SlowMist : Du vieux vin dans de nouvelles bouteilles, analyse de l'arnaque du robot d'arbitrage MEV
Original author: Liz, Slow Mist
arrière-plan
Earlier this year, SlowMist founder Cos warned users on X about the arbitrage MEV robot scam. Now hacker gangs are also following the trend, and the name of the scam has changed from Simple and easy-to-use Uniswap arbitrage MEV robot to ChatGPT arbitrage MEV robot: How to use the slippage robot to earn $2,000 a day completely passively. The SlowMist security team has noticed that the number of users who have been harmed by this type of scam has increased recently. Therefore, this article will explain the scam routine and analyze the scammers fund transfer model to help users avoid falling into this type of scam.
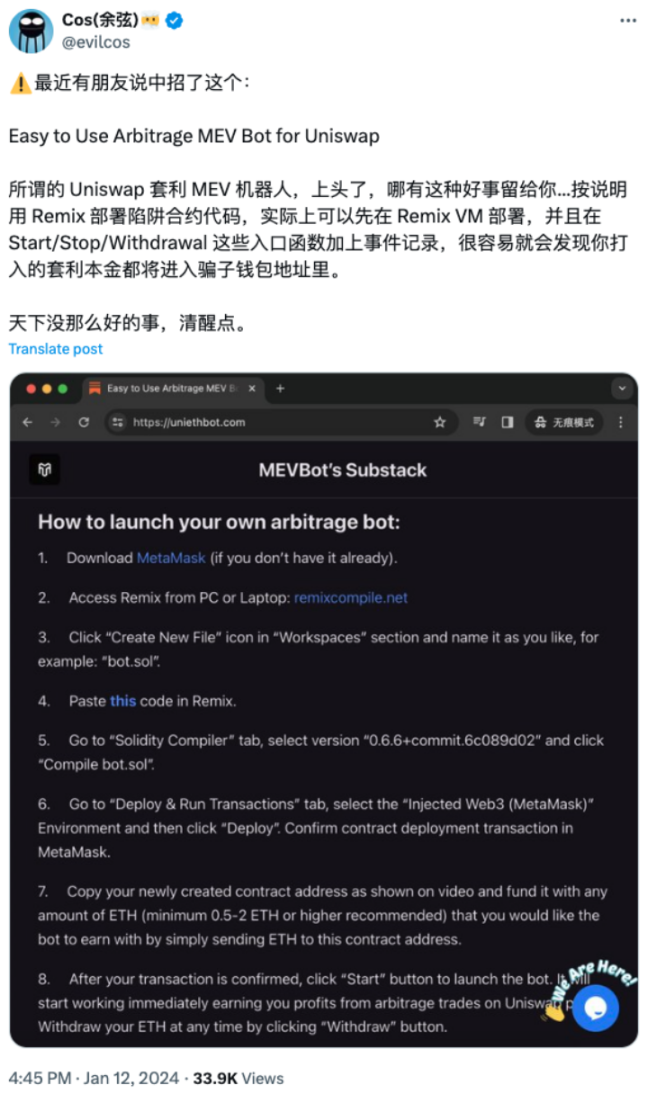
( https://x.com/evilcos/status/1745728599171457120 )
Arbitrage is cheated
AI has become a tool for more and more people to improve their productivity. Scammers are well aware of this and label their scams with ChatGPT, which not only attracts attention but also makes them appear reliable and advanced. However, ChatGPT only appeared briefly in the scammers video tutorials: the scammers claimed that the code of the arbitrage robot was generated by him using ChatGPT, which also dispelled some users suspicion that the code was malicious.
( https://www.youtube.com/watch?v=Z32hH3eLK-c )
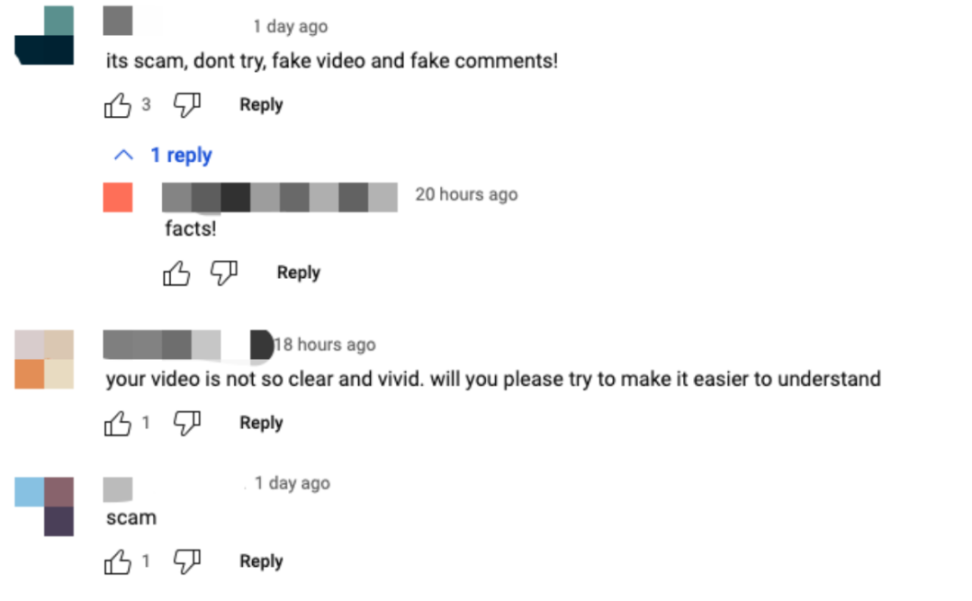
In fact, if you look closely at the videos made by the scammers on YouTube, you will find that the audio and video are not synchronized, the historical videos are just for show, and the account is most likely bought. All signs show that this YouTuber is not trustworthy. Although the comment area is almost dominated by praise and words of thanks, if you scroll down, you can find some reminders and warnings from victims.
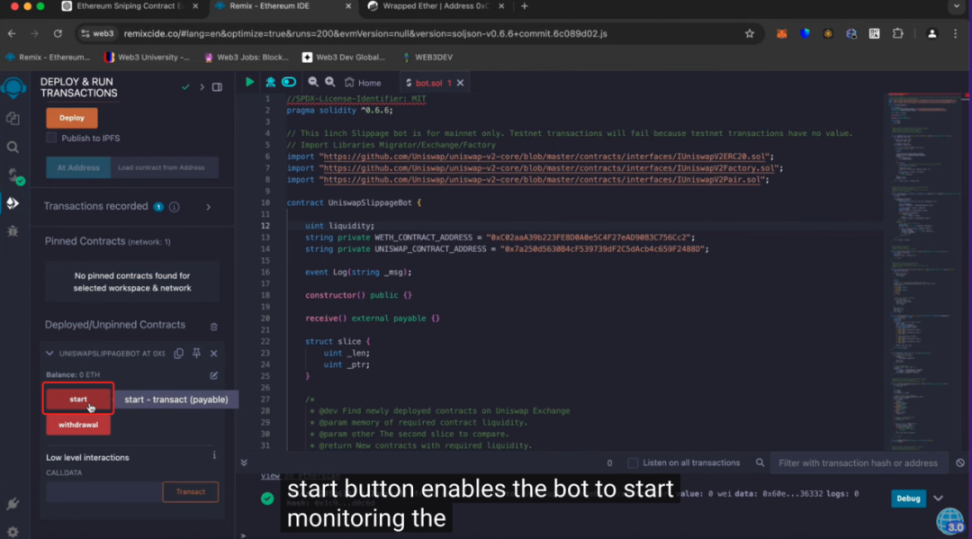
The scammer claimed that his robot could monitor new tokens and large price changes on Ethereum, looking for arbitrage opportunities, and users only needed to wait for the money to be collected. Users first had to have a MetaMask wallet, and then open the Remix link (fake Remix) provided in the tutorial.
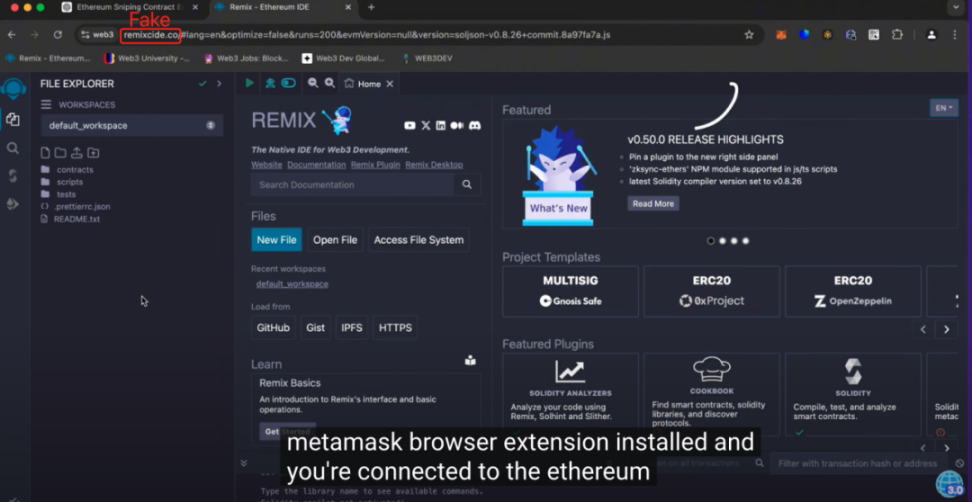
Next, the user needs to paste the code provided by the scammer, compile the robot and deploy the smart contract. At this point, the scammer said that the user must provide initial funds for the contract, and the more ETH deposited into the contract, the more profit can be obtained. After the user follows the above process and clicks start, the money disappears, and the arbitrage principal deposited goes to the scammers wallet address because the code has a backdoor.
We take the following fraud incident reported by the Web3 anti-fraud platform Scam Sniffer as an example to analyze the fund transfer pattern of such scammers.
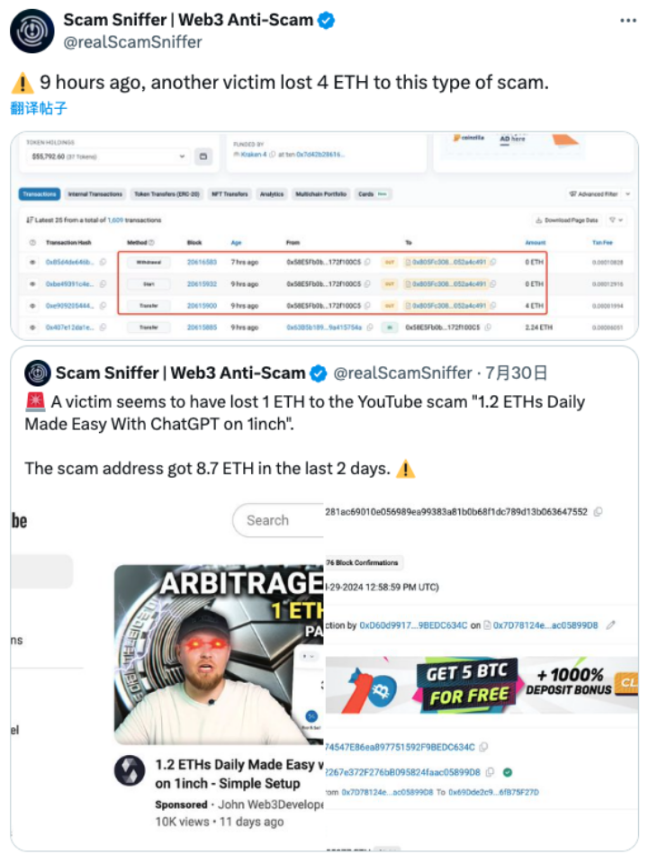
( https://x.com/realScamSniffer/status/1828364436241031669 )
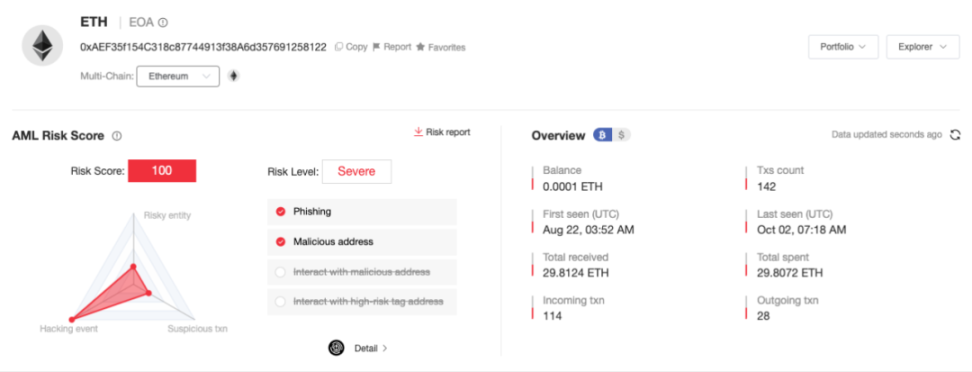
Using the on-chain tracking and anti-money laundering platform MistTrack to query the scammer鈥檚 address (0xAEF35f154C318c87744913f38A6d357691258122), we can see that from the end of August to now, this address alone has made a profit of about 30 ETH, with more than 100 victims.
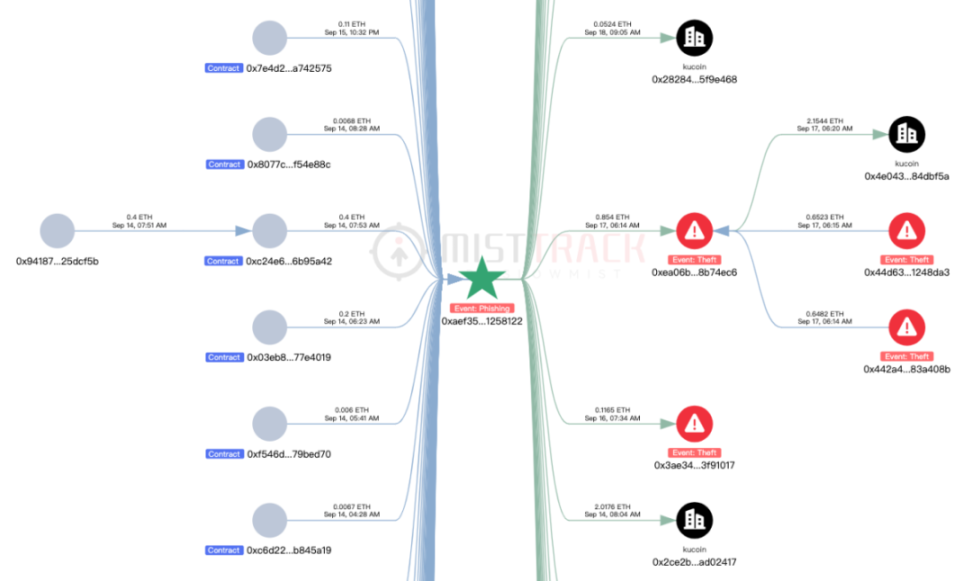
The funds transfer mode of this address is single, all of which are transferred by the victims according to the above scam process, and then ETH is stolen by the scammers. The withdrawal mode is directly transferred to the exchange; or transferred to the address for temporary storage of funds (such as: 0xea06b983e144432919779b236ba28ece28b74ec6), and then transferred to the exchange.
0x442a4960c783affe2b6d9884f32d7cf2683a408b and 0x44d63ce270637553f89f3c2706869d98d1248da3 in the figure below are also the addresses used by scammers to directly collect funds from victims. These two addresses were created at the end of August and have stolen about 20 ETH so far, with about 93 victims.
Since the scammers adopt a model of casting a wide net and accumulating small profits, although there are many victims, the losses are relatively small, and it is not realistic to spend energy to pursue them. Therefore, these scammers can get away with it for a long time, and they can continue similar fraudulent activities by changing the scam skin. Remix has reminded users on its website to be aware of such scams. In the comment section of the scam analysis article published on Medium, it was found that victims have posted messages about being deceived from two years ago to recently, and many users have provided links to related scam videos to remind everyone to pay attention to safety, which shows the extent of the prevalence of such scams.
Résumer
The SlowMist security team reminds users not to click on unknown links or run unknown codes. Since the scammers claim that the code is generated by ChatGPT, we can at least send the code to ChatGPT, Claude and other tools to check whether it contains malicious behavior. Many users originally just wanted to earn passive income and were willing to pay the principal, but after following the scammers operations, they didnt expect that the principal would be gone in the end. Instead, the scammers relied on these tutorials to fool victims into transferring money to his wallet to achieve passive income. Therefore, users are requested to remain vigilant and confirm whether it is a pie in the sky or a trap before operation to avoid financial loss.
This article is sourced from the internet: SlowMist: Old wine in new bottles, analysis of the arbitrage MEV robot scam
Guest of this episode: Raymond, Partner of Mossfire Capital FC: What is the reason for inviting Raymond today? We actually wrote three keywords on Twitter: the first is the regular army, with 8 years of investment banking experience and a long time in traditional finance; the second is that I have handled APPs with tens of millions of DAU, which I think is actually quite difficult; the third is that I think you have a set of methodology. In fact, I haven鈥檛 written one more. I am quite curious about your personality, because I think we are quite similar, and we should both be more sensitive. I think it is not conducive to trading. In fact, I will have a discussion about personality in each issue, because I think everyone鈥檚…







