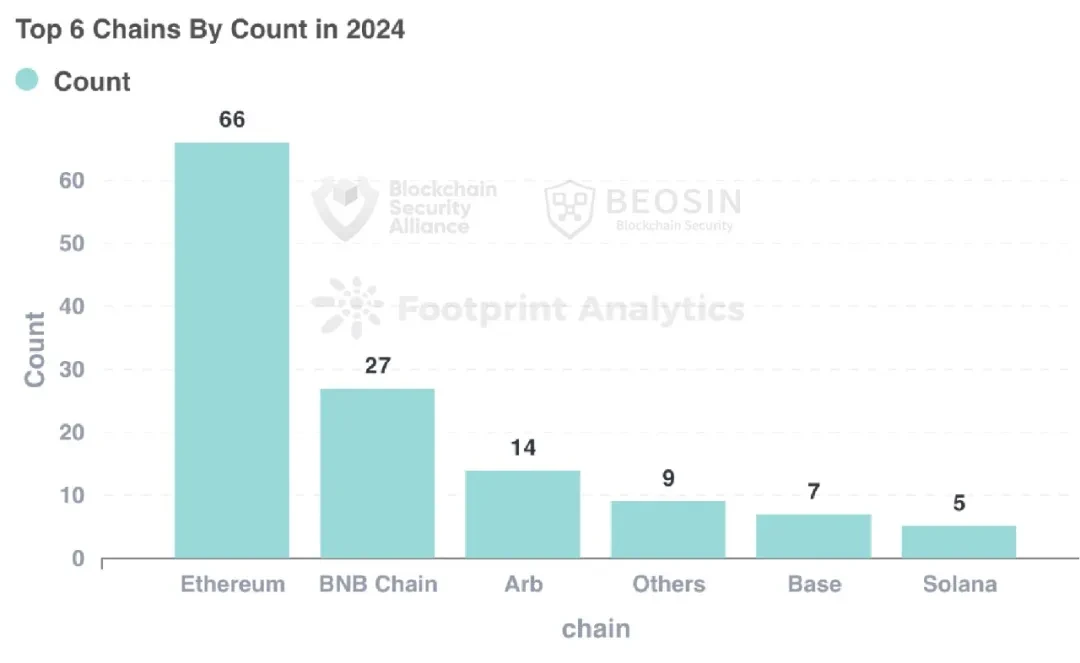
Similar to 2023, Ethereum is still the public chain with the highest loss. 66 attacks on Ethereum caused a loss of approximately US$844 million, accounting for 33.59% of the total losses for the year.
Note: The total loss data does not include on-chain phishing losses and some CEX hot wallet losses
Bitcoin network losses ranked second, with a single security incident loss of $238 million. Arbitrum ranked third, with a total loss of approximately $114 million.
5. Analysis of attack methods
The attack methods in 2024 are very diverse. In addition to the common contract vulnerability attacks, there are many other attack methods, including: supply chain attacks, third-party service provider attacks, man-in-the-middle attacks, DNS attacks, front-end attacks, etc.
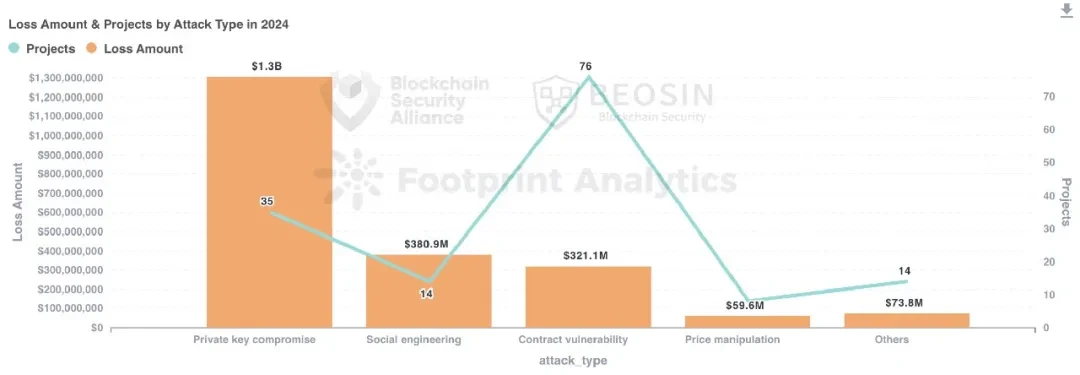
In 2024, 35 private key leaks caused a total loss of $1.306 billion, accounting for 51.96% of the total loss, which is the attack method that caused the most losses. The private key leaks that caused large losses include: DMM Bitcoin ($304 million), PlayDapp ($290 million), Ripple co-founder Chris Larsen ($112 million), BTCTurk ($55 million), Radiant Capital ($53 million), BingX ($44.7 million), DEXX ($21 million).
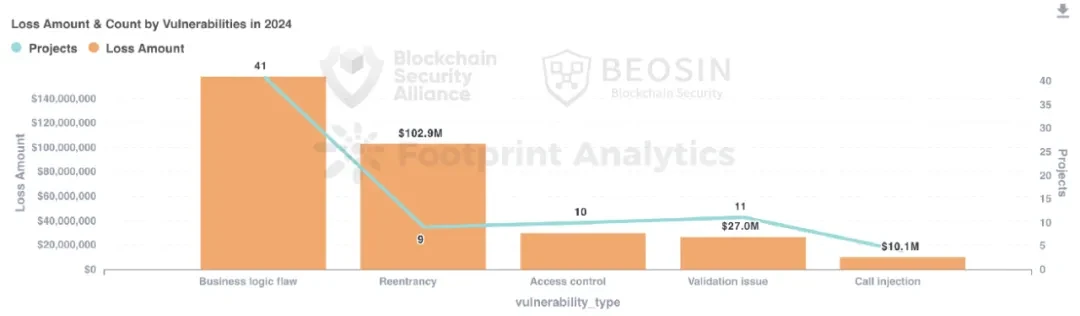
Contract vulnerability exploitation is the most common attack method. Among the 131 attacks, 76 were caused by contract vulnerability exploitation, accounting for 58.02%. The total loss caused by contract vulnerabilities was approximately US$321 million, ranking third in terms of loss amount.
According to the vulnerability classification, business logic vulnerabilities occur most frequently and cause the most losses. About 53.95% of the losses in contract vulnerability incidents come from business logic vulnerabilities, causing a total loss of approximately US$158 million.
6. Analysis of typical anti-money laundering incidents
6.1 Polter Finance Security Incident
Event Summary
On November 17, 2024, according to the Beosin Alert monitoring warning, the FTM on-chain lending protocol Polter Finance was attacked. The attacker manipulated the token price in the project contract through flash loans to make a profit.
Vulnerability and Funding Analysis
The LendingPool contract (0x d 47 ae 558623638 f 676 c 1 e 38 dad 71 b 53054 f 54273) attacked in this incident uses 0x 6808 b 5 ce 79 d 44 e 89883 c 5393 b 487 c 4296 abb 69 fe as the oracle, which uses the recently deployed feed contract (0x 80663 edff 11 e 99 e 8 e 0 b 34 cb 9 c 3 e 1 ff 32 e 82 a 80 fe). This feed contract uses the token reserves in the uniswap V2_pair (0x Ec 71) contract, which can be used by attackers for flash loans, to calculate the price, so the contract has a price manipulation attack vulnerability.
The attacker used flash loans to falsely push up the value of $BOO tokens and lend other crypto assets. The stolen funds were then converted into FTM tokens by the attacker and then transferred across chains to the ETH chain, where all funds were stored. The following is a schematic diagram of the fund flow process on the ARB chain and the ETH chain:
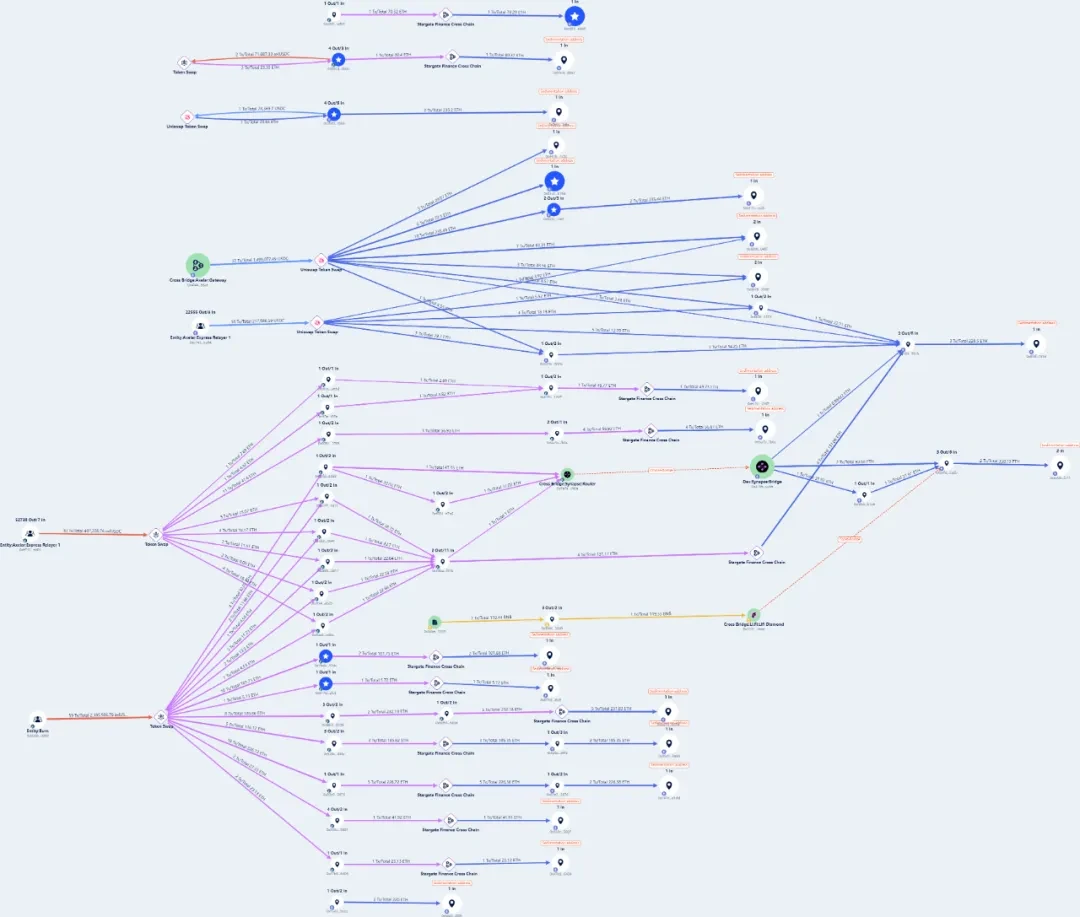
On November 20, the attacker continued to transfer more than 2,625 ETH to Tornado Cash, as shown in the figure below:

6.2 BitForex Security Incident
Event Summary
On February 23, 2024, ZachXBT, a well-known on-chain detective, disclosed through his analysis tools that BitForexs hot wallet had an outflow of approximately US$56.5 million, and in the process, the platform suspended withdrawal services.
Funding Analysis
The Beosin security team conducted an in-depth tracking and analysis of the BitForex incident through Trace:
Éthereum
At 6:11 (UTC+8) on February 24, 2024, Bitforex exchange began to transfer 40,771 USDT, 258,700 USDC, 148.01 ETH and 471,405 TRB to the Ethereum runaway address (0xdcacd7eb6692b816b6957f8898c1c4b63d1fc01f).
Subsequently, on August 9th, Beijing time, the runaway address transferred all tokens except TRB (including 147.9 ETH, 40,771 USDT and 258,700 USDC) back to the Bitforex exchange account (0xcce7300829f49b8f2e4aee6123b12da64662a8b8).
Then, from November 9 to November 10, Beijing time, the runaway address transferred 355,000 TRB to four different OKX exchange user addresses through 7 transactions:
0x274c481bf400c2abfd2b5e648a0056ef34970b0a
0x45798ca76a589647acc21040c50562dcc33cf6bf
0x712d2fd67fe65510c5fad49d5a9181514d94183d
0xe8ec263ad9ee6947bf773837a2c86dff3a737bba
The runaway address then transferred the remaining 116,414.93 TRB to a transfer address (0xbb217bd37c6bf76c6d9a50fefc21caa8e2f2e82e), which then transferred all TRB to two different Binance exchange users in two transactions:
0x431c916ef45e660dae7cd7184e3226a72fa50c0c
0x e 7 b 1 fb 77 baaa 3 bba 9326 af 2 af 3 c d5 857256519 df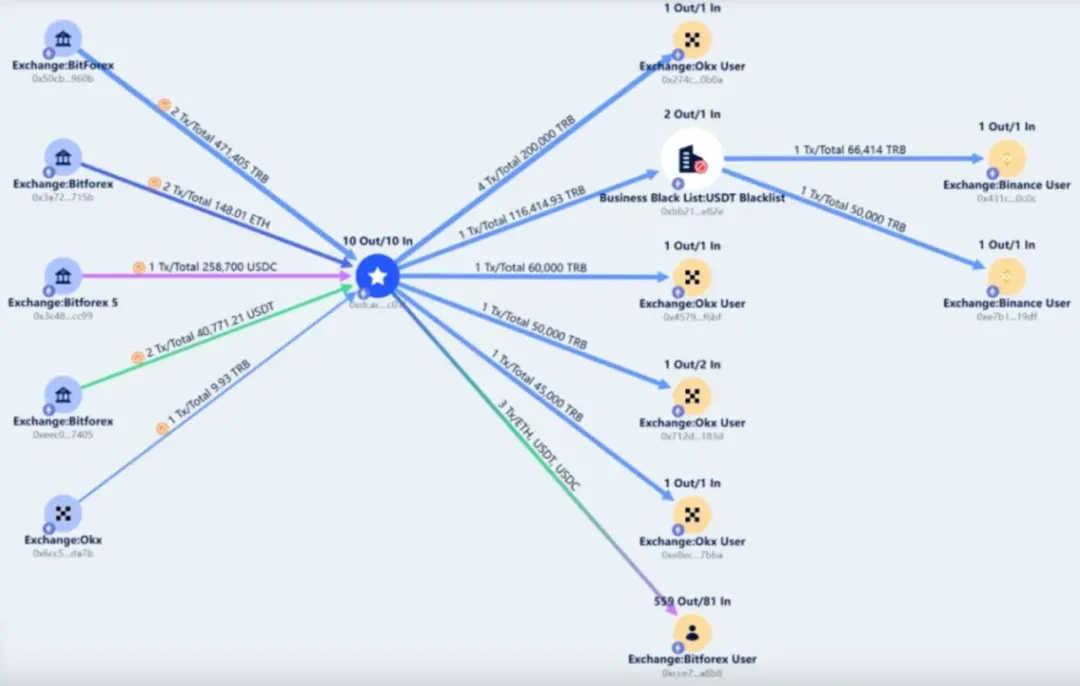
BNB Chain
On February 24, 166 ETH, 46,905 USDT and 57,810 USDC were withdrawn from Bitforex to the BNB Chain address (0x dcacd 7 eb 669 2b 816 b 6957 f 8898 c 1 c 4 b 6 3d 1 fc 01 f) and have been deposited to date. 
Polygone
On February 24th, Beijing time, Bitforex exchange withdrew 99,000 MATIC, 20,300 USDT and 1,700 USDC to the POL chain address: 0xdcacd7eb6692b816b6957f8898c1c4b63d1fc01f.
Among them, 99,000 MATIC were transferred to the address 0x cce 7300829 f 49 b 8 f 2 e 4 aee 6123 b 1 2d a 64662 a 8 b 8 on August 9 and have been deposited to date, and the remaining USDT and USDC tokens have been deposited to date.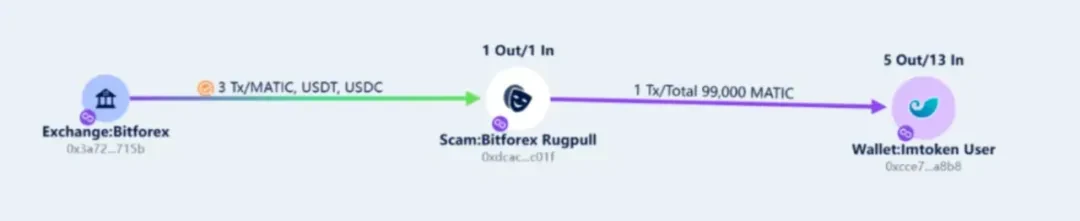
TRON
On February 24, Bitforex exchange withdrew 44,000 TRX and 657,698 USDT to the TRON chain address TQcnqaU 4 NDTR 86 eA 4 FZneeKfJMiQi 7 i 76 o. On August 9, all the above tokens were transferred back to the Bitforex exchange user address: TGiTEXjqx 1 C 2 Y 2 ywp 7 gTR 8 aYGv 8 rztn 9 uo.
Bitcoin
Starting from February 24, 16 Bitforex addresses transferred a total of 5.7 BTC to the BTC chain address 3D bbF 7 yxCR 7 ni 94 ANrRkf V1 2 rJoxrmo 1 o 2. This address transferred all 5.7 BTC back to the Bitforex exchange address on August 9: 11 dxPFQ 8 K 9 pJefffHE 4 HUwb 2 aprzLUqxz.
In summary, on February 24, Bitforex exchange transferred 40,771 USDT, 258,700 USDC, 148.01 ETH and 471,405 TRB to the ETH chain; 44,000 TRX and 657,698 USDT to the TRON chain; 5.7 BTC to the BTC chain; 166 ETH, 46,905 USDT and 57,810 USDC to the BNB Chain; and 99,000 MATIC, 20,300 USDT and 1,700 USDC to the Polygon chain. On August 9, all BTC chain tokens, all TRON chain tokens, and ETH chain tokens except TRB were transferred back to Bitforex Échange, and all 471,405 TRB were transferred to 4 OKX accounts and 2 Binance accounts on November 9 and 10. So far, all tokens of ETH chain, TRON chain and BTC chain have been transferred, 166 ETH, 46,905 USDT and 57,810 USDC are deposited on BSC, and 99,000 MATIC, 20,300 USDT and 1,700 USDC are deposited on POL.
Attached is the exchange address for depositing TRB:
7. Analysis of the flow of funds of stolen assets
Of the funds stolen in 2024, about $1.312 billion remained in the hackers address (including those transferred through cross-chain and dispersed to multiple addresses), accounting for 52.20% of the total stolen funds. Compared with last year, hackers this year are more inclined to use multiple cross-chain to launder money and disperse the stolen funds to many addresses instead of directly using mixers. The increase in addresses and the complexity of money laundering paths have undoubtedly increased the difficulty of investigation for project owners and regulators.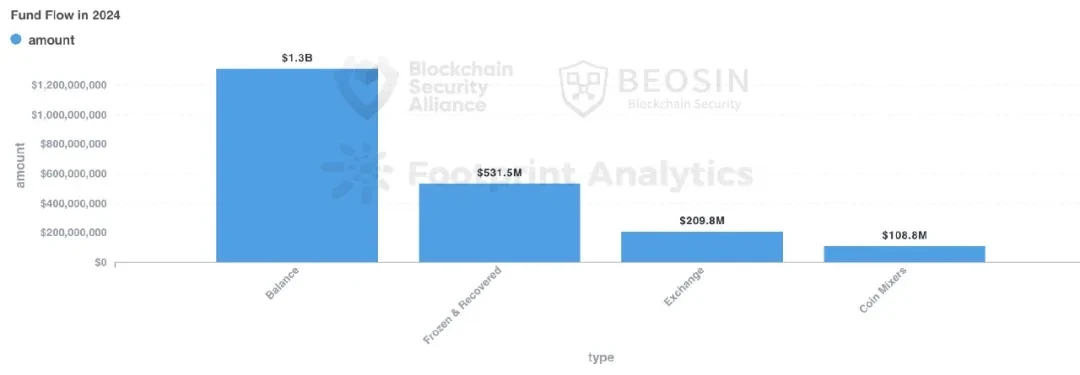
About $531 million of stolen funds were recovered, accounting for about 21.13%. In 2023, the recovered funds were about $295 million.
About $109 million of stolen funds were transferred to mixers throughout the year, accounting for about 4.34% of the total stolen funds. Since the US OFAC sanctioned Tornado Cash in August 2022, the amount of stolen funds transferred to Tornado Cash has dropped significantly.
8. Project audit situation analysis
Among the 131 attack incidents, the project parties of 42 incidents had not been audited, the project parties of 78 incidents had been audited, and the audit status of the project parties of 11 incidents could not be confirmed.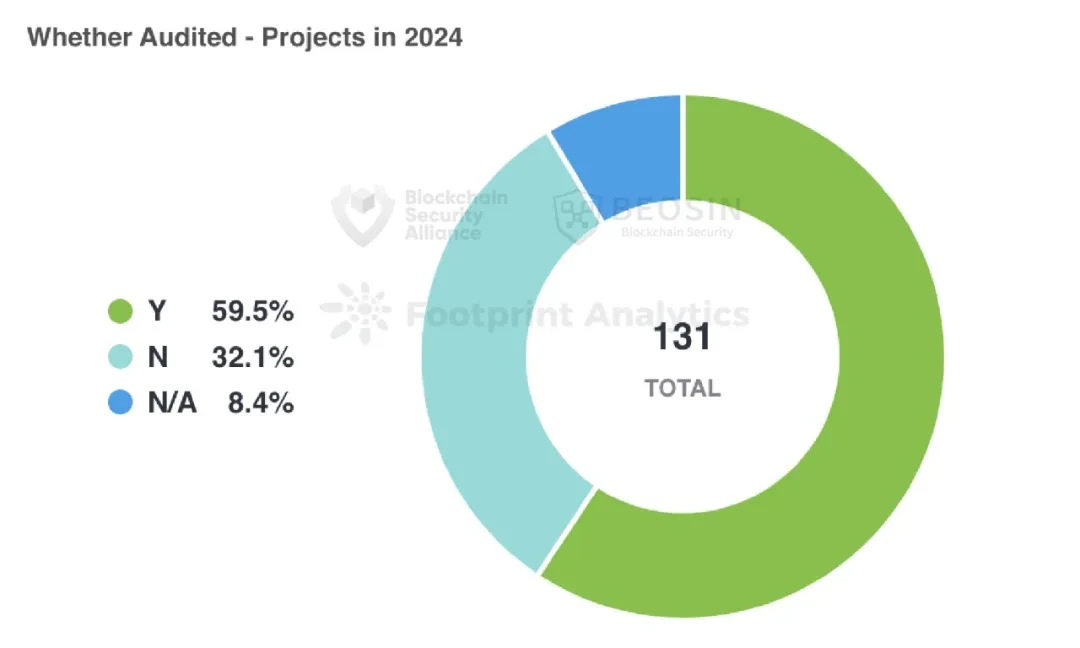
Among the 42 unaudited projects, 30 (about 71.43%) had contract vulnerabilities. This shows that unaudited projects are more likely to have potential security risks. In contrast, among the 78 audited projects, 49 (about 62.82%) had contract vulnerabilities. This shows that auditing can improve the security of projects to a certain extent.
However, due to the lack of complete regulatory standards in the Web3 market, the audit quality varies greatly, and the final results are far from expectations. In order to effectively protect asset security, it is recommended that projects must find a professional security company to conduct an audit before going online.
9. Rug Pull Analysis
In 2024, the Beosin Alert platform monitored 68 major Rug Pull events in the Web3 ecosystem, with a total amount involved of approximately US$148 million, a significant drop from US$388 million in 2023.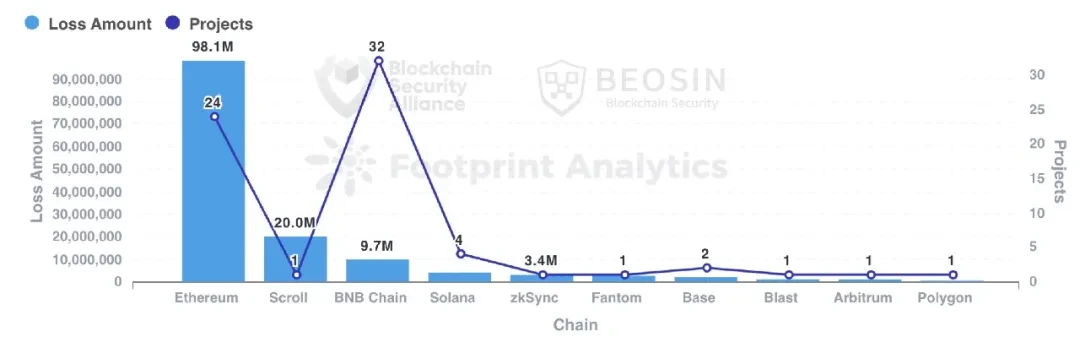
In terms of the amount, among the 68 Rug Pull incidents, there were 9 projects involving amounts of more than one million US dollars, namely Essence Finance (US$20 million), Shido Global (US$2.4 million), ETHTrustFund (US$2.2 million), Nexera (US$1.8 million), Grand Base (US$1.7 million), SAGA Jeton (US$1.6 million), OrdiZK (US$1.4 million), MangoFarmSOL (US$1.29 million) and RiskOnBlast (US$1.25 million), with a total loss of US$33.64 million, accounting for 22.73% of the loss amount of all Rug Pull incidents.
Rug Pulls on Ethereum and BNB Chain accounted for 82.35% of the total number, with 24 and 32 respectively. Scroll had one Rug Pull worth more than $20 million. Other public chains have had a small number of Rug Pulls, including Polygon, BASE, Solana, etc.
10. Summary of Web3 blockchain security situation in 2024
En 2024, the number of on-chain hacker attacks and project Rug Pull incidents has dropped significantly compared to 2023, but the amount of losses is still increasing, and phishing attacks are more rampant. The attack method with the highest loss is still private key leakage. The main reasons for this change include:
After the rampant hacker activities last year, the entire Web3 ecosystem has paid more attention to security this year. From project owners to security companies, efforts have been made in various aspects, such as real-time on-chain monitoring, more emphasis on security audits, and active learning from past contract vulnerability exploitation incidents, making it more difficult for hackers to steal funds through contract vulnerabilities than last year. However, project owners still need to strengthen their security awareness in terms of private key custody and project operation security.
With the integration of the crypto market and the traditional market, hackers are no longer limited to attacking DeFi, cross-chain bridges, exchanges, etc., but have turned to attacking payment platforms, gambling platforms, crypto brokers, infrastructure, password managers, development tools, MEV robots, TG robots and other targets.
In 2024-2025, the crypto market will enter a bull market, and on-chain funds will be active, which will attract more hacker attacks to a certain extent. In addition, the regulatory policies for crypto assets in various regions are gradually improving to combat various criminal activities using crypto assets. Under this trend, it is expected that hacker attacks will continue to be high in 2025, and global law enforcement agencies and regulatory authorities will still face severe challenges.
This article is sourced from the internet: Beosin: 2024 Web3 Blockchain Security Situation Annual Report
Related: Lumoz opens esMOZ airdrop query and announces airdrop rules
The Lumoz airdrop is officially here. Over the past two years, the community and Lumoz have gone through several important stages together: the Pre-Alpha testnet had 87,567 active participants, the Alpha testnet gained 286,179 followers, and the number of participants in the Quidditch testnet exceeded one million, demonstrating the communitys wide recognition and trust in Lumoz. These participations not only provide valuable feedback for Lumozs technical improvements, but also lay a solid foundation for the development of the ecosystem. This airdrop is not only a return to the support of users, but also an important testimony of Lumoz and the community moving towards the next stage together. Airdrop Rules Airdrop query portal: https://lumoz.org/airdrop The total amount of Lumoz Token is 10 billion. This airdropped token totals 10%, or 1 billion…







