Railgun: A privacy service worth $2 billion, a ZK tool to cover up money laundering on the chain
This article comes from: AnChain.AI
Compilé par Odaily Planet Daily ( @OdailyChina )

In January 2023, the FBI accused the North Korean hacker group Lazarus Group of using the privacy protocol Railgun to launder money, involving approximately 41,000 ETH (worth more than $60 million at the time), which was stolen from the Harmony Horizon Bridge attack in 2022. AnChain.AI is the main security company responding to the case. As of the time of writing, the total value of the ETH involved has exceeded $120 million.
Since its founding in 2022, Railgun has facilitated over $2 billion in cryptocurrency transactions, with WETH accounting for 76% of total volume. This volume of transactions highlights Railgun’s growing utility in on-chain privacy services.
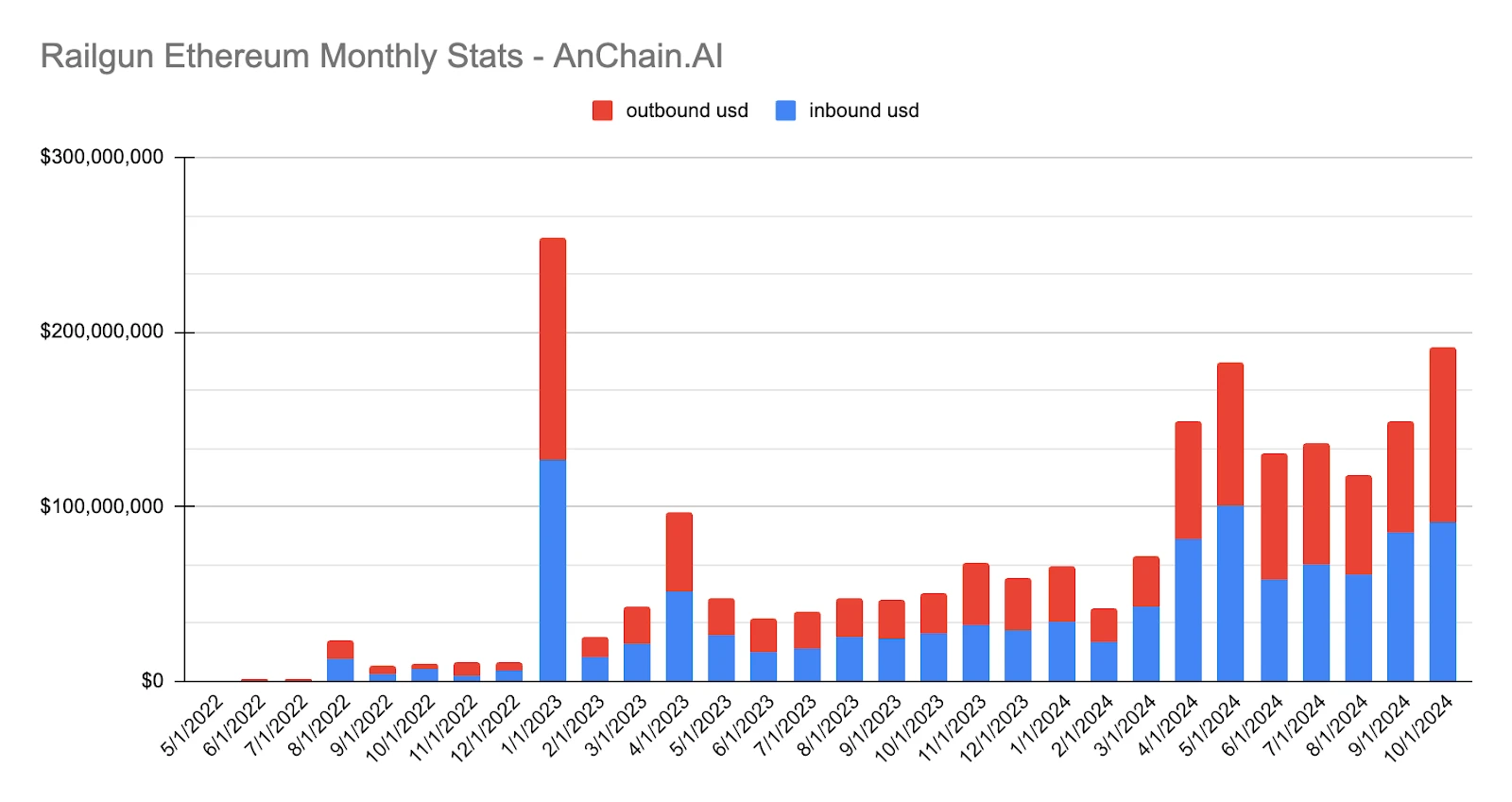
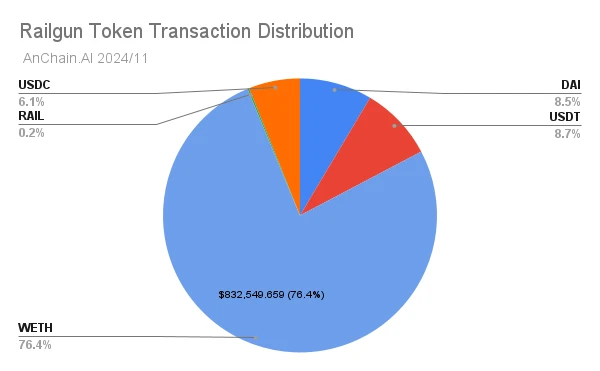
Railgun poses unique challenges to cryptocurrency-related investigations, especially in tracking illegal activity. This article will take a deep dive into Railgun’s underlying concepts, inner workings, innovative privacy mechanisms, and how this cutting-edge solution, trusted by regulators around the world, can more effectively combat money laundering.
What is Railgun?
Railgun uses smart contracts and zero-knowledge proof (ZKP) technology to replace traditional cryptocurrency mixing tools and become a new generation of privacy services. Unlike mixers that need to pool funds off-chain to obfuscate transactions, Railgun can directly integrate privacy functions into on-chain transactions to help users remain anonymous in DeFi activities.
Railgun runs on Ethereum and other EVM-compatible networks and can use zk-SNARKs to facilitate private on-chain transactions. zk-SNARKs allow users to prove the validity of transactions without revealing any sensitive information. This approach eliminates the need for third-party layers or bridges that often have privacy risks or operational complexity issues, enabling seamless integration with DeFi applications.
How does Railgun achieve transaction privacy? According to Railgun, it only takes 4 simple steps:
-
Create: Set up your non-custodial RAILGUN wallet using a private 0 zk address.
-
Shield: Transfer any ERC-20 token or NFT to this 0 zk address to achieve shielding;
-
Transaction: Once blocked, tokens, balances, and transactions are encrypted.
-
Use: Transfer assets between 0 zk addresses and use DeFi anonymously.
However, while these steps may seem simple, the challenges posed by Railgun become more apparent when we look more closely at its inner workings.
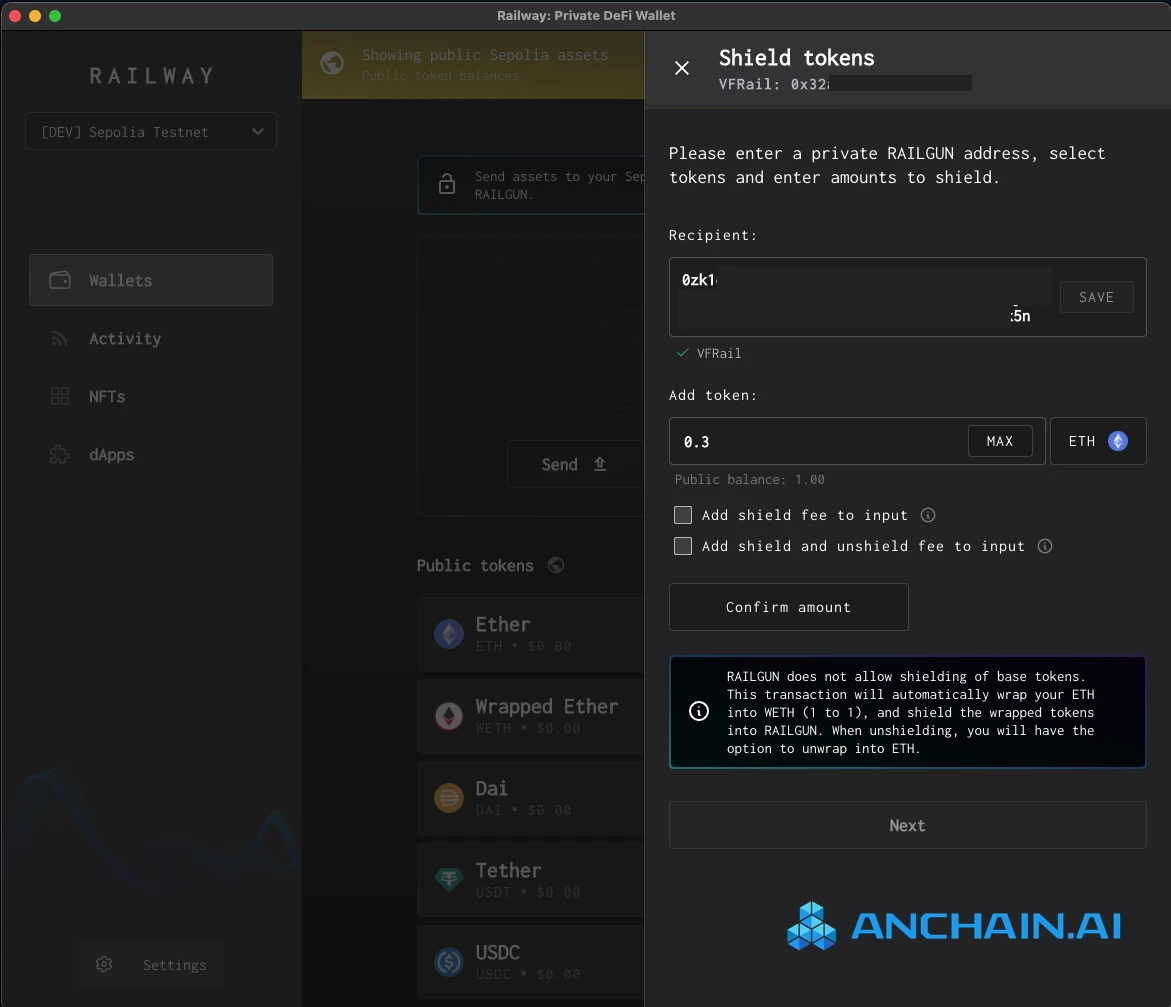
What are zk-SNARKs?
Railgun is essentially a smart contract DApp that uses zero-knowledge proofs, specifically zk-SNARKs, to ensure transaction privacy.
Zero-knowledge proofs are a cryptographic technique that allows one party (the prover) to convince another party (the verifier) that they know some form of information without revealing the actual information. zk-SNARKs (Zero-Knowledge Succinct Non-Interactive Arguments of Knowledge) are a specific form of zero-knowledge proofs that emphasize “non-interactive,” meaning that no back-and-forth communication is required between the prover and the verifier.
In Railgun’s privacy system, zk-SNARKs allow smart contracts to act as validators. When a user wants to make a transaction, zk-SNARKs allow the user to prove that their actions (i.e. transferring tokens or interacting with a DeFi protocol) followed the rules without revealing any sensitive details.
Railguns technical process involves several key components:
-
Trusted setup: Use elliptic curves to generate the cryptographic parameters required for proof creation and verification to establish a public parameter system. These parameters will be used to ensure that subsequent proofs can be verified.
-
Circuits: In the Railgun protocol, witnesses (private data, such as a users token balance or transactions) are used in cryptographic circuits. The circuit défines some conditions that must be met (such as a valid transaction amount or sufficient balance). Based on the witnesses and the circuit, the prover can calculate a solution (proof).
-
Proof Generation: Generate a concise, cryptographically valid proof that a user knows a “proof” that satisfies the “circuit” conditions, without revealing the “proof” itself.
-
Verification: Submit the proof to the network and verify it using the public parameters from the trusted setup step. The verification process can be computationally efficient, allowing for real-time verification on-chain.
The magic of zk-SNARKs lies in their efficiency – they can generate smaller, easier-to-verify proofs, a feature that is well suited for blockchains with strong demands for speed and privacy. This allows the Railgun system to use cryptographic circuits to handle different types of transactions, each of which can be defined by a specific number of inputs (UTXO) and outputs. These circuits can manage different transactions, from multi-sends to privacy NFT shielding. Railgun has 54 different circuits that can handle a variety of transaction combinations, and the system automatically routes transactions to optimize gas and save costs. This flexible design also allows Railgun to support a variety of token standards, including ERC-20, ERC-721, and ERC-1155, enabling Railgun to efficiently handle a variety of transaction types.
Unveiling the Railgun Smart Contract
The role of smart contracts in cryptocurrency tracking
The rise of smart contracts and Railgun has fundamentally changed the way cryptocurrencies are tracked. There are two main challenges.
-
Technical Complexity: Railgun’s privacy design and ZKP technology obscure transaction details, making it difficult to link deposits and withdrawals without specialized tools.
-
Legal ambiguity: The inherent privacy nature of the protocol raises questions about liability, especially when features intended to protect user privacy are exploited by bad actors.
For cryptocurrency investigators, understanding smart contract mechanics is no longer a nice-to-have, but an essential skill.
Railgun main contract address on Ethereum mainnet
Railgun operates through a series of dedicated smart contract networks. It mainly has two smart contracts on the Ethereum mainnet.
Railgun relay contract:
-
Address: 0xfa7093cdd9ee6932b4eb2c9e1cde7ce00b1fa4b9
-
Description: Facilitates the relay of transactions within the Railgun system, ensuring that users interactions remain private and secure.
Railgun Smart Wallet Contract:
-
Address: 0xc0BEF2D373A1EfaDE8B952f33c1370E486f209Cc
-
Description: Manages the core functionality of the Railgun privacy system, including the shielding and unshielding of assets, and how private transactions are processed.
It’s important to note that while these addresses are specific to Ethereum, Railgun also operates on other networks like BSC, Polygon, and Arbitrum, each with their own unique contract addresses.
Analyzing Railguns relay contract
An analysis of Railgun’s relay contract using AnChain.AI’s SCREEN smart contract evaluation platform found that the contract was broadly classified as a “Pausable Upgradeable Proxy.” This architecture allows for upgrades while maintaining operational control, providing flexibility and security.
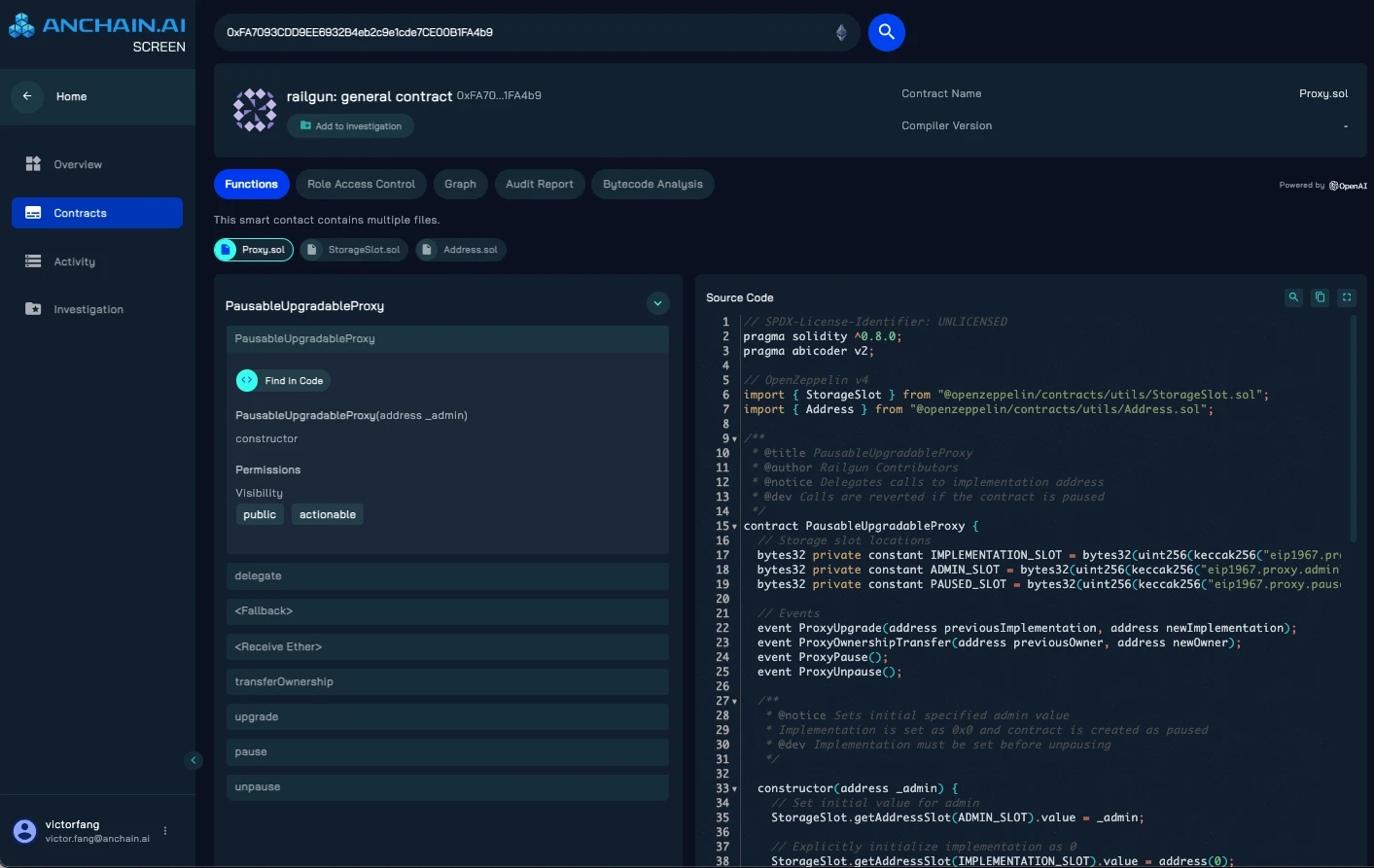
We can better understand what this design means in the real world through a case study involving a complex money laundering operation.
Case Study: Harmony Bridge Attack and the Effectiveness of Railgun
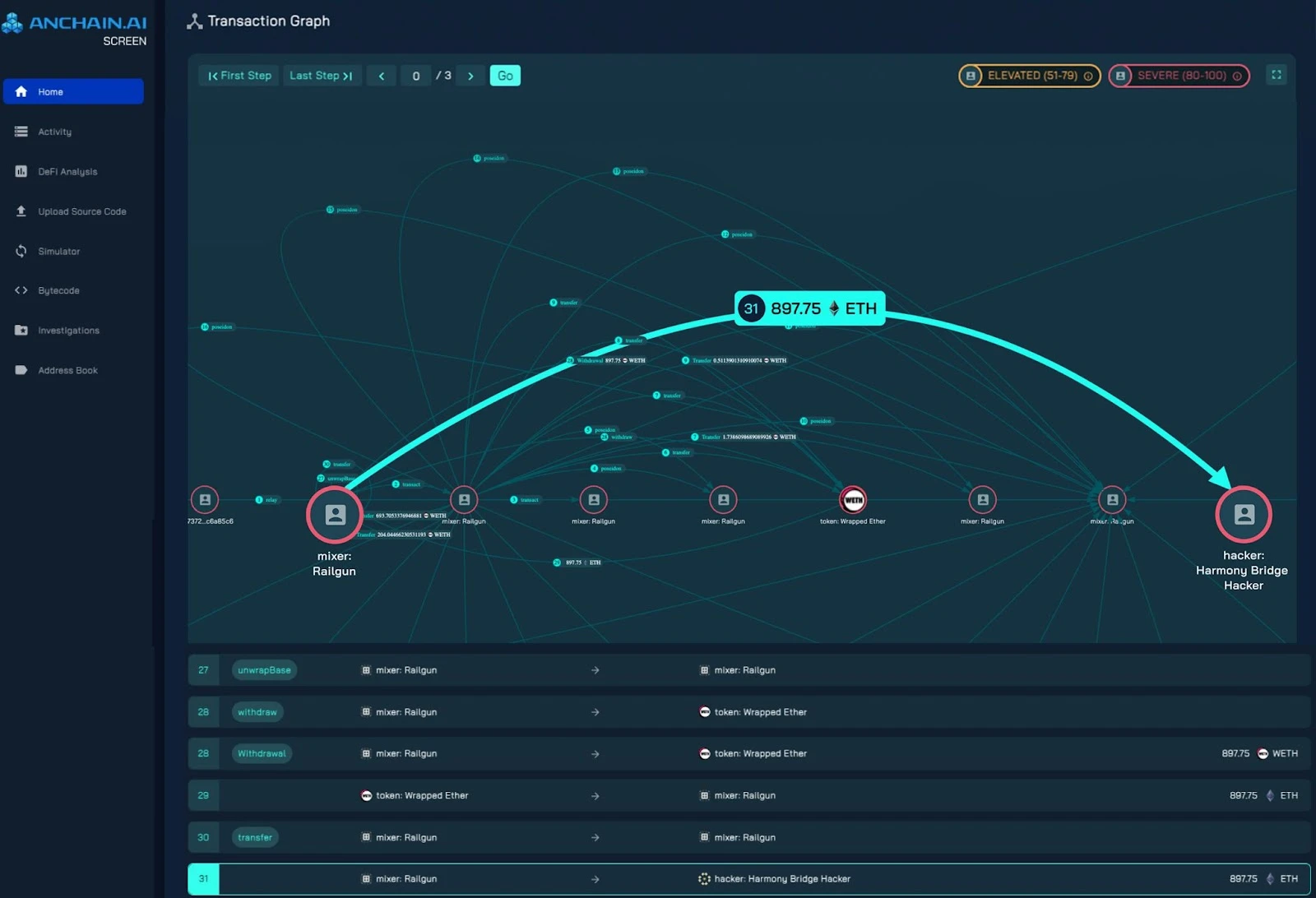
In January 2023, an address associated with the infamous Harmony Bridge hack laundered 897 ETH (about $2.7 million) through Railgun. While this transaction (as highlighted above) appears simple, it was supported by 31 different smart contract events, many of which escaped detection by traditional investigative tools. This complex transfer pattern highlights the complexity of Railguns privacy mechanism and its ability to conceal the true flow of funds.
Uncovering the intricacies of insider trading
Traditional blockchain explorers were unable to capture the details of Railgun’s private transactions. To address this challenge, SCREEN’s advanced transaction graphs and simulation capabilities helped investigators break down Railgun’s internal processes, revealing hidden flows and patterns of funds.
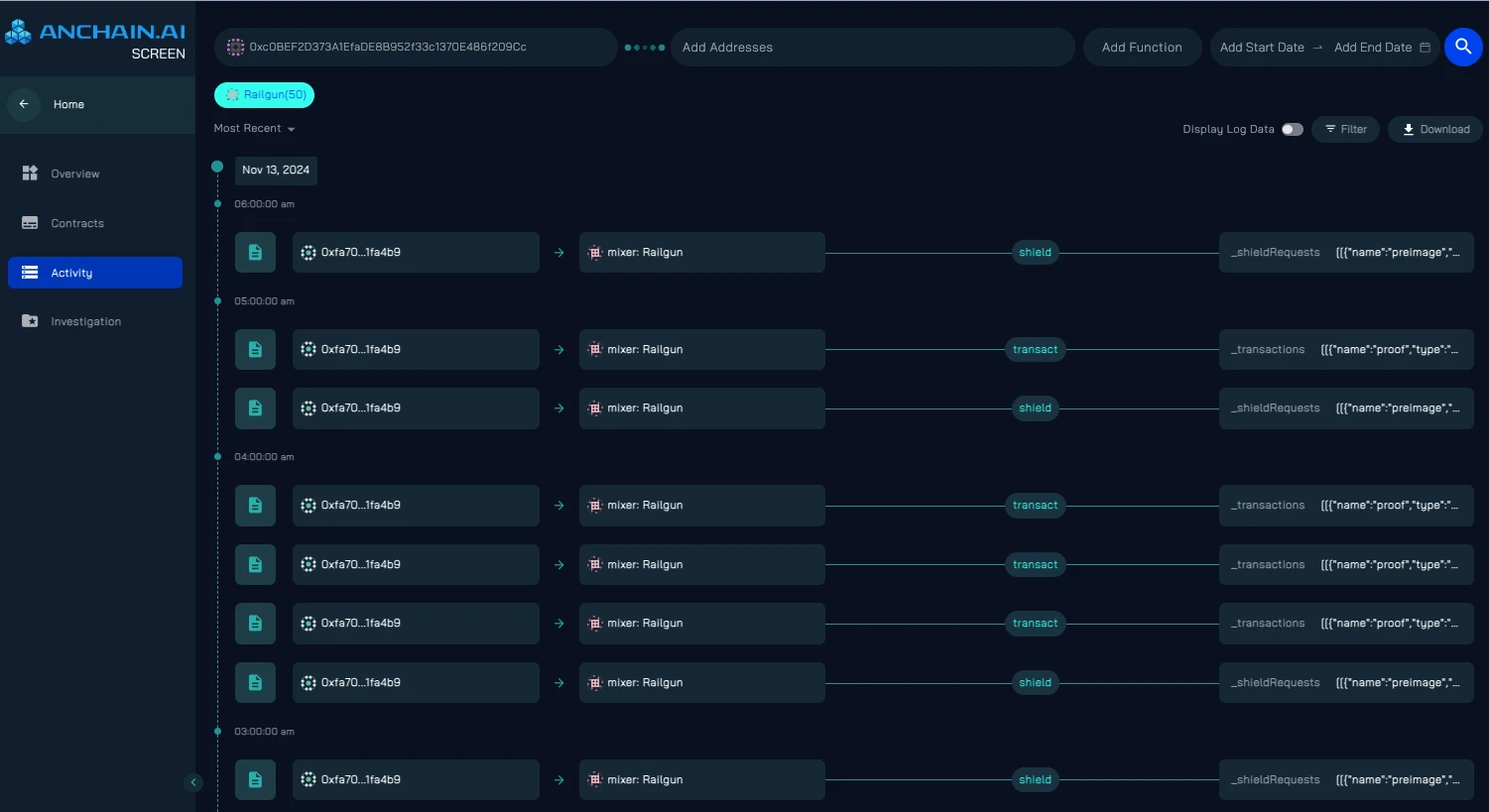
As shown above, the internal transaction timeline in SCREEN can reveal complex patterns of fund movement, including transfers back and forth — part of Railgun’s privacy system.
New Challenges in Cryptocurrency Investigations
Railgun’s privacy design and use of ZKP technology creates a huge barrier to cryptocurrency investigations, but it is not impossible to overcome.
Successful investigations rely heavily on contextual factors such as external interactions with exchanges, activity patterns for deposits and withdrawals, and potential associations identified through behavioral or cluster analysis.
Investigating exploratory solutions for Railgun transactions
Based on extensive investigative experience, AnChain.AI has developed the following exploratory solutions for probabilistic tracing and analysis of transactions conducted through Railgun. Different methods target different aspects of Railguns functionality to infer potential connections between deposit and withdrawal events.
Deposit and withdrawal monitoring plan:
-
Focus: Watch the money coming into (blocking) and leaving (unblocking) Railgun;
-
Method: Track the public addresses that deposit funds to Railgun and monitor their withdrawal transactions to see where the funds reappear on the public address;
-
Limitations: Cannot reveal transactions within Railgun, but provides potential endpoints.
Time monitoring program:
-
Focus: Analyze the timing of deposits and withdrawals;
-
Methods: Look for temporal relationships between large or independent deposit and withdrawal events, which may indicate the existence of a potential relationship;
-
Limitations: There is a certain degree of probability, and the monitoring effect is best for isolated time events, but false alarms may also occur;
Off-chain association scheme:
-
Focus: Correlate on-chain Railgun activity with off-chain events;
-
Methodology: Compare Railgun transactions to external factors such as exchange activity or known social interactions on the blockchain.
-
Limitations: Depends on the availability and quality of off-chain data.
Transaction pattern analysis plan:
-
Focus: Identify relevant addresses through transaction patterns;
-
Methodology: Use clustering algorithms to find behavioral similarities in Railgun interaction addresses to identify an entity or group.
-
Limitations: Private transactions may reduce the accuracy of analysis, and transaction patterns are usually complex and ambiguous.
Governance Interaction Program:
-
Focus: Check Railgun governance or public wallet interactions;
-
Methodology: Analyze known governance or public addresses that may be associated with Railgun and observe their transaction behavior;
-
Limitation: Only applies if Railgun is using a known governance address.
end
The challenges posed by Railgun raise a common problem when conducting cryptocurrency investigations today — how do investigators begin to track illicit funds when widespread privacy protocols hinder their most commonly used tools?
In today’s digital asset ecosystem, understanding smart contracts is more than just a suggestion, it’s a necessity. Protocols like Railgun challenge traditional methods of blockchain tracing, highlighting the need for continued innovation in forensic techniques and investigative strategies.
AnChain.AI is committed to solving this problem through technology and continues to provide leading global regulators with technology that can penetrate smart contracts, redefining the way cryptocurrencies are investigated.
This article is sourced from the internet: Railgun: A privacy service worth $2 billion, a ZK tool to cover up money laundering on the chain
Recently, the MEME coin GOAT on Solana can be said to be the biggest wealth code, with a market value of over $400 million in just one week. It also allowed many smart money to gain more than a thousand times of profit. Behind the story of getting rich quickly, how did these smart money operate? How did they achieve more than a thousand times of profit? PANews conducted an in-depth analysis of the six smart money addresses that gained substantial profits on GOAT. In the analysis, PANews mainly focuses on the time period in which these smart money buys, what is the daily buying operation strategy, how long is the position held, and when is the principal sold. 2PYWK : Pump.fun curve pusher accidentally captured GOAT 2PYWKE6EJ8pWeX11ahhvrY1k947JCwuwZpV4eihiJJNS (hereinafter referred…







