Nillions comprehensive research report: A leader in blind computing across the two tracks of AI and privacy
This article comes from | Messari
Zusammengestellt von Odaily Planet Täglich ( @OdailyChine )
Übersetzer| Azuma ( @azuma_eth )
Editors Note: Earlier this week, the market was buzzing with a list of popular projects expected to hold TGE in the first quarter of this year. Nillion, the privacy computing leader that had raised $50 million, was among them.
In the following, investment research firm Messari analyzes Nillion in detail from multiple levels, including team, narrative, technology, architecture, token, ecology, roadmap, etc., which may help you further understand the information and dynamics of the project.
The following is the full text of Messari, translated by Odaily Planet Daily.

Core content overview
-
Nillion has established partnerships with companies/projects such as Virtuals, NEAR, Aptos, Arbitrum, Ritual, io.net, and Meta.
-
A complete set of application tools including nilAI, nilVM, nilDB and nilChain provide developers with resources to create privacy-preserving applications in areas such as artificial intelligence, healthcare and DeFi.
-
Nillion coordinates privacy-enhancing technologies (PETs) such as multi-party computation (MPC), homomorphic encryption, and zero-knowledge proofs to achieve secure data computation and storage on its decentralized infrastructure.
-
Nillions validator program has approximately 500,000 validators, who have processed a total of approximately 195 million ciphertexts and protected approximately 1,050 GB of data.
Vorwort
Processing high-value data (such as passwords, personalized AI, healthcare information, biometric information) has always been insecure and inefficient. Although encryption technology ensures the security of stored data, it needs to be decrypted and re-encrypted during calculations, which introduces vulnerabilities and delays. Although blockchain technology can decentralize transactions and data management, it does not inherently solve the problem of secure computing of encrypted data. This limitation restricts the types of applications that can be securely built in Web3.
Nillion hopes to address these limitations by performing data transmission, storage, and computation without decryption, thereby ensuring that sensitive information remains private and secure throughout its lifecycle. This approach, called Blind Compute, decentralizes trust and expands the use cases of decentralized networks to previously unexplored white space, such as private AI agents, private LLM inference, and other industries that require secure data. By using advanced privacy technologies (PETs) such as multi-party computation (MPC), fully homomorphic encryption (FHE), and trusted execution environments (TEEs), Nillion allows data to remain encrypted throughout the entire computation process.
Hintergrund
Founded in 2021, Nillion offers a novel approach to handling private data in distributed systems without compromising security or efficiency. Supported by application frameworks such as nilVM, nilDB, nilAI, and nilChain, Nillion provides developers with a variety of tools to help them build private applications in areas such as artificial intelligence, DeFi, and data storage.
Nillion team members include:
-
Alex Page (CEO), former Hedera SPV general partner and Goldman Sachs banker;
-
Andrew Masanto (CSO), co-founder of Hedera and founding CMO of Reserve;
-
Slava Rubin (CBO), founder of Indiegogo;
-
Dr. Miguel de Vega (Chief Scientist), PhD supervisor and author of more than 30 patents.
-
Conrad Whelan (founding CTO), founding engineer at Uber;
-
Mark McDermott (COO), former head of innovation at Nike;
-
Andrew Yeoh (CMO), an early senior partner at Hedera and former UBS and Rothschild banker, etc.
Since its founding, the team has raised $50 million in private funding from investors including Hack VC, Hashkey Capital, Distributed Global, and Maelstrom.
technology
The Nillion Network is a decentralized infrastructure designed to enable the processing of high-value data in a secure and private manner.
Nillion consists of two core layers: (i) the Coordination Layer, which is responsible for management and payments, and (ii) the Orchestration Layer (Petnet), which handles computation and storage. Nillion’s multi-party computation (MPC) protocol is at the core of the network’s functionality, allowing private data computation without revealing a single input. Nillion’s ecosystem is supported by a suite of application tools (nilAI, nilVM, nilDB, and nilChain) that help developers build privacy-focused applications. Academic research papers in Kryptography and privacy technologies validate Nillion’s technical feasibility.
Nillion Network
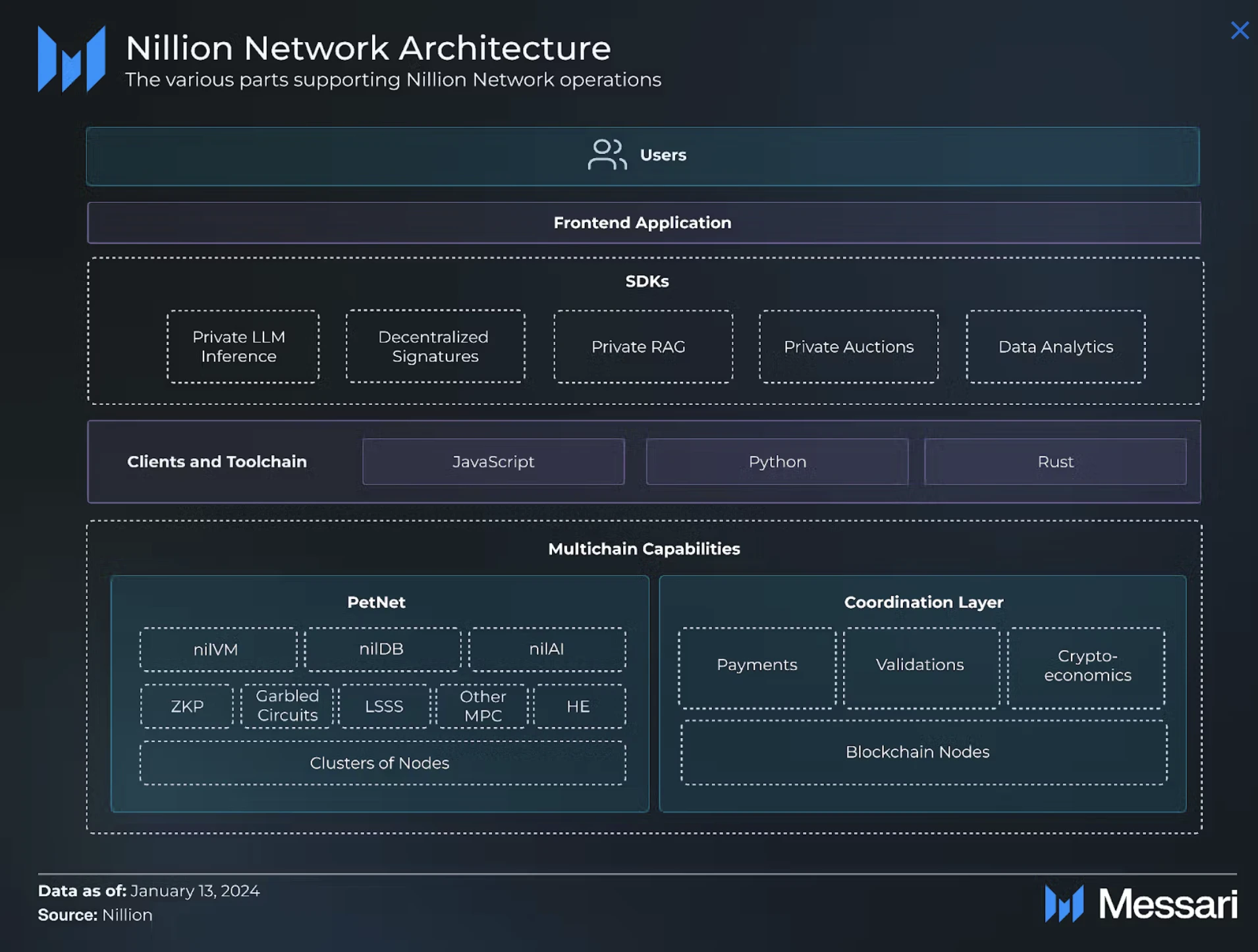
Nillion Network is a decentralized infrastructure designed to support private high-value data storage and computing. Nillion Networks scalability is achieved through clusters, which can configure groups of nodes to meet specific performance, security, and cost requirements. Unlike traditional blockchains, Nillion Network does not rely on a global shared state to operate, achieving vertical scalability (by upgrading a single node or cluster) and horizontal scalability (by adding new nodes or clusters) to effectively distribute workloads. The following is the contribution of each layer (i.e., the coordination layer and the orchestration layer) to the network architecture.
Coordination Layer
The coordination layer of the Nillion network (nilChain for short) is responsible for: (i) managing rewards; (ii) payments; (iii) cryptoeconomic security; and (iv) coordination between network clusters.
Specifically, nilChain is responsible for coordinating payments for storage operations and blind computations performed on the network, without handling computation directly. The coordination layer is built using the Cosmos SDK and supports IBC for interoperability; however, given the networks core focus on storage and computation, it does not currently support the execution of smart contracts. While directly accessible through Keplr or Leap wallets, applications built on the cooperating blockchain (which will be further explored in the Key Projects section) will be completely abstracted. nilChain is already running on testnet in June 2024.
Orchestration layer (Petnet)
Petnet aims to integrate cryptographic techniques such as multi-party computation (MPC), fully homomorphic encryption (FHE), and zero-knowledge proofs (ZKPs) to enable private computation and data management. This integration is achieved through two key components: (i) compiler and (ii) computation network. Specifically, the compiler simplifies the use of privacy-enhancing technologies (PET) by providing different levels of abstraction, while the computation network performs secure computation and manages encrypted data.
Nillion Network is implementing this approach through its Nada language compiler and nilVM, with elements of all four levels of abstraction already under development. The four levels of abstraction are as follows:
-
Each PET protocol runs independently in its own blind module, similar to an isolated black box. There is no built-in unified interface or abstraction, and all orchestration occurs on the client side; therefore, developers can use the application interface to perform specific tasks, but cannot integrate or customize it.
-
Various blind modules are integrated into each SDK, providing developers with a straightforward and unified way to manage multiple PET protocols without cryptography expertise. Although these modules are not yet fully optimized as they currently rely on a single PET protocol, they already allow for seamless, ready-to-use combinations of PET protocols.
-
Blind modules begin supporting multiple PET protocols within a single blind module. This provides developers with the ability to choose between various tradeoffs between performance and security — further simplifying the decision for developers with limited cryptographic knowledge.
-
Blind modules are deployed on loosely independent networks (called clusters) and managed by NilChain. As the Nillion blind computer matures, the same blind module can be replicated in multiple clusters, each with a different configuration. These configurations vary based on various factors (such as the number of nodes, node location, reputation, hardware specifications, security thresholds). This versatility allows developers to use the same functionality in different cluster setups, allowing solutions to be customized based on specific needs (such as security, cost, hardware, regulatory compliance, etc.).
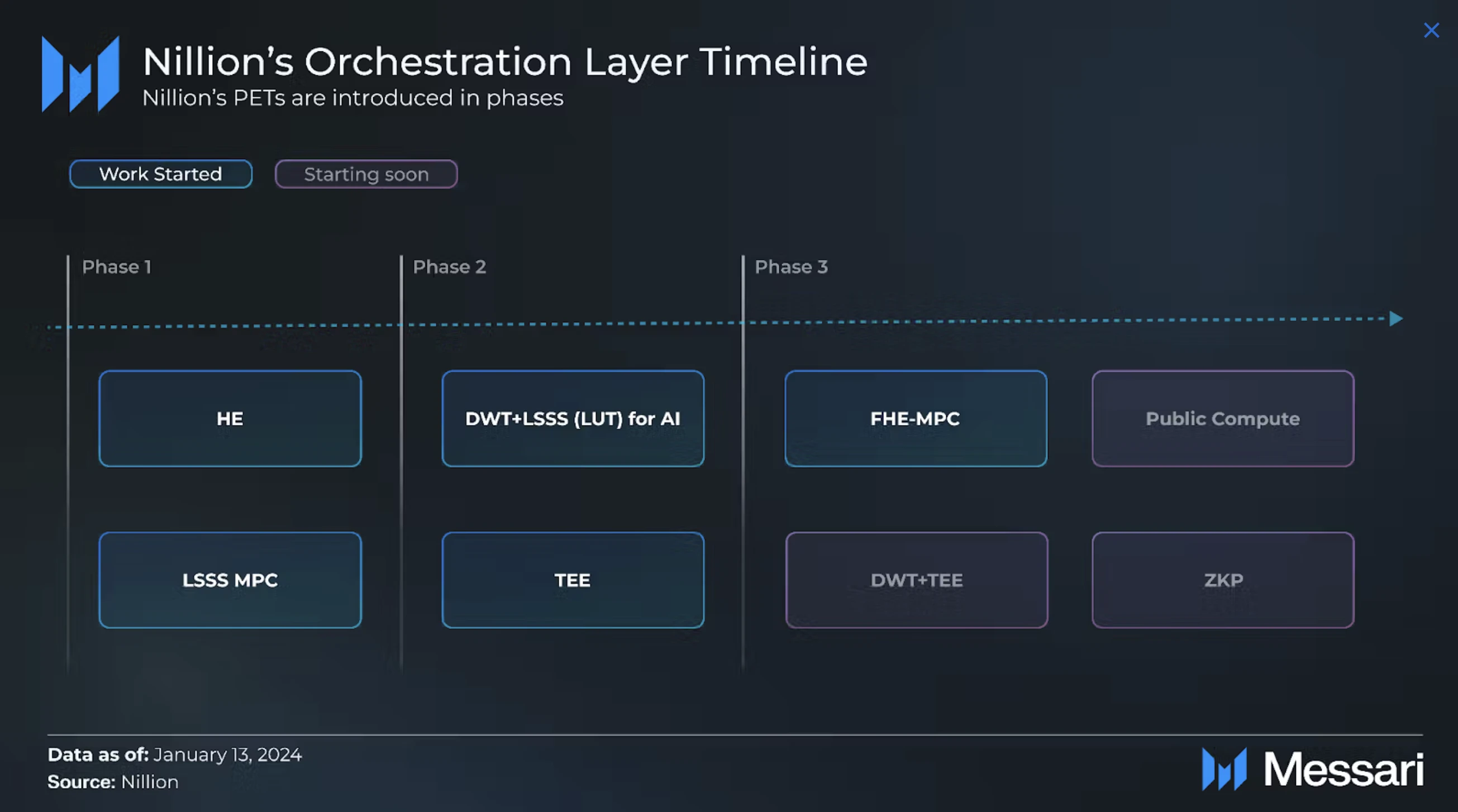
Nillions PET is introduced in phases, each phase passing through the four levels of abstraction mentioned above. Phase 1 (i.e., HE, LSSS MPC) and Phase 2 (i.e., DWT+LSSS, TEE) are progressing faster and have been integrated into the Nillion network. In Phase 3 technologies (i.e., FHE-MPC, DWT+TEE, public computing, ZKP), FHE-MPC has begun to make progress at the abstraction level.
Operation process
The following is a detailed breakdown of how the Nillion network components work:
-
Users/developers submit data to store or initiate blind computation requests through front-end applications built using JavaScript or Python clients.
-
Applications using JavaScript clients interact with Petnet for secure computation and encrypted data management, whereas Python-based applications interact with the coordination layer for payments, routing, and multi-chain communication.
The coordination layer processes payments using the native gas token of the corresponding blockchain or the NIL token.
-
After the coordination layer processes the request, it forwards the computing task to the Petnet containing the PET.
-
Petnet processes data using PETs such as linear secret sharing schemes, obfuscated circuits, and/or homomorphic encryption depending on the task requirements.
These computations will be performed on a cluster of nodes.
Each node in Petnet manages only a fragment (share) of the encrypted data.
-
The node performs a specified computation (such as addition, multiplication, or safe comparison) on the masked data and produces a partial output.
-
Petnet aggregates these partial outputs to produce the final computational result in a secure and confidential manner.
-
The final result is routed back as follows:
If using the JavaScript client, Petnet sends the results directly to the application for the user/developer to access.
If using the Python client, the coordination layer retrieves the results from the Petnet and routes them to the application or the relevant blockchain for further use.
-
For blockchain-integrated use cases, the coordination layer will pass the results to the original smart contract or decentralized application, allowing multi-chain functionality without requiring users to download new wallets.
Nillions MPC Complex Computing Protocol
Multi-party computation (MPC) is a subfield of cryptography that allows individuals to collaborate on computing the result of their combined data without revealing their individual inputs. Nillion developed an MPC protocol called Curl that is based on the Linear Secret Sharing Scheme (LSSS), but extends its capabilities to efficiently handle complex operations such as division, square roots, trigonometric functions, and logarithms. This makes Curl highly scalable and well suited for real-world problems, such as private AI agents, where the output is not linearly related to the input. Curl uses a structured two-stage workflow:
-
Phase 1 (Preprocessing to create shares): This phase generates random shares and distributes them to participants (computational entities) before processing the actual data using MPC technology. It is worth noting that the operations of the preprocessing phase are independent of the input value and only rely on the amount of input in order to create the appropriate number of shares before the calculation occurs. It can be seen as an abstraction layer – creating placeholders in advance, which are then combined with the actual input data provided by the user in Phase 2.
-
Phase 2 (Efficient Computation of Complex Operations): The computation phase involves the actual computation of the input private data through the following three phases: (i) input; (ii) evaluation; and (iii) output.
-
Input: Each party distributes its input to the participants, ensuring information theoretic security (ITS). Each participant gets a share for each input value, and the entire process remains confidential.
-
Evaluation: Parties use Nillions Curl protocol to efficiently compute complex operations on input shares.
-
Output: Local computation results are disclosed and aggregated to produce the final result.
To learn more about Nillion’s MPC mechanism, read the original academic paper Hier.
Application WerkzeugS
On top of the Nillion Network, application tools (i.e. nilVM, nilDB, nilAI, and the Nada integration package) provide developers with a modular framework and utilities to quickly build privacy-preserving, high-value data applications.
nilAI
nilAI is Nillion’s suite of privacy-focused AI technologies (i.e. AIVM, nada-AI, and nilTEE). Here’s how each technology works:
-
Artificial Intelligence Virtual Machine (AIVM): This is a secure AI inference platform based on Nillion’s MPC technology and Meta’s CrypTen framework. It uses Discrete Wavelet Transform (DWT) developed in conjunction with Meta’s AI research team to accelerate inference. AIVM ensures data privacy by keeping individual nodes invisible to user prompts and model outputs, thereby ensuring private deep learning model inference and deployment.
-
nada-AI: A library of nilVM designed for AI applications, providing a PyTorch-like interface for running small models such as neural networks (NN), convolutional neural networks (CNN), linear regression, etc. Developers can also use Google Colab to quickly bootstrap their projects.
-
nilTEE: This solution uses a trusted execution environment (TEE) to run large language models (LLMs) with high performance during inference. Nillion recommends limiting the use of TEE to inference time rather than long-term data storage. Nillion is currently conducting research to enhance nilTEE and AIVM by separating the inference setup to further improve security and performance.
nilVM, Nada and its libraries
nilVM is a virtual machine that allows developers to create programs using PET. Programs are written in Nada, Nillions Python-based open source DSL, and developed using the Nillion SDK. Nada also includes libraries such as nada-ai (similar to PyTorch and scikit-learn), nada-numpy, nada-data, and nada-test to simplify program development. Developers can integrate nilVM into their own applications using Python, Typescript, or CLI clients, and use the storage API for secure data storage and retrieval on the Nillion Network. Examples include joint learning programs, community development projects, and interactive demonstration use cases.
nilDB
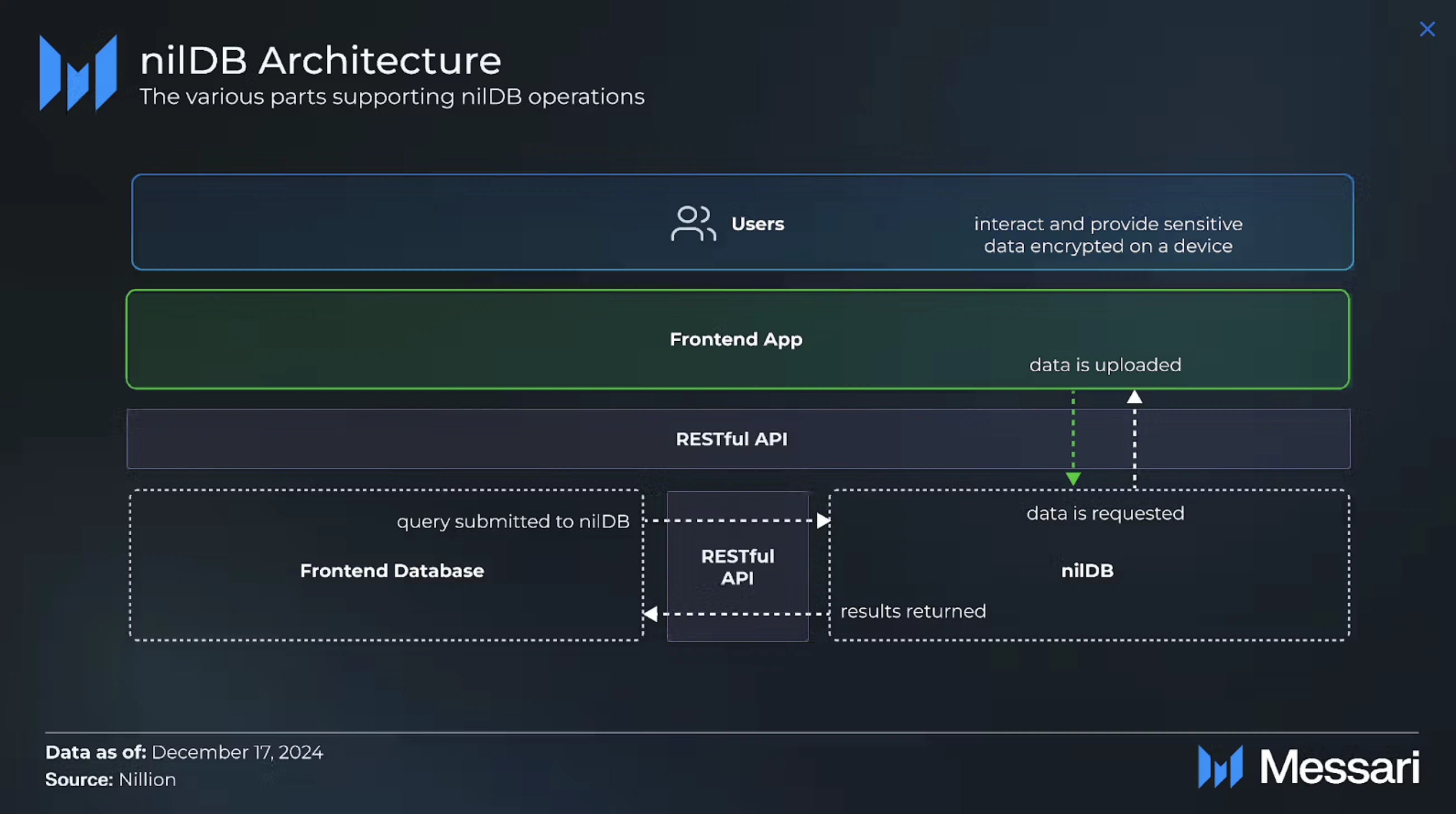
nilDB is an encrypted, distributed NoSQL database designed for privacy-preserving data storage and computation. Unlike ordinary NoSQL databases, nilDB distributes encrypted data as secret shares across multiple nodes, eliminating the reliance on central authorities. In addition, data owners can grant access to others to run SQL-like queries, computations, and privacy-preserving aggregations on stored data.
The specific operations are as follows:
-
Users encrypt sensitive data locally on their devices.
-
Users securely upload encrypted data through the Nillion-based front-end application. The application securely uploads the encrypted data to nilDB through the integrated back-end RESTful API.
-
The encrypted data is split into secret shares using Nillion’s MPC protocol and distributed across a cluster of nodes in the nilDB network. It is worth noting that no single node has the complete dataset.
-
Users provide explicit consent for specific data usage or querying and can withdraw consent at any time through the application.
-
Permitted entities (such as companies or third parties) submit SQL-like query requests (such as lookups, range filters, or aggregate calculations) through Nillions RESTful API.
-
Nodes in a nilDB cluster collaboratively perform computations on encrypted data without exposing sensitive information.
-
Query results, such as averages, sums, or filtered data sets, are generated while maintaining data confidentiality.
-
Only the final query results will be returned to the requesting user through the RESTful API.
-
For more information on the technical architecture, click Hier .
Nada Integration Package
The Nada language includes various integrated packages, including nada-AI (discussed earlier), nada-numpy, and nada-test. The use cases are as follows:
-
nada-numpy: A restricted adaptation of NumPy tailored for Nada DSL. Compared with ordinary NumPy, nada-numpy allows efficient manipulation of array structures and imposes strong typing requirements on data types to ensure compatibility with the strong typing characteristics of MPC.
-
nada-test: A testing framework for Nada programs that supports generating dynamic tests at runtime. Developers can write test cases in Python, integrate the framework into the pytest workflow, and define flexible input and output specifications.
Other tools (such as Nada DSL, Nada Sandbox, etc.) and SDKs can be viewed on GitHub .
NIL Zeichen
Token-Dienstprogramm
NIL tokens will play a variety of roles in the Nillion network, including
-
Pay for computing services, data storage, AI inference, and transaction fees for the Petnet and coordination layers. Specifically, developers can use NIL to access the privacy-preserving computing services provided by Nillion for their applications.
-
Stake and support network security and earn rewards.
Validators bind NIL to verify transactions and computations, ensuring the security of the coordination layer.
Petnet nodes stake NIL to increase the security of their cluster and attract developers and applications.
-
Participate in decentralized governance by proposing and voting on various network decisions such as protocol upgrades, resource allocation, and community grants programs.
Governance
Governance decisions are made through an on-chain voting mechanism. Specifically, any NIL token holder who meets the minimum token holding requirements can propose concepts to the network. Community committees or working groups established through previous governance actions can also submit proposals.
Voting rights apply to key decisions, e.g.
-
Introducing new features or updates.
-
Allocate reward pools for grants, developer rewards, and community-driven projects.
-
Adjust network pricing, validator requirements, or delegation limits.
-
Modify governance structures, such as quorum requirements or proposal thresholds.
-
Expand interoperability, establish strategic partnerships, or implement transparency and audit mechanisms.
-
Voting power is proportional to the amount of NIL staked, and stakers delegate voting power to validators while retaining the ability to vote on proposals themselves.
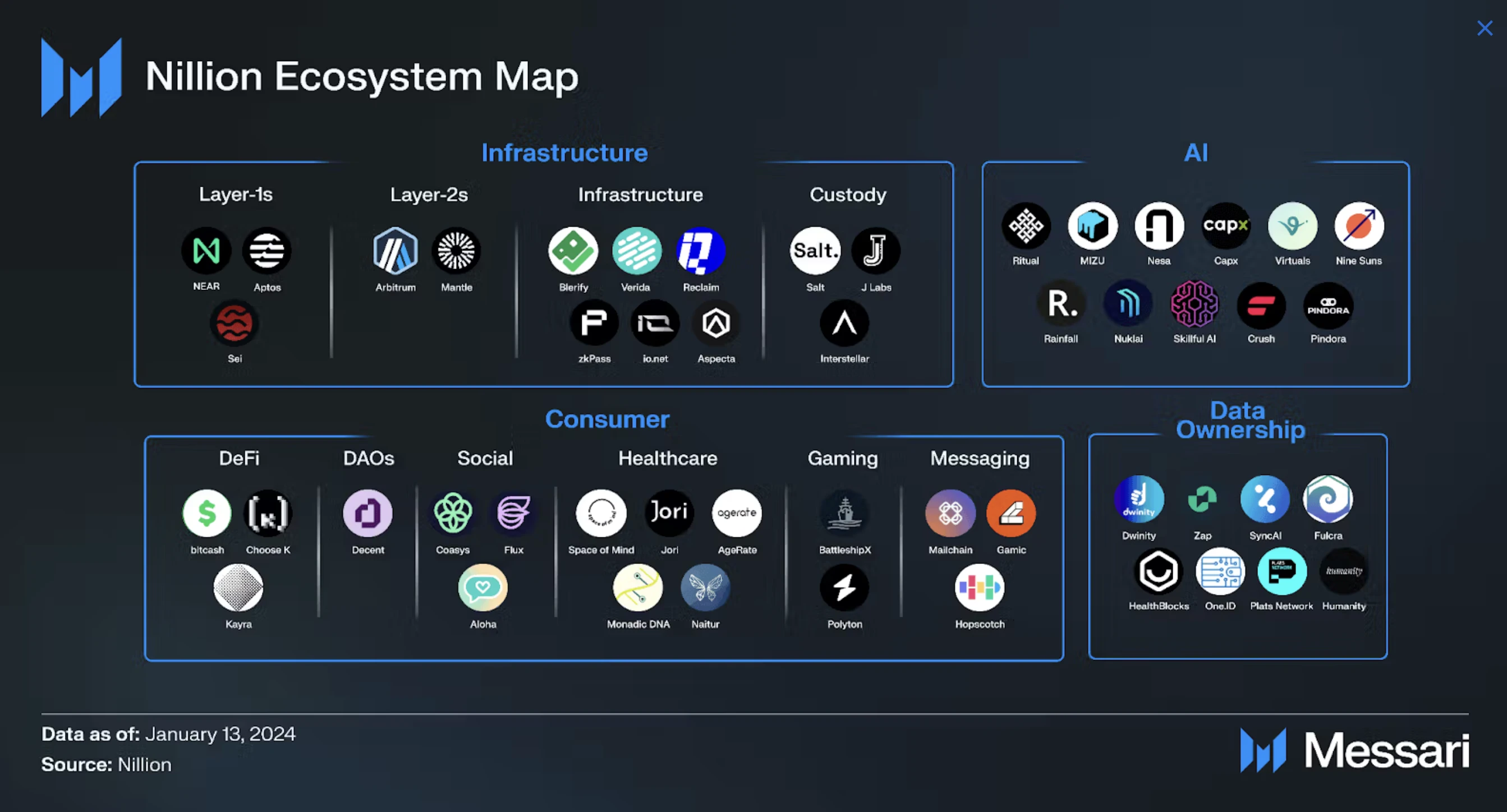
Nillion Ecosystem
Nillion can create new opportunities for the following industries:
-
Artificial Intelligence: Nillion processes data and inferences without exposing sensitive information, bridging the gap between secure local AI processing and the scalability of centralized, non-private AI systems.
-
Personalized agents: AI agents can store, compute, and process private data.
-
Privacy-focused model reasoning: AI models can securely process private data, minimize the risk of exposure to third parties, and achieve private LLM.
-
Privacy Knowledge Base and Search: Data can be stored in an encrypted form while still providing search capabilities for AI agents and other AI use cases.
-
Data Ownership: Nillion’s cryptographic infrastructure supports a secure data Marktplatz, allowing users to control and sell their own data to buyers.
-
Blockchain: Nillion allows blockchain applications to send blind storage and computing requests to the Nillion network, supplementing the public data function of the blockchain. It also supports on-chain settlement, allowing applications to decrypt relevant data on the blockchain.
-
Healthcare: Nillion enables privacy-preserving analytics of healthcare data across institutions and users.
-
DePIN: When integrated with Nillion, the DePIN project can securely store and process sensitive operational data.
Key Projects
-
Virtuals Protocol: An AI agent building platform that has developed a multimodal AI agent library and, by using Nillion, allows private training and inference of its AI models to build personalized AI agents.
-
Aptos/NEAR/Arbitrum/Sei: Layer 1 and Layer 2 blockchains that integrate blind data storage and computation to enhance data processing within smart contracts.
-
Ritual: An AI platform that builds a decentralized AI inference network, with Nillion integrated in its backend for private inference.
-
Zap: A data platform that aggregates user data into a decentralized data pool in Nillion, providing secure insights through blind computation and zero-knowledge transport layer security (zkTLS).
-
Reclaim Protocol: A zkTLS infrastructure platform that allows users to prove their identity and reputation through a trusted off-chain platform, and uses Nillion as the storage and processing platform for the generated proofs.
-
Healthblocks: A fitness app that uses Nillion to maintain user ownership and control of their data while allowing third parties to gain insight without exposing personal details.
-
MonadicDNA: A genomics platform that uses Nillion to encrypt data throughout its lifecycle, offering an alternative to centralized providers like 23andMe .
Roadmap
The Nillion roadmap was released on May 31, 2024 and is divided into four key phases:
-
Phase 1 – Genesis Sprint (Completed). This phase established: (i) the base coordination layer during the testnet launch; (ii) tested core functionality such as Keplr wallet creation, token transfers, staking, and management; (iii) provided developers with access to the Nillion SDK, which has telemetry capabilities for early application development; and (iv) conducted load testing to evaluate transaction throughput and network scalability.
-
Phase 2 – Catalyst Fusion (in progress). This phase: (i) integrates Petnet with the coordination layer; (ii) joins external nodes to achieve full decentralization; (iii) introduces blind applications for secure data processing; (iv) supports cross-chain functionality, expanding Nillion into a multi-chain ecosystem.
-
Phase 3 — Hardening. This phase will: (i) include the mainnet launch and token generation event (TGE); (ii) run external nodes; (iii) enable real-world interactions through blind computation; and (iv) validate previously built applications on the network under live conditions.
-
Phase 4 — The multi-cluster future. This phase will: (i) enable horizontal expansion by adding public node clusters; (ii) increase computing power; (iii) optimize the network for applications in specific markets; and (iv) achieve scalability while maintaining security and privacy.
Abschluss
Nillion is a decentralized infrastructure designed to handle high-value, privacy-sensitive data in a variety of applications from AI agents to privacy DeFi. Nillion combines advanced PETs (such as MPC, FHE, TEE) to expand the usability of decentralized networks and the possibilities of decentralized applications. Nillions architecture – coordination layer and Petnet – supports scalability through clustering while ensuring data confidentiality and decentralized trust.
The Nillion ecosystem continues to expand, with milestones including: (i) the Nucleus Builder Program (supporting ~50 projects across multiple verticals) and (ii) ~500,000 validators participating, collectively processing ~195M secrets and protecting ~1,050GB of data. Partnerships with Virtuals, NEAR, Meta, and Aptos, as well as ongoing mainnet launch and multi-cluster scalability roadmap development, highlight Nillion’s progress in advancing privacy-focused data management and secure computation.
This article is sourced from the internet: Nillions comprehensive research report: A leader in blind computing across the two tracks of AI and privacy
Related: Memecoin: a product of jokes, with a market value of hundreds of billions
TL;DR 1. As the dust settled on the US election, Bitcoin successfully broke through 100,000 US dollars, and Meme ushered in the Sunmmer season; 2. Memecoin was not originally created for speculation. The birth of DOGE is the original intention of Meme: straightforward, humorous and grassroots, and most of it is invested in charity; 3. A new trend is that Memecoin is gradually becoming a vehicle for expressing support and belief; 4. At this stage, with the continuous improvement of infrastructure, Memecoin has shown a new two-sidedness while its number has increased dramatically; 5. Memecoin is a complex investment that requires comprehensive consideration of narrative, community, marketing, risk, market performance and smart money. introduction An animal image, an emoticon, an ICON, although Meme in the Internet age is already everywhere,…







