Explicación detallada del upstream y downstream de la industria del cifrado: ¿Cuál es el valor del front-en downstream?
Autor original: Richard Yuen
Traducción original: TechFlow
The downstream front-end application layer will become one of the largest components of the on-chain economy
Many are calling for more applications, but for the wrong reasons — this is not about VCs trying to drive up their infrastructure assets, or looking for the next 100x speculative story.
Here are some ideas.
1. Value chain – upstream, midstream and downstream
To understand how the crypto/blockchain space might evolve, we can draw on the evolution of mature industries such as the internet.
In a mature Internet industry, its value chain can be divided into upstream, midstream and downstream.
-
Upstream: The underlying technologies and infrastructure that make the Internet possible; including hardware, connectivity, networks, core software and protocols, etc.
-
Midstream: Platforms built on underlying infrastructure; including data storage, cloud computing, hosting services, search engines, etc.
-
Downstream: Platforms supported by midstream infrastructure that interact with end users and consumers; including applications such as social media, streaming, e-commerce, blogs, forums, etc.

The upstream of the value chain involves the development of basic technologies, including core protocols and software that midstream platforms rely on. Midstream platforms serve as a key link to ensure compatibility, optimization and seamless integration between upstream infrastructure and technology providers and downstream consumer-facing platforms. Downstream platforms are the main interface and delivery channel for end users, who can access and use the products and services provided by these platforms.
The infrastructure provided by upstream and midstream platforms enables downstream applications to provide diversified products and unlimited iterations to meet the needs of end users.
Upstream and midstream infrastructure typically have strong technological moats, homogeneous products, limited differentiation, and are often commoditized, but still generate high profits (such as Amazon AWS), and some have become public products.
Downstream applications have lower technology moats, but differentiated product offerings, clear value propositions to attract users, and a focus on retaining users and creating strong network effects as moats. Many applications will expand horizontally to provide a wider range of products, and some will even vertically integrate the entire value chain as they scale.
-
Upstream and midstream platforms: B2B
-
Downstream applications: B2C
As the blockchain/crypto industry develops, I expect the value chain to eventually form the following three main streams:
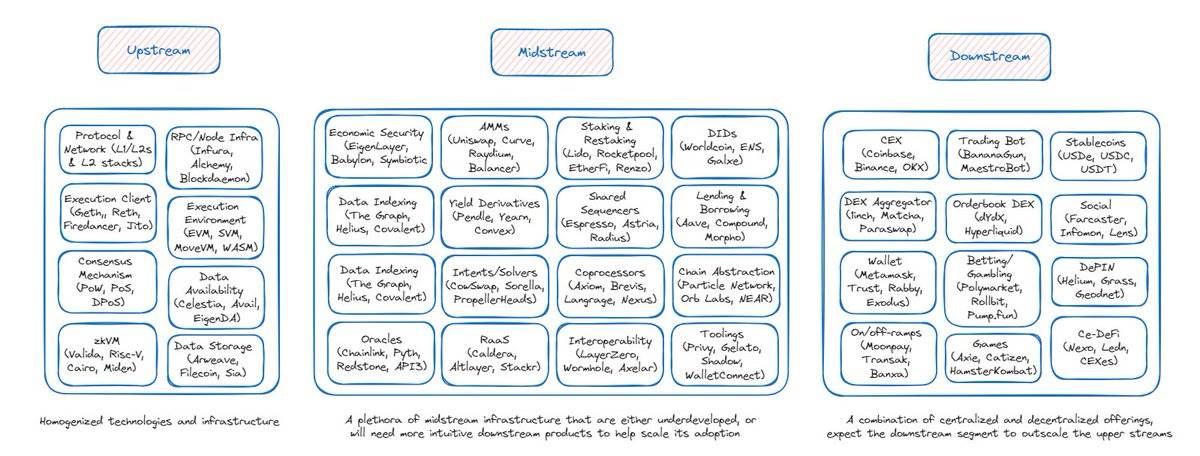
-
Upstream : The foundational technologies and infrastructure that enable blockchain adoption; including protocols and networks (L1/L2), RPC/node infrastructure, execution and consensus clients, execution environment, consensus mechanisms, data storage, zkVM, data availability, etc.
-
Midstream : Platforms built on the underlying blockchain infrastructure; including economic security, automated market makers (AMMs), yield derivatives, intent solvers, oracles, RaaS, staking and re-staking, shared sequencers, interoperability, decentralized identity (DID), lending markets, chain abstraction, data indexing, etc.
-
Downstream : Applications supported by upstream infrastructure; including centralized exchanges (CEX), decentralized exchange aggregators, order book decentralized exchanges, trading robots, games, centralized and decentralized finance (Ce-DeFi), entry and exit services, wallets, decentralized physical infrastructure (DePIN), social, gambling/betting, stablecoins, etc.
2. Key observations and thoughts:
Upstream crypto infrastructure is becoming homogenous. Infrastructure projects are almost all built on the same standardized mechanisms – for example, proof of stake (PoS), EVM compatibility, etc. Although some projects may offer a certain degree of specialization or unique features, the features provided by the overall upstream participants are generally comparable.
The homogeneous nature of upstream products will eventually lead to price competition, with projects striving to differentiate themselves in pricing, performance, and developer relationship management (e.g., commoditization of block space). Creating branding and network effects will become more important than ever for upstream players to remain relevant in the competition.
It seems a bit strange that upstream infrastructure (such as L1/L2) should take on most of the general customer acquisition work, because their business model is mainly B2B. It seems very inefficient to indiscriminately airdrop billions of dollars to users of various downstream applications. Imagine Amazon AWS spending billions of dollars to help its downstream customers (such as ordinary traders on Robinhood or viewers on Netflix) with user onboarding – it is difficult to formulate the right user onboarding and retention incentive strategy due to unfamiliarity with the product, user behavior/segmentation, engagement metrics, etc. Therefore, billions of dollars are ultimately lost to attract airdrop farmers and hired users who will churn after the incentive ends.
Midstream crypto infrastructure could face the same fate, becoming homogenized and ultimately commoditized.
DeFi applications like Uniswap, Aave, and Pendle — I intentionally categorize them as midstream because there is limited differentiation between players in the same sub-sector, and they will need more intuitive downstream applications (e.g., front-end aggregators/CeDeFi platforms) to provide better UX and scale. The UX they currently provide tends to be targeted only at crypto natives (let’s be honest: setting up and funding a hot wallet, navigating to a DeFi application, choosing the right product/trading pair, choosing the right chain, confirming transactions, etc. is really a nightmare for most non-native users).
A lot of midstream infrastructure is still in the iteration phase (especially intent layer/solver networks, coprocessors, shared sequencing, chain abstraction) – as the technology matures, this area will be able to provide better capabilities for downstream applications – faster, cheaper, more precise execution and calculation, better interoperability, smoother user experience…
The downstream crypto application space is still a long way from mature status. I expect the downstream space to be larger than the upstream space – similar to the market structure in mature industries.
There are two main categories of downstream applications: centralized and decentralized. Centralized applications (CEX, CeDeFi platforms, entry and exit services) provide a more intuitive UI/UX, similar to Web2 platforms, with less user onboarding friction, usually compliant with regulatory requirements, and most have found some kind of product market fit. Decentralized applications leverage and aggregate upstream infrastructure as their support while providing a smoother front-end interface to reduce user friction. This area will be at the forefront of accelerating the mass adoption of blockchain technology and cryptocurrencies.
Vertical Integration – A trend is observed where downstream applications that have found product-market fit begin to vertically integrate across the value chain and expand horizontally to provide a wider range of services. This phenomenon is not uncommon – Amazon online bookstore (downstream) built its own logistics/fulfillment network (midstream) and cloud-based infrastructure (upstream) to support its e-commerce and other internal operations, and expanded its e-commerce products horizontally to every general category. In the crypto space – consider centralized exchanges like Binance and Coinbase (downstream) launching BNB Chain and Base (upstream), incentivizing the construction of midstream infrastructure on top of it, and expanding horizontally to provide a wider range of products – wallets, staking services, entry and exit services, custody, etc.; or consider the game Axie Infinity (downstream) launching Ronin Chain (upstream), and all midstream applications/infrastructure – Ronin wallet, Katana (DEX), Mavis Market (NFT Market), Ronin Launch Platform, Mavis ID (decentralized identity), Ronin RPC, etc.
I expect the burden of customer acquisition to shift from upstream infrastructure back to downstream applications. This will be catalyzed by:
1) The L1/L2 ecosystem directly airdrops to applications, enabling them to design incentive plans based on their respective roadmaps, product designs, and business models;
2) Venture capital firms, L1/L2 and general capital re-evaluate downstream applications and fund growth in this area.
3. Applications in the middle and lower reaches of the value chain will accumulate the most value
About value creation: Upstream infrastructure creates value by pioneering technological innovation and improving the performance, efficiency and reliability of basic systems. Midstream platforms create value by packaging upstream technology products into applications, platforms or ecosystems that are easy for developers to use to meet specific market needs. Downstream participants rely on midstream and upstream infrastructure to create value by improving the availability, accessibility and personalization of products.
Current status: Upstream and midstream infrastructure have gone through 2-3 technology iteration cycles, and the value created by many technological advances has been reflected in the market value growth of these areas. Innovation has stabilized and technology has become homogenized. Downstream applications may experience unprecedented growth in the upcoming cycle as they begin to create value by leveraging increasingly mature upstream infrastructure.
In mature industries, downstream platforms and applications usually receive the most user attention because they are the only interface for users to interact. Users often do not know (or care about) the backend technology stacks built by these downstream applications. What users care most about is the user experience provided by these applications.
With strong network effects (user base) and differentiated product offerings, downstream platforms are able to command higher pricing power and receive higher valuations.
Take ByteDance (TikToks parent company) as an example. It has more than 50 million daily active users, generates $120 billion in revenue, and is valued at $268 billion; while the CDN network it relies on, Akamai, only generates $3.8 billion in revenue and has a transaction value of $16 billion in 2023; the same applies to companies such as Meta, Netflix, and Google.
Value flows from downstream applications that are monetized through a large network of paying customers to midstream and ultimately to upstream players. The growth of downstream applications will promote the growth of the upstream technologies they rely on, forming a symbiotic relationship.
We have seen that crypto applications’ fee income exceeds upstream infrastructure – midstream (Raydium, Uniswap, PancakeSwap, Aave, Lido, Jito); downstream (Ethena, Pump). Upstream infrastructure like Avalanche, Near, Polygon are no longer in the spotlight, generating only $10,000 to $100,000 in fees per day.
Take Uniswap and Ethereum as an example: a user trades $100,000 on Uniswap and pays $1 in network transaction fees to Ethereum, but Uniswap earns over $300 from transaction fees and MEV profits – its obvious which layer accumulates more value.
4. Popularization of profit maximization
Downstream applications on L1/L2 are affected by the gas fees of user activities (L1 security fees and/or L2 execution fees) on the one hand, and by the upstream L1/L2 block builders utilizing MEV, leaving a large amount of funds unused.
Intuitively, in order to maximize revenue sources, many downstream applications have begun to explore the possibility of regaining sovereignty over revenue generation.
It is expected that downstream applications will further privatize their order flows, build their own private memory pools through vertical integration, and even become block builders. Some may launch their own application chains to capture more value.
Take the Banana Gun TG bot for example – it is expected to pay over $100M in priority fees and miner tips to Ethereum builders and validators. Already 98% of order flow goes through the private mempool. I wouldnt be surprised if Banana Gun expands vertically into block building to capture more value.
Some choose to build their own application chains to achieve a more optimized blockchain architecture for specific applications (throughput requirements, consensus algorithms, application-specific data structures, custom gas fees and economic incentives, sovereignty, etc.), enabling them to scale more efficiently than general-purpose blockchains. Value capture will also be concentrated on the application chain, rather than revenue sharing with the base layer blockchain.
It is expected that as solver networks (Fastlane Atlas, Semantic Layer, Uniswap V4 hooks), interoperability and chain abstraction infrastructure, as well as RaaS and rollup stacks (OP Stack, ZK Stack, Arbitrum Orbit, etc.) mature and become more popular, the profitability of applications will grow, enabling better value capture in the future.
5. “Front-end flip” meta-concept
Downstream front-end applications that provide a smooth user experience will lead the entry of millions of non-crypto users. Midstream applications such as Curve, Aave and upstream infrastructure will become the backbone of execution and settlement.
Front-end applications that I am particularly optimistic about include: trading bots and wallet-built exchanges that provide a chain-abstracted trading experience that enable optimized trade execution and low fees; order books and centralized limit orders (CLOBs) that provide a Web2-like trading experience , ensuring fast and low-cost transactions; payment super-apps with on- and off-line solutions that provide a seamless P2P Venmo-like experience for stablecoin transfers; and social applications and games that make rational use of financialization, asset ownership, and AI to create an experience comparable to Web2 applications.
Front-end flipping is happening.
For example, downstream frontends like Jupiter and 1inch charge fees comparable to Uniswap and PancakeSwap.
Additionally, front-end applications such as TG bots, wallet exchanges, and aggregators already generate approximately 50% of Ethereum transactions.
Downstream front-ends are taking market share from midstream back-end applications. As these front-ends become the de facto standard for interacting with DeFi, the market share of back-end applications is expected to decline further.
The rollover of fat front-end applications is inevitable.
This article is sourced from the internet: Detailed explanation of the upstream and downstream of the encryption industry: What is the value of downstream front-end applications?
Related: Selling V3 trading software and being hacked, what is dYdX doing?
Original author: Grapefruit, ChainCatcher Original editor: Marco, ChainCatcher According to ChainCatcher on July 24, dYdX, the leading decentralized derivatives trading platform, was revealed to be planning to sell the dYdX V3 trading software. However, within less than an hour after the news broke, the dYdX V3 website (dydx.exchange) was attacked by hackers. The hackers first took over the website and then implanted links pretending to be phishing websites. Once users authorized their information, they might face the possibility of having their assets or information stolen. As soon as the planned sale of V3 was revealed, its domain name was hacked, and the community speculated whether this was pure coincidence or a premeditated action. The sale and security crisis of dYdX triggered a series of chain reactions, with users and investors…







